Differences between a domain and a workgroup. How to create a working group in a computer network
We have repeatedly mentioned working groups and domains. Let's take a look at how these two models of networking in Microsoft networks are fundamentally different.
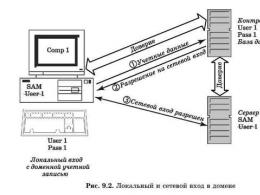
Working group is a logical grouping of computers united by a common name to facilitate navigation within a network. It is crucial that each computer in the workgroup equal(i.e., the network turns out to be peer-to-peer) and maintains its own local database of user accounts (Security Accounts Manager, SAM).
This is the main problem that does not allow the use of workgroups in large corporate networks. Indeed, if we recall that logging into a protected system is mandatory, and direct and network logins are fundamentally different (direct login is controlled by the local computer, and network login is remote), then, for example, a user who logged into Comp1 computer under the local account User1, will be denied access to the printer installed on the Comp2 computer, since there is no user named User1 in its local database (Fig. 9.1). Thus, in order to ensure "transparent" interaction in the working group, it is necessary create the same accounts with the same passwords on all computers, where users work and resources are located.
Windows XP Professional for Workgroups has a special mode called "Use Simple File Sharing" to work around this problem (this mode is enabled by default). In this case, the connection to any network computer is carried out on behalf of its local guest account, which is enabled using Network setup wizards(it is disabled by default) and for which the desired access level is configured.
For Windows XP Home Edition, this method of network communication is the main one and cannot be disabled (therefore, computers with this OS cannot be made domain members).
It is clear that you can manage accounts and resources in a workgroup only with a small number of computers and users. Large networks should use domains.
Domain is a logical grouping of computers connected common database of users and computers, security and management policy.
Domains are created based on Windows network OS, and the database, as we said, is supported domain controllers. What is important in domains is that all computers here do not themselves check users at login, but delegate this procedure to controllers (Fig. 9.2). This organization of access makes it easy to carry out a one-time user check when logging on to the network, and then, without checking, grant him access to the resources of all computers in the domain.

» domains and workgroups - what is it
The Windows Server 2003 operating system and classic Windows NT use two terms that are unrelated but often confuse
administrators: "domains" and "workgroups". Here is how these terms are defined.
- The domain is an element of the security system. Domain members pass
authentication using special servers called domain controllers. - The working group is an element of the resource allocation system. Working group members find each other using special servers called browsers.
All those who, like me, lived through the Cold War will understand where the source of this confusion lies. Remember Khrushchev or Brezhnev? Each of them had unlimited power in the USSR, since each of them held two posts - the Chairman of the Supreme Soviet and the General Secretary of the Communist Party. Similarly, the Primary Domain Controller (PDC) makes domains and workgroups look like each other because the PDC stores both the security database and the browser database.
Using Workgroups
If you are installing a server that does not need to communicate with other servers, you can make it a standalone server - a member of a workgroup. Clients in the same workgroup on the same IP subnet use the same browser to find the server. Users will be authenticated using a local SAM database on the server each time they connect over the network.
Even with a domain, it sometimes makes sense to set up isolated servers. For example, such a server could be installed within a DMZ where computers are not required to relay registration information back through the firewall.
Joining a domain
If the authentication database on the server is not strong enough, the server must be joined to a domain. The server then becomes a member of the domain. Active Directory domain members authenticate users using the Kerberos protocol. This allows you to achieve a high level of security and get a fast authentication mechanism. In addition, this authentication mechanism contains the authorization information needed to create the user's local security context.
Members of a classic Windows NT domain authenticate users using the NT LanMan Challenge-Response protocol. This requires the server to have a direct link to the backup domain controller.
On Windows NT, adding a computer to a domain required providing administrator credentials. In the Windows Server 2003 (and Windows 2000) operating system, any authenticated user can add a computer to a domain. The ability to add computers to a domain is determined by Group Policy for the Domain Controllers Organization Unit in Active Directory. By modifying this Group Policy, you can restrict the users who are allowed to add computers to the domain.
Working group is a logical grouping of computers united by a common name to make it easier for computers to navigate within a network.
It is fundamentally important that everyone in the workgroup is equal (i.e., the network turns out to be peer-to-peer) and maintains its own local database of user accounts (Security Accounts Manager, SAM).
This is the main problem that does not allow the use of workgroups in large corporate networks.
Indeed, logging into a secure system is mandatory, and direct and network logins are fundamentally different (direct login is controlled by the local computer, and network login is remote), then, for example, a user logged into Comp1 computer under the local account User1 will be denied access to the printer installed on the Comp2 computer, since there is no user named Userl in its local database (Fig. 1).

Rice. 1 Working groups and domains
Thus, to ensure "transparent" interaction in the workgroup, you need to create the same accounts with the same passwords on all computers where users work and resources are located.
Windows OS for workgroups has a special mode: "Use simple file sharing", which allows you to bypass the indicated problem (this mode is enabled by default).
In this case, connection to any network computer is carried out on behalf of its local guest account, which is enabled using the Network Configuration Wizard (it is disabled by default) and for which the required access level is configured.
For Windows Home Edition, this method of networking is the main one and cannot be disabled (therefore, computers running this OS cannot be made members of a domain).
It is clear that you can manage accounts and resources in a workgroup only with a small number of computers and users.
Large networks should use domains.
Domain is a logical grouping of computers united by a common database of users and computers, a security and management policy.
Domains are created based on the Windows network operating system, and the database is maintained by domain controllers.
It is important in domains that all computers here do not themselves check users at the entrance, but delegate this procedure to controllers.
This organization of access makes it easy to carry out a one-time user check when logging on to the network, and then, without checking, grant him access to the resources of all computers in the domain.

Rice. 2 Domains
The main threats when working on the network
There are quite a few threats waiting for users when connecting a computer to the network:
- "hacking" a computer is usually done in order to seize control of the operating system and gain access to data;
- damage to the system is most often organized to disrupt the performance (cause a denial of service - “Denial of Service”) of any services or a computer (usually a server) as a whole, and sometimes even the entire network infrastructure of an organization;
Basic security measures when working on a network
They can be formulated as the following set of rules:
- turn off your computer when you are not using it. As computer security experts like to say, “the most secure is a computer that is turned off and stored in a bank vault”;
- keep your operating system up to date. In any OS, so-called “vulnerabilities” are periodically discovered that reduce the security of your computer. The presence of vulnerabilities must be carefully monitored (including by reading the “computer” press or information on the Internet) in order to take timely measures to eliminate them.
- data theft due to incorrectly set access rights, when transferring data or “hacking” the system, allows access to protected, often confidential information with all the ensuing unpleasant consequences for the owner of this data;
- data destruction is intended to disrupt or even paralyze systems, computers, servers, or an entire organization.
- use a limited set of well-tested applications, do not install or allow others to install on your computer programs taken from unverified sources (especially from the Internet). If the app is no longer needed, delete it;
- Don't share your computer's resources unnecessarily. If this is still required, be sure to configure the minimum required level of access to the resource only for registered accounts;
- install (or enable) a personal firewall (firewall) on your computer. If we are talking about corporate networks, install firewalls both on the routers connecting your local network to the Internet, and on all computers on the network;
- even if you are the sole owner of the computer, use a user account for normal work: in this case, damage to the system, for example, when infected with a virus, will be immeasurably less than if you worked with administrator rights. For all accounts, especially administrative ones, set and remember strong passwords.
A password is considered complex if it contains a random combination of letters, numbers, and special characters, such as jxglrg$N. Of course, the password must not be the same as your account name. On Windows operating systems, a complex password can be generated automatically using the NET USER command with the /RANDOM switch, for example:
NET USER UserName /RANDOM
- When working with e-mail, never immediately open attachments, especially those from unknown senders. Save the attachment to disk, check it with an antivirus program, and only then open it. If possible, enable protection against potentially dangerous content in your email program and disable HTML support;
- when working with websites, take reasonable precautions: try to avoid registration, do not share personal information about yourself with anyone, and carefully work with online stores and other services that use online payment methods using credit cards or systems such as WebMoney, Yandex-Money etc.
- Two models are used to organize work in Microsoft networks: workgroups, used with a small number of computers, and domains, which make it easy to combine a large number of users, workstations, and servers.
- All network operating systems and data stored on computers must be reliably protected, and it is desirable that the security system used be multi-level.
All computers are network peers; neither computer can control the other.
Each computer has multiple user accounts. To log on to any computer that belongs to a workgroup, you must have an account on that computer.
A workgroup usually has no more than twenty computers.
The workgroup is not password protected.
All computers must be on the same local network or subnet.
In the home group:
Computers on a home network must belong to a workgroup, but they can also be members of a homegroup. With a homegroup, it's much easier to share pictures, music, videos, documents, and printers with others.
The HomeGroup is password protected, but you only enter it once when you add a computer to the HomeGroup.
In the domain:
One or more computers are servers. Network administrators use servers to control security and permissions for all computers in a domain. This makes it easy to change settings, as changes are automatically made to all computers. Domain users must provide a password or other credentials each time they access the domain.
If the user has an account in the domain, he can log on to any computer. This does not require you to have an account on the computer itself.
The rights to change computer settings can be limited because network administrators want to ensure that computer settings are consistent.
There can be thousands of computers in a domain.
Computers can belong to different local networks.
Domains and working groups can be present in the structure of computer networks. What are they?
What is a domain?
Under domain it is customary to understand a fairly large group of computers united in one LAN or through several connected LANs, as well as having access to a wide range of different resources and network interfaces (allowing you to organize the exchange of files, streams, arrays, and share access to them).
The main features of domains are as follows:
- the structure of domains provides for dedicated servers that perform the main computing functions and are designed to manage network resources;
- management of access settings for computers in certain parts of the network included in the domain can be carried out centrally - with the help of servers;
- a user with a login that is bound to a domain (or access rights) can connect to the network from any PC that interacts with the corresponding domain.
A domain can have a huge number of computers - a common thing if there are thousands of them. At the same time, their individual groups may belong to different LANs, and, despite this, the domain will be functional.
Domain-hosted servers tend to be significantly more powerful than the average domain-joined PC. Any of those operating systems that are optimal for solving specific problems set by the domain owner can be installed on them - and it can differ significantly from that installed on non-server PCs.
When using VPN standards and similar standards, locally formed domains can be connected by users from virtually any other networks that physically have access to the relevant resources. The Internet works according to this principle - when a large number of PCs located in different countries of the world can, by connecting to a specific domain, receive various resources from it.
What is a working group?
Under working group It is customary to understand a relatively small-scale computer network, created mainly in order to provide shared access to various files for the PCs included in it (however, it remains in principle possible to exchange the corresponding files).
Working groups are characterized by the following features:
- all PCs included in the workgroup are most often united in a peer-to-peer network (there are no dedicated servers in it, and, as a rule, there is no way to manage key resources of other computers or the network as a whole using one PC);
- access to the corresponding network is usually possible only if the PC operating system is loaded from a specific login (user account) for which this access is open and configured.
The size of a working group usually does not exceed a few dozen PCs. It is important that all of them be combined within a common LAN or subnet - so that the corresponding infrastructure is sufficiently stable.
Comparison
The main difference between a domain and a workgroup is how resource management is implemented in the network infrastructure of the first and second types. So, for home networks, where particularly intensive data exchange is not expected, the use of workgroups is typical. In corporate (for which such tasks are typical), as a rule, domains are involved. The interaction of computers in large-scale networks - such as the Internet - is almost always carried out using domains.
A working group is usually much easier to form than a domain. The interfaces of modern operating systems allow even an inexperienced user to solve this problem. All you need to do is connect the PC physically using a cable or switch (as an option - wirelessly, via Wi-Fi), as well as configure the network infrastructure using the built-in software of the operating system.
Creating a domain is usually a more complicated procedure. It assumes, first of all, the availability of servers with sufficient performance, their detailed configuration, and possibly the installation of a suitable network operating system. It will also be necessary to implement in the infrastructure of the domain the function of authenticating the rights of those users who connect to the network.
The security of computers included in the workgroup, as a rule, is implemented by installing anti-virus software and other auxiliary programs on each of them. In the case of a domain, PC security can also be implemented by installing intranet interfaces that allow monitoring various threats and preventing their spread over the network.
Domains are usually much easier to scale, providing more and more new users to connect to them (including those outside the local network where the main domain server is located, or via the Internet). All that is needed is to provide new users with the information necessary for authorization in the domain, or configure its servers so that they recognize and connect certain user groups automatically.
In turn, adding a new user to a workgroup is usually a more time-consuming procedure. You may need to configure each of the connecting computers separately, determine the access rights for the respective PCs, and verify the effectiveness of the anti-virus and other auxiliary software that is installed on them.
Having determined the difference between a domain and a workgroup, let's record the findings in a small table.
table
| Domain | Working group |
| What do they have in common? | |
| Domains and workgroups are designed to provide communication between different PCs for the purpose of exchanging data, as well as sharing access to them | |
| What is the difference between them? | |
| It is a large-scale computer network (or a group of interacting LANs) controlled centrally using servers | It is usually a relatively small number of connected PCs peer-to-peer LAN without servers |
| Allows for less labor-intensive, faster infrastructure scaling (which makes it possible to form networks on a global scale) | Assumes slower scaling - due to the fact that connecting each new PC to the network, as a rule, requires detailed configuration |
| Allows you to implement intranet solutions aimed at improving the security of data exchange between PCs within a domain | It involves the installation on each PC of the working group of programs necessary to ensure secure data exchange |
| A user with the required credentials or access can log into the domain from any PC | The user can connect to the workgroup, as a rule, only from a specific PC under a specific account |