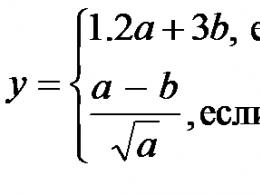Digital subscriber lines isdn. Last Mile Using Wireless Local Loop General Transport Network Development Trends
Send your good work in the knowledge base is simple. Use the form below
Students, graduate students, young scientists who use the knowledge base in their studies and work will be very grateful to you.
Posted on http:// www. all best. en/
Final qualifying work
Subject: Subscriber Access Network
Introduction
One of the most important problems of telecommunication networks continues to be the problem of subscriber access to network services. The urgency of this problem is determined primarily by the rapid development of the Internet, access to which requires a sharp increase in the bandwidth of subscriber access networks. The main means of the access network, despite the emergence of new most modern wireless methods of subscriber access, are traditional copper subscriber pairs. At the same time, networks of high-speed subscriber access based on fiber-optic communication technologies have been widely developed recently. Their distinctive feature is:
* absence of harmful electromagnetic radiation;
* the signal is not distorted by electromagnetic and radio frequency interference (optical cable is absolutely immune to the effects of high voltage, electromagnetic interference);
* fiber optic cable is lighter;
* has a much greater bandwidth than conventional copper, which means that fiber can transmit much more information in the same time;
* low attenuation of the light signal;
* protection against unauthorized access, etc.
Optical lines are much cheaper to build and operate than copper lines, so as the volume of optical services grows, prices should come down.
The purpose of the diploma project is to develop a project for a high-speed subscriber access network based on fiber optic communication technologies using computer-aided design tools.
To achieve the goal of the graduation project, the following tasks were set:
analyze methodological and theoretical materials on the basics of local and telecommunication networks;
to study the features and structure of local and telecommunication networks of subscriber access;
explore the stages of network design, as well as the tools and methods used for network design and reasonably choose the tools to achieve the goal of the graduation project;
develop a project for a subscriber access network using the selected design tool.
The practical significance of the graduation project lies in the development of a subscriber access network project using design tools and methods and the further implementation of this project on real objects.
The structure of the graduation project is subject to the logic of solving the tasks. The first chapter of the graduation project will present the theoretical foundations of data transmission networks. The second chapter will provide an overview of network technologies. The third chapter is devoted to design: it will present the main design stages, the development of a subscriber access network project in accordance with the assignment for a graduation project, and the choice of tools for project development. The fourth chapter will present the organizational and economic part. In the fifth chapter, we will talk about life safety.
1. Overview of data networks
1.1 Definition of local networks
Recently, many methods and means of information exchange have been proposed: from the simplest transfer of files using a floppy disk to the worldwide computer network Internet, which can unite all the computers in the world. What is the place in this hierarchy given to local networks?
Most often, the term "local networks" or "local area networks" (LAN, Local Area Network) is understood literally, that is, these are networks that are small, local in size, connect closely spaced computers. However, it is enough to look at the characteristics of some modern local networks to understand that such a definition is not accurate. For example, some local networks easily provide communication over a distance of several tens of kilometers. This is not the size of a room, not a building, not closely spaced buildings, and maybe even the whole city. On the other hand, computers located on neighboring tables in the same room may well communicate over a global network (WAN, Wide Area Network or GAN, Global Area Network), but for some reason no one calls it a local network. Nearby computers can also communicate using a cable connecting external interface connectors (RS232-C, Centronics) or even without a cable via infrared (IrDA) . But for some reason such a connection is also not called local.
The definition of a local network as a small network that unites a small number of computers is incorrect and quite common. Indeed, as a rule, a local network connects from two to several dozen computers. But the limiting capabilities of modern local networks are much higher: the maximum number of subscribers can reach a thousand. It is wrong to call such a network small.
Some authors define a local area network as "a system for connecting many computers directly". This implies that information is transmitted from computer to computer without any intermediaries and through a single transmission medium. However, it is not necessary to talk about a single transmission medium in a modern local area network. For example, within the same network, both electrical cables of various types (twisted pair, coaxial cable) and fiber optic cables can be used. The definition of transmission "without intermediaries" is also not correct, because modern local networks use repeaters, transceivers, hubs, switches, routers, bridges, which sometimes perform quite complex processing of transmitted information. It is not entirely clear whether they can be considered intermediaries or not, whether such a network can be considered a local one.
Probably, it would be most accurate to define it as a local area network that allows users to ignore the connection. You can also say that the local network should provide transparent communication. In fact, computers connected by a local network are combined into one virtual computer, the resources of which can be accessed by all users, and this access is no less convenient than to the resources included directly in each individual computer. Convenience in this case refers to a high real speed of access, the speed of information exchange between applications, which is almost imperceptible to the user. With this definition, it becomes clear that neither slow WANs nor slow communication through serial or parallel ports fall under the concept of a local area network.
From this definition, it follows that the speed of transmission over a local network must necessarily increase as the speed of the most common computers increases. This is exactly what is observed: if ten years ago an exchange rate of 10 Mbps was considered quite acceptable, now a network with a bandwidth of 100 Mbps is already considered medium-speed, they are actively developed, and in some places funds are used for a speed of 1000 Mbps. with and even more. Without this, it is no longer possible, otherwise the connection will become too bottleneck, it will excessively slow down the work of a networked virtual computer, and reduce the convenience of access to network resources.
Thus, the main difference between a local network and any other is the high speed of information transfer over the network. But that's not all, other factors are equally important.
In particular, a low level of transmission errors caused by both internal and external factors is essential. After all, even very quickly transmitted information, which is distorted by errors, simply does not make sense, it will have to be transmitted again. Therefore, local networks necessarily use specially laid high-quality and well-protected communication lines.
Of particular importance is such a characteristic of the network as the ability to work with heavy loads, that is, with high exchange intensity (or, as they say, with high traffic). After all, if the exchange control mechanism used in the network is not very effective, then computers can wait a long time for their turn to transmit. And even if this transfer is then carried out at the highest speed and error-free, such a delay in access to all network resources is unacceptable for a network user. He doesn't care why he has to wait.
The exchange control mechanism can be guaranteed to work successfully only if it is known in advance how many computers (or, as they say, subscribers, nodes) can be connected to the network. Otherwise, you can always turn on so many subscribers that, due to overload, any control mechanism will stall. Finally, a network can only be called a data transmission system that allows you to combine up to several dozen computers, but not two, as in the case of communication through standard ports.
Thus, the distinctive features of a local network can be formulated as follows:
high speed of information transfer, large network bandwidth. Acceptable speed now is at least 100 Mbps;
low level of transmission errors (or, equivalently, high-quality communication channels). The allowable probability of data transmission errors should be of the order of 10-8 -- 10-12;
efficient, high-speed network exchange control mechanism;
a predetermined number of computers connected to the network.
With this definition, it is clear that global networks differ from local networks primarily in that they are designed for an unlimited number of subscribers. In addition, they use (or can use) not very high-quality communication channels and a relatively low transmission rate. And the exchange control mechanism in them cannot be guaranteed to be fast. In global networks, it is not the quality of communication that is much more important, but the very fact of its existence.
Another class of computer networks is often distinguished - urban, regional networks (MAN, Metropolitan Area Network), which are usually closer in their characteristics to global networks, although sometimes they still have some features of local networks, for example, high-quality communication channels and relatively high transmission speed. In principle, a city network can be local with all its advantages.
True, now it is no longer possible to draw a clear line between local and global networks. Most local networks have access to the global. But the nature of the transmitted information, the principles of organizing the exchange, the modes of access to resources within the local network, as a rule, are very different from those accepted in the global network. And although all computers on the local network in this case are also included in the global network, this does not negate the specifics of the local network. The ability to access the global network remains just one of the resources shared by users of the local network.
A wide variety of digital information can be transmitted over a local area network: data, images, telephone conversations, emails, etc. By the way, it is the task of transmitting images, especially full-color dynamic ones, that makes the highest demands on network speed. Most often, local area networks are used to share (share) resources such as disk space, printers, and access to the global network, but this is only a small part of the possibilities that LANs provide. For example, they allow the exchange of information between different types of computers. Full-fledged subscribers (nodes) of the network can be not only computers, but also other devices, for example, printers, plotters, scanners. Local networks also make it possible to organize a system of parallel computing on all computers in the network, which greatly speeds up the solution of complex mathematical problems. With their help, as already mentioned, it is possible to control the operation of a technological system or a research facility from several computers simultaneously.
However, networks also have quite significant drawbacks, which should always be remembered:
the network requires additional, sometimes significant material costs for the purchase of network equipment, software, for laying connecting cables and training personnel;
the network requires the hiring of a specialist (network administrator) who will be responsible for monitoring the operation of the network, upgrading it, managing access to resources, troubleshooting, protecting information and backing up (for large networks, a whole team of administrators may be needed);
the network restricts the ability to move computers connected to it, as this may require relocation of connecting cables;
networks are an excellent environment for the spread of computer viruses, therefore, much more attention will have to be paid to protection against them than in the case of autonomous use of computers, because it is enough to infect one, and all computers on the network will be affected;
the network dramatically increases the risk of unauthorized access to information with the aim of stealing or destroying it; information protection requires a whole range of technical and organizational measures.
Here we should also mention such important concepts of network theory as subscriber, server, client.
A subscriber (node, host, station) is a device connected to the network and actively participating in information exchange. Most often, the subscriber (node) of the network is a computer, but the subscriber can also be, for example, a network printer or other peripheral device that can connect directly to the network. Hereinafter, instead of the term "subscriber", for simplicity, the term "computer" will be used.
A server is a network subscriber (node) that provides its resources to other subscribers, but does not use their resources itself. Thus, it serves the network. There can be several servers in the network, and it is not at all necessary that the server is the most powerful computer. A dedicated server is a server that only handles network tasks. A non-dedicated server can perform other tasks in addition to network maintenance. A specific type of server is a network printer.
A client is a network subscriber who only uses network resources, but does not give his own resources to the network, that is, the network serves him, and he only uses it. The client computer is also often referred to as the workstation. In principle, each computer can be both a client and a server at the same time.
Server and client are also often understood not as computers themselves, but as software applications running on them. In this case, the application that only sends the resource to the network is the server, and the application that only uses network resources is the client.
1.2 Types of communication network lines
The information transmission medium is those communication lines (or communication channels) through which information is exchanged between computers. The vast majority of computer networks (especially local ones) use wired or cable communication channels, although there are also wireless networks that are now increasingly used, especially in portable computers.
Information in networks is most often transmitted in a serial code, that is, bit by bit. This transfer is slower and more complicated than using parallel code. However, it should be taken into account that with faster parallel transmission (through several cables at the same time), the number of connecting cables increases by a factor equal to the number of bits of the parallel code (for example, 8 times with an 8-bit code). This is not at all a trifle, as it might seem at first glance. With significant distances between network subscribers, the cost of a cable is quite comparable to the cost of computers and may even exceed it. In addition, laying one cable (less often two multidirectional) is much easier than 8, 16 or 32. Finding damage and repairing the cable will also be much cheaper.
But that is not all. Transmission over long distances with any type of cable requires complex transmitting and receiving equipment, since it is necessary to generate a strong signal at the transmitting end and detect a weak signal at the receiving end. With serial transmission, this requires only one transmitter and one receiver. With parallel, the number of required transmitters and receivers increases in proportion to the bit depth of the parallel code used. In this regard, even if a network of insignificant length (on the order of ten meters) is being developed, serial transmission is most often chosen.
In addition, with parallel transmission it is extremely important that the lengths of the individual cables are exactly equal to each other. Otherwise, as a result of passing through cables of different lengths, a time shift is formed between the signals at the receiving end, which can lead to malfunctions or even to the complete inoperability of the network. For example, at a transmission rate of 100 Mbps and a bit duration of 10 ns, this time shift should not exceed 5–10 ns. This amount of shift gives a difference in cable lengths of 1-2 meters. With a cable length of 1000 meters, this is 0.1-0.2%.
It should be noted that in some high-speed local networks, parallel transmission over 2-4 cables is still used, which makes it possible to use cheaper cables with a lower bandwidth at a given transmission rate. But the permissible cable length does not exceed hundreds of meters. An example is the 100BASE-T4 segment of a Fast Ethernet network.
The industry produces a huge number of types of cables, for example, only one largest cable company Belden offers more than 2000 of their names. But all cables can be divided into three large groups:
electrical (copper) cables based on twisted pairs of wires (twisted pair), which are divided into shielded (shielded twisted pair, STP) and unshielded (unshielded twisted pair, UTP);
electrical (copper) coaxial cables (coaxial cable);
fiber optic cables (fiber optic).
Each type of cable has its own advantages and disadvantages, so when choosing it is necessary to take into account both the features of the problem being solved and the features of a particular network, including the topology used.
We can distinguish the following main parameters of cables, which are fundamentally important for use in local networks:
cable bandwidth (frequency range of signals transmitted by the cable) and signal attenuation in the cable; these two parameters are closely related to each other, since with increasing signal frequency, signal attenuation increases; it is necessary to choose a cable that has acceptable attenuation at a given signal frequency; or it is necessary to choose a signal frequency at which attenuation is still acceptable; attenuation is measured in decibels and is proportional to the length of the cable;
noise immunity of the cable and the secrecy of information transmission provided by it; these two interrelated parameters show how the cable interacts with the environment, that is, how it reacts to external interference, and how easy it is to listen to information transmitted over the cable;
speed of signal propagation along the cable or, inverse parameter - signal delay per meter of cable length; this parameter is of fundamental importance when choosing the length of the network; typical values of the speed of signal propagation - from 0.6 to 0.8 of the speed of propagation of light in vacuum; respectively, typical delays are from 4 to 5 ns/m;
for electric cables, the value of the wave impedance of the cable is very important; wave impedance is important to consider when matching the cable to prevent signal reflection from the ends of the cable; wave resistance depends on the shape and position of the conductors, on the manufacturing technology and the material of the cable dielectric; typical wave impedance values are from 50 to 150 ohms.
The following cable standards currently apply:
EIA / TIA 568 (Commercial Building Telecommunications Cabling Standard) - American;
ISO/IEC IS 11801 (Generic cabling for customer premises) - international;
CENELEC EN 50173 (Generic cabling systems) - European.
These standards describe almost the same cable systems, but differ in terminology and parameter standards. In this course, it is proposed to adhere to the terminology of the EIA/TIA 568 standard.
1.3 Basics of the Open System Information Exchange Reference Model
The network performs many operations that ensure the transfer of data from computer to computer. The user is not interested in how exactly this happens, he needs access to an application or computer resource located on another computer on the network. In reality, all transmitted information goes through many stages of processing.
First of all, it is divided into blocks, each of which is supplied with control information. The received blocks are made in the form of network packets, then these packets are encoded, transmitted using electrical or light signals over the network in accordance with the selected access method, then the data blocks enclosed in them are restored from the received packets, the blocks are combined into data that become available to another application. This is, of course, a simplified description of the ongoing processes.
Some of these procedures are implemented only in software, the other part - in hardware, and some operations can be performed both by software and hardware.
To streamline all the procedures performed, to divide them into levels and sublevels that interact with each other, just the network models are called upon. These models allow you to correctly organize the interaction of both subscribers within the same network, and a variety of networks at various levels. At present, the so-called OSI (Open System Interchange) reference model for information exchange is most widely used. The term "open system" refers to a system that is not closed in itself and has the ability to interact with some other systems (as opposed to a closed system).
The OSI model was proposed by the International Standards Organization ISO (International Standards Organization) in 1984. Since then, it has been used (more or less strictly) by all manufacturers of network products. Like any universal model, OSI is quite bulky, redundant, and not very flexible. Therefore, actual networking facilities offered by various firms do not necessarily adhere to the accepted separation of functions. However, familiarity with the OSI model allows you to better understand what is happening on the network.
All network functions in the model are divided into 7 levels (Figure 1). At the same time, higher levels perform more complex, global tasks, for which they use lower levels for their own purposes, and also manage them. The purpose of the lower layer is to provide services to the higher layer, and the higher layer does not care about the details of the performance of these services. The lower levels perform simpler and more specific functions. Ideally, each level interacts only with those that are next to it (above and below it). The upper level corresponds to the applied task, the currently running application, the lower one corresponds to the direct transmission of signals over the communication channel.
The OSI model applies not only to local area networks, but also to any communication networks between computers or other subscribers. In particular, the functions of the Internet can also be divided into layers according to the OSI model. The fundamental differences between local networks and global ones, from the point of view of the OSI model, are observed only at the lower levels of the model.
Figure 1 - Seven layers of the OSI model
The functions included in the levels shown in Figure 1 are implemented by each network subscriber. In this case, each level on one subscriber works as if it has a direct connection with the corresponding level of another subscriber. There is a virtual (logical) connection between the same-name levels of network subscribers, for example, between application levels of subscribers interacting over the network. The real, physical connection (cable, radio channel) subscribers of one network have only at the lowest, first, physical level. In the transmitting subscriber, information passes through all levels, from the top to the bottom. In the receiving subscriber, the received information makes the reverse path: from the lower level to the upper one (Figure 2).
The data that needs to be transmitted over the network, on the way from the upper (seventh) layer to the lower (first) one, undergoes an encapsulation process. Each lower level not only processes the data coming from a higher level, but also supplies them with its own header, as well as service information. This process of overgrowing with service information continues to the last (physical) level. At the physical level, this entire multi-shell design is transmitted over the cable to the receiver. There, she performs the reverse decapsulation procedure, that is, when transferred to a higher level, one of the shells is removed. The upper seventh level is already reached by data freed from all shells, that is, from all service information of lower levels. At the same time, each level of the receiving subscriber processes the data received from the next level in accordance with the service information it removes.
Figure 2 - Information path from subscriber to subscriber
If some intermediate devices (for example, transceivers, repeaters, hubs, switches, routers) are included on the path between subscribers in the network, then they can also perform the functions included in the lower levels of the OSI model. The greater the complexity of an intermediate device, the more levels it captures. But any intermediate device must receive and return information at the lower, physical level. All internal data transformations must be done twice and in opposite directions. Intermediate network devices, unlike full-fledged subscribers (for example, computers), operate only at lower levels and also perform two-way conversion.
Figure 3 - Turning on intermediate devices between network subscribers
1.4 Standard network protocols
Protocols are a set of rules and procedures that govern how communication takes place. The computers participating in the exchange must work on the same protocols so that as a result of the transfer all information is restored in its original form.
The protocols of the lower layers (physical and channel) related to the equipment have already been mentioned in the previous sections. In particular, these include methods of encoding and decoding, as well as managing the exchange in the network. Now we should dwell on the features of higher-level protocols implemented in software.
Network adapter communication with network software is carried out by network adapter drivers. It is thanks to the driver that the computer may not know any hardware features of the adapter (its addresses, rules for exchanging with it, its characteristics). The driver unifies, makes the interaction of high-level software with any adapter of this class uniform. The network drivers supplied with the network adapters allow network programs to work equally with cards from different vendors and even cards from different LANs (Ethernet, Arcnet, Token-Ring, etc.). If we talk about the standard OSI model, then drivers, as a rule, perform the functions of the link layer, although sometimes they also implement part of the functions of the network layer (Figure 4). For example, drivers form a packet to be transmitted in the adapter's buffer memory, read a packet that came over the network from this memory, issue a transmission command, and inform the computer about packet reception.
Figure 4 - Network adapter driver functions in the OSI model
The quality of writing a driver program largely determines the efficiency of the network as a whole. Even with the best performance of a network adapter, a low-quality driver can drastically degrade network traffic.
Before you purchase an adapter card, you should review the Hardware Compatibility List (HCL) published by all network operating system manufacturers. The choice there is quite large (for example, for Microsoft Windows Server, the list includes more than a hundred network adapter drivers). If an adapter of some type is not included in the HCL list, it is better not to buy it.
There are several standard sets (or, as they are also called, stacks) of protocols that are now widely used:
a set of ISO/OSI protocols;
IBM System Network Architecture (SNA);
Apple AppleTalk;
a set of protocols for the global Internet, TCP/IP.
The inclusion of WAN protocols in this list is quite understandable, because, as already noted, the OSI model is used for any open system: based on both local and wide area networks or a combination of local and wide area networks.
The protocols of the listed sets are divided into three main types:
application protocols (performing the functions of the top three layers of the OSI model - application, presentation and session);
transport protocols (implementing the functions of the middle layers of the OSI model - transport and session);
network protocols (performing the functions of the three lower layers of the OSI model).
Application protocols enable applications to interact and exchange data between them. Most popular:
FTAM (File Transfer Access and Management) - OSI file access protocol;
X.400 - CCITT protocol for international email exchange;
X.500 - CCITT protocol for file and directory services on multiple systems;
SMTP (Simple Mail Transfer Protocol) - protocol for the global Internet for e-mail exchange;
FTP (File Transfer Protocol) - protocol of the global Internet network for file transfer;
SNMP (Simple Network Management Protocol) - a protocol for monitoring the network, controlling the operation of network components and managing them;
Telnet - a global Internet protocol for registering on remote servers and processing data on them;
Microsoft SMBs (Server Message Blocks, server message blocks) and client shells or redirectors from Microsoft;
NCP (Novell NetWare Core Protocol) and Novell client shells or redirectors.
Transport protocols support communication sessions between computers and guarantee reliable data exchange between them. The most popular of them are the following:
TCP (Transmission Control Protocol) - part of the TCP / IP protocol suite for guaranteed delivery of data broken into a sequence of fragments;
SPX - part of the IPX / SPX (Internetwork Packet Exchange / Sequential Packet Exchange) protocol suite for guaranteed delivery of data broken into a sequence of fragments proposed by Novell;
NetBEUI - (NetBIOS Extended User Interface, extended NetBIOS interface) - establishes communication sessions between computers (NetBIOS) and provides upper layers with transport services (NetBEUI).
Network protocols govern addressing, routing, error checking, and retransmission requests. The following are widespread:
IP (Internet Protocol) - TCP / IP protocol for non-guaranteed transmission of packets without establishing connections;
IPX (Internetwork Packet Exchange) - NetWare protocol for non-guaranteed packet transmission and packet routing;
NWLink is an implementation of the IPX/SPX protocol by Microsoft;
NetBEUI is a transport protocol that provides transport services for NetBIOS sessions and applications.
All of these protocols can be mapped to one layer or another of the OSI reference model. However, it should be taken into account that protocol developers do not strictly adhere to these levels. For example, some protocols perform functions related to several layers of the OSI model at once, while others perform only part of the functions of one of the layers. This leads to the fact that the protocols of different companies are often incompatible with each other. In addition, protocols can be successfully used exclusively as part of their own set of protocols (protocol stack), which performs a more or less complete group of functions. This is precisely what makes the network operating system "proprietary", that is, in fact, incompatible with the standard model of the open system OSI.
As an example, Figure 5, Figure 6, and Figure 7 schematically show the relationship between the protocols used by popular proprietary network operating systems and the layers of the standard OSI model. As can be seen from the figures, practically at no level there is a clear correspondence between the real protocol and any level of the ideal model. Building such relationships is rather arbitrary, since it is difficult to clearly distinguish between the functions of all parts of the software. In addition, software companies do not always describe in detail the internal structure of products.
Figure 5 - Correlation between the levels of the OSI model and Internet protocols
Figure 6 - Correlation between the levels of the OSI model and the protocols of the Windows Server operating system
Figure 7 - Correlation between the levels of the OSI model and the protocols of the NetWare operating system
2. Network technologies
2.1 Networks based on PDH technology
The first digital stream was established in 1957 by the Bell System. In the future, the technology was standardized, and is now known as T1. This was done to meet the ever-increasing needs of telecom operators. Local telephony in the birthplace of technology, the United States, was relatively well developed at that time. Changes on the client network, consisting of copper pairs, were not expected (and have not happened so far). Therefore, the main efforts of operators have been focused on building backbone (transport) networks and their effective use for voice transmission. Naturally, the transfer of data in those days was not even out of the question.
The developed systems used the principle of pulse code modulation and methods of multiplexing (summation) with time division of channels (Time Division Multiplexing, abbreviated as TDM) to transmit several voice channels, otherwise called time slots, in one data stream.
In the USA, Canada and Japan, the T1 stream was taken as the basis, which transmitted 24 timeslots at a speed of 1.536 Mbps, and in Europe (and a little later in the Soviet Union) - the E1 stream, which has a speed of 2.048 Mbps, and allows transmit 30 data channels at a speed of 64 kbps, plus a signaling channel (16 time slot) and synchronization (zero time slot). This, without exaggeration, seemed to be the pinnacle of progress.
Further development led to the emergence of a number of standardized streams E2 - E3 - E4 - E5 with data transfer rates of 8.448 - 34.368 - 139.264 - 564.992 Mbps, respectively. They were called the Plesiochronous Digital Hierarchy - PDH (Plesiochronous Digital Hierarchy), which is still often used for both telephony and data transmission. More modern technologies have almost completely replaced PDH from optical communications, but its position on outdated copper cables is still unshakable. The structure of the PDH network is shown in Figure 8.
Figure 8 - PDH network structure
Each device has its own clock generator, which works with slight differences from others. In a pair of transceivers, the master node sets its synchronization (Sync 1-2), and the slave one adjusts to it. There is no single synchronization for a large network. Therefore, plesiochronous in this case means "almost" synchronous. This is convenient for building individual channels, but causes unnecessary difficulties when creating global networks.
2.2 Networks based on SDH technology
As the networks of different telecom operators merge, the problem of global synchronization of nodes becomes acute. Plus, the complication of the topology caused difficulties in extracting component channels from the stream. The technical features of independent synchronization of different nodes (the presence of equalization bits) made this impossible. That is, to extract the E1 stream from the E4 stream, it is necessary to demultiplex E4 into four E3s, then one of E3s into four E2s, and only then obtain the desired E1.
In this situation, the SONET synchronous optical network developed in the 80s, and the SDH synchronous digital hierarchy, which are often considered as a single SONET / SDH technology, became a successful solution.
The advent of Synchronous Digital Hierarchy (SDH) standards in 1988 marked a new stage in the development of transport networks. Synchronous transmission systems not only overcome the limitations of the predecessor plesiochronous systems (PDH), but also reduced the overhead of information transmission. A number of unique advantages (access to low-speed channels without complete demultiplexing of the entire stream, high fault tolerance, advanced monitoring and control tools, flexible management of permanent subscriber connections) determined the choice of specialists in favor of a new technology that became the basis of new generation primary networks. To date, SDH technology is deservedly considered not only a promising, but also a fairly used technology for creating transport networks. SDH technology has a number of important advantages from a user, operational and investment point of view. Namely:
Moderate structural complexity, which reduces the cost of installation, operation and development of the network, including the connection of new nodes.
Wide range of possible speeds - from 155.520 Mbps (STM-1) to 2.488 Gbps (STM-16) and higher.
Possibility of integration with PDH channels, since digital PDH channels are input channels for SDH networks.
High system reliability due to centralized monitoring and control, as well as the possibility of using redundant channels.
High degree of controllability of the system due to fully software control.
Ability to dynamically provide services - channels for subscribers can be created and configured dynamically, without making changes to the system infrastructure.
A high level of technology standardization, which facilitates the integration and expansion of the system, makes it possible to use equipment from different manufacturers.
High degree of distribution of the standard in world practice.
9. The SDH standard is mature enough to make it a solid investment. In addition to the listed advantages, it is necessary to note the development of backbone telecommunications of Russian telecom operators based on SDH, which provides additional opportunities for attractive integration solutions. The transformation and transmission of data in this system is quite complex. Only a few points need to be noted. As the minimum "transport" unit, a container is used, the size of the payload of which is 1890 bytes, and the service part is 540 bytes. Simplified, they can be thought of as a number of T1/E1 channels combined (multiplexed) into one SONET/SDH channel. At the same time, there is no provision for any connection between the flows, or their change (except for the later and relatively uncommon cross-connectors). The SDH network diagram is shown in Figure 9.
It can be seen that such a scheme was created strictly for the needs of telephony. Indeed, multiplexers (MUX) are usually installed at PBXs, where E1 streams (collected from other multiplexers) are transferred to analog copper lines. Network bandwidth optimization (in other words, interstation connections) is achieved by selecting the ratio of the number of subscriber lines and the flows used.
These advantages make solutions based on SDH technology rational in terms of investment. At present, it can be considered the basis for building modern transport networks, both for corporate networks of various sizes, and for public communication networks. SDH is increasingly being used to build modern digital primary networks.
Also technologies of networks Frame Relay, ISDN (Integrated Service Digital Network), ATM (Asynchronous Transfer Mode) were developed. However, these technologies have not been widely used. Later, WDM (Wavelength Division Multiplexing - spectral channel multiplexing) was developed, technologies
Figure 9 - The structure of the transport network SONET / SDH and the scheme of possible options for the passage of E1 flows
Dense Wave Division Multiplexing (DWDM), multiprotocol MPLS label switching. These technologies are most widely used in the USA, where the market for fiber optic systems is well developed. They are also used on communication networks in other regions of the world, especially in Europe, Asia and Latin America.
2.3 Network topology
Network topology is commonly understood as a way to describe the configuration of a network, the layout and connection of network devices. There are many ways to connect network devices, of which eight basic topologies can be distinguished: bus, ring, star, double ring, mesh topology, lattice, tree, Fat Tree. The remaining methods are combinations of the basic ones. In this case, such topologies are called mixed or hybrid.
Consider some types of network topologies. The topology is widespread - "Common bus" (Figure 10).
Figure 10 - Topology "Common bus"
The common bus topology assumes the use of a single cable to which all computers on the network are connected. A message sent by a workstation propagates to all computers on the network. Each machine checks to see who the message is addressed to and, if so, processes it. Special measures are taken to ensure that when working with a common cable, computers do not interfere with each other to transmit and receive data. In order to exclude the simultaneous sending of data, either a "carrier" signal is used, or one of the computers is the main one and "gives the word" "MARKER" to the rest of the stations. A typical bus topology has a simple cabling structure with short cable runs. Therefore, compared with other topologies, the cost of its implementation is low. However, the low cost of implementation is offset by the high cost of management. In fact, the biggest disadvantage of a bus topology is that diagnosing errors and isolating network problems can be quite difficult, since there are several points of concentration. Since the data transmission medium does not pass through the nodes connected to the network, the loss of operability of one of the devices does not affect other devices in any way. While using just one cable can be seen as an advantage of a bus topology, it is offset by the fact that the cable used in this type of topology can become a critical point of failure. In other words, if the bus breaks, then none of the devices connected to it will be able to transmit signals.
Consider the "Ring" Topology (Figure 11).
Figure 11 - Topology "Ring"
A ring is a topology in which each computer is connected by communication lines to only two others: it only receives information from one, and only transmits information to the other. On each communication line, as in the case of a star, only one transmitter and one receiver operate. This eliminates the need for external terminators. The work in the ring network is that each computer retransmits (resumes) the signal, that is, acts as a repeater, therefore the signal attenuation in the entire ring does not matter, only the attenuation between neighboring computers of the ring is important. In this case, there is no clearly defined center; all computers can be the same. However, quite often a special subscriber is allocated in the ring, which controls the exchange or controls the exchange. It is clear that the presence of such a control subscriber reduces the reliability of the network, because its failure immediately paralyzes the entire exchange.
The computers in the ring are not completely equal (unlike, for example, a bus topology). Some of them necessarily receive information from the computer that is transmitting at this moment, earlier, while others - later. It is on this feature of the topology that the methods of managing exchange over the network are built, specially designed for the "ring". In these methods, the right to the next transfer (or, as they say, to capture the network) passes sequentially to the next computer in the circle. Connecting new subscribers to the "ring" is usually completely painless, although it requires the obligatory shutdown of the entire network for the duration of the connection. As in the case of the "bus" topology, the maximum number of subscribers in the ring can be quite large (up to a thousand or more). The ring topology is usually the most resistant to congestion, it provides reliable operation with the largest flows of information transmitted over the network, because it usually does not have collisions (unlike a bus) and there is no central subscriber (unlike a star) .
In the ring, unlike other topologies (star, bus), the competitive method of sending data is not used, the computer on the network receives data from the previous one in the list of destinations and redirects them further if they are not addressed to it. The mailing list is generated by the computer that is the token generator. The network module generates a token signal (usually on the order of 2-10 bytes to avoid fading) and passes it on to the next system (sometimes in ascending MAC address). The next system, having received the signal, does not analyze it, but simply passes it on. This is the so-called zero cycle.
The subsequent operation algorithm is as follows - the GRE data packet transmitted by the sender to the addressee begins to follow the path laid by the marker. The packet is transmitted until it reaches the recipient.
The next type of topology is "Star" (Figure 12).
A star is the basic topology of a computer network in which all computers on the network are connected to a central node (usually a network hub), forming a physical network segment. Such a network segment can function both separately and as part of a complex network topology (usually a "tree"). The entire exchange of information takes place exclusively through the central computer, which in this way bears a very large load, therefore it cannot do anything other than the network. As a rule, exactly
Figure 12 - Topology "Star"
the central computer is the most powerful, and it is on it that all the functions of managing the exchange are assigned. No conflicts in a network with a star topology are in principle impossible, because management is completely centralized. The workstation from which it is necessary to transfer data sends them to the hub, which determines the addressee and gives him information. At a given time, only one machine on the network can send data, if two packets arrive at the hub at the same time, both packets are not received and senders will have to wait a random amount of time to resume data transmission. This drawback is absent on a higher-level network device - a switch, which, unlike a hub that sends a packet to all ports, feeds only to a certain port - the recipient. Multiple packets can be sent at the same time. How much depends on the switch.
Along with the well-known topologies of computer networks ring, star and bus, a combined one, for example, a tree structure, is also used in practice (Figure 13). It is formed mainly in the form of combinations of the above topologies of computer networks. The base of the computer network tree is located at the point (root) where communication information lines (tree branches) are collected.
Computing networks with a tree structure are used where it is impossible to directly apply the basic network structures in their pure form. To connect a large number of workstations, according to adapter cards, network amplifiers and / or switches are used. A switch that simultaneously has the functions of an amplifier is called an active hub.
Figure 13 - Topology "Tree"
In practice, two varieties are used, providing the connection of eight or sixteen lines, respectively.
A device to which a maximum of three stations can be connected is called a passive hub. A passive hub is usually used as a splitter. It doesn't need an amplifier. The prerequisite for connecting a passive hub is that the maximum possible distance to the workstation must not exceed several tens of meters.
The topology of the network determines not only the physical location of computers, but, much more importantly, the nature of the connections between them, the characteristics of the propagation of signals over the network. It is the nature of the connections that determines the degree of network fault tolerance, the required complexity of network equipment, the most appropriate method of exchange control, the possible types of transmission media (communication channels), the allowable network size (the length of communication lines and the number of subscribers), the need for electrical coordination, and much more.
3. Development of a subscriber access network
3.1 Development input
The subscriber access network is being developed according to the task for the graduation project for the territory shown in Figure 14 in order to provide broadband Internet access and exchange of information between network users. The network is being developed using Ethernet technology using fiber-optic communication lines and copper cable and assumes the presence of several servers. The expected speed of subscriber access, taking into account the bandwidth of the city network, is 100 Mbps. Previously, the speed of subscriber access was 10 Mbps, but due to the use of improved equipment, it was possible to provide users with a higher speed. To connect to the network to computers, the following requirements are put forward:
The presence in the computer of a network adapter with an Ethernet 10/100BaseTX interface;
The presence of an operating system that supports the TCP / IP protocol.
3.2 Basic network solutions
For the convenience of segmenting the network, we use a quarterly division of the "Star" type. Segments to improve network manageability are divided into subnets. We will divide the territory into segments, each of which covers several houses (from 4 to 10). Each segment is connected to the quarterly equipment through an optical converter according to the 1000BaseLX standard using a fiber optic cable in order to increase the distance of the cable segment and high data transmission speed. Each quarterly equipment is connected to the central communication node via an optical converter according to the Gigabit Ethernet 1000BaseLX standard to increase the throughput on the network backbone.
Figure 14 - Design area
Central communication node (located at the PBX by agreement of the parties): We will choose the SDH network access technology due to the high bandwidth of the paths, flexibility, and the ability to dynamically increase the network capacity without interrupting traffic. At the central node, we will place the main switch and router for accessing the SDH network of the backbone provider and servers responsible for counting traffic, for monitoring the network, and a DNS server will also be installed. ), as well as the computer on which the software is running. The DNS server may be responsible for some zones, or may forward queries to upstream servers.
Similar Documents
Analysis of existing topologies for building a MetroEthernet network. Evaluation of typical solutions for building subscriber access networks. Calculation of equipment for voice transmission services. Development of a topological and situational scheme. Calculation of the traffic of telephony services.
term paper, added 05/17/2016
Existing public telephone network. Bandwidth calculation for providing Triple Play services. Calculation of the total network bandwidth for transmitting and receiving data. Choice of subscriber access switch and optical cable.
thesis, added 01/19/2016
Classification and characteristics of access networks. Technology of networks of collective access. Choice of broadband access technology. Factors affecting ADSL quality parameters. Methods for configuring subscriber access. Basic components of a DSL connection.
thesis, added 09/26/2014
Review of modern systems of wireless subscriber access. Features of using OFDM modems and OFDMA multiple access. Development of an information network based on Mobile WiMAX technology, evaluation of the economic efficiency of its implementation.
thesis, added 07/12/2010
Development and areas of application, technical foundations of PLC and technological prerequisites for the implementation of PLC solutions, an overview of broadband subscriber access technologies. The principle of operation and the main capabilities of the equipment, an approximate scheme of network organization.
thesis, added 07/28/2010
Modern means of communication and their characteristics. Development of the structure of the data transmission network. Select the type of access. Basic levels of the OSI model, access technology. Choice of equipment, characteristics of the server. Calculation of cost indicators for laying the network.
term paper, added 04/22/2013
Topology of computer networks. Carrier access methods in computer networks. Data transmission media, their characteristics. Structural model of OSI, its levels. IP protocol, principles of packet routing. The physical topology of the network. Subnet class definition.
control work, added 01/14/2011
Overview of existing broadband access technologies (xDSL, PON, wireless access). Description of the features of PON technology. Project for the construction of a subscriber access network based on passive optical network technology. Scheme of distribution areas.
thesis, added 05/28/2016
Selection and justification of technologies for building local area networks. Analysis of the data transmission environment. Calculation of network performance, layout of premises. Choice of network software. Types of standards for wireless access to the Internet.
term paper, added 12/22/2010
Basic principles of organizing subscriber access networks based on PLC technology. Threats to local networks, security policy when using PLC technology. Analysis of the functioning of the PLC of the building of the engineering and development center of LLC NPP Inteps Kom.
The modern development of local telecommunication networks is focused on providing the most complete range of services, ranging from standard telephony to modern multimedia services. This allows us to consider the elements of networks not only from the point of view of the presence of certain linear structures and various equipment, but also from the point of view of their functional purpose.
The subscriber access network is a set of technical means between the terminal subscriber devices installed in the user's premises and the switching equipment, the numbering plan (or addressing) of which includes terminals connected to the telecommunications system.
Based on this definition, the boundaries of the subscriber access network vary widely depending on the type of information transmitted (analogue telephony, ISDN services, data transmission and the Internet, broadcasting, television) and include various fragments of traditional wired and wireless networks. In some cases, these are just subscriber lines, in some cases they are subscriber lines, subscriber concentrators and trunk lines to core exchanges, in some cases they are a combination of xDSL active equipment and copper or optical communication lines, etc.
Also, fragments of a cable television network, wireless communication equipment can be used as an information transfer medium.
Subscriber access networks operating on the basis of wired technologies can be divided into the following types:
PBX analogue subscriber lines and digital subscriber line multiplexing systems that allow organizing several telephone lines over one pair of copper cable;
Integrated services digital network (ISDN), which involves the organization of digital subscriber lines based on basic interfaces (BRI) and primary access (PRI). Often, in addition to ISDN terminals, these networks include equipment for office and office-industrial automatic telephone exchanges of corporate users of communication services;
C) a network based on ADSL technology (asymmetric digital subscriber line), which allows organizing an asymmetric data transmission channel simultaneously with analog telephony. The greatest development of this technology is associated with an increase in the need for access to the Internet. The network provides a dedicated channel for Internet access at a low cost, operates over existing subscriber lines and is used mainly by individual customers of the telephone network;
Access network based on xDSL technologies (except ADSL), providing various options (speed, type of transmitted information) for access to communication networks. The network is designed to connect corporate and individual users and can operate over copper and optical communication lines;
Wireless subscriber access network WLL (wireless subscriber line), which involves fixed placement or limited mobility of subscriber radio equipment and does not require large costs for the construction of cable structures when deployed. This network can be built on the basis of equipment operating according to the DECT standard.
The technology of wired subscriber access has five main groups according to the criterion of transmission medium and categories of users. On fig. 1 shows their classification.
LAN (Local Area Network) is a group of technologies designed to provide corporate users with access to local area network resources and using structured cabling systems of categories 3, 4 and 5, coaxial cable and fiber optic cable as a transmission medium.
DSL (Digital Subscriber Line) is a group of technologies designed to provide PSTN users with multimedia services and use the existing PSTN infrastructure as a transmission medium.
CATV (cable television) is a group of technologies designed to provide users of CATV networks with multimedia services (due to the organization of a reverse channel) and using fiber optic and coaxial cables as a transmission medium.
OAN (Optical Access Networks) is a group of technologies designed to provide users with broadband services, a line of access to multimedia services and using fiber optic cable as a transmission medium.
SKD (multiple access networks) - a group of hybrid technologies for organizing access networks in apartment buildings; the existing infrastructure of the PSTN, radio broadcasting networks and power supply networks is used as a transmission medium.
One of the most important problems of telecommunication networks continues to be the problem of subscriber access to network services. The urgency of this problem is determined primarily by the rapid development of the Internet, access to which requires a sharp increase in the bandwidth of subscriber access networks. The main means of the access network, despite the emergence of new most modern wireless methods of subscriber access, are traditional copper subscriber pairs. The reason for this is the natural desire of network operators to protect the investments made. Therefore, at present and in the foreseeable future, the technology of asymmetric digital subscriber line ADSL will remain a strategic direction for increasing the capacity of subscriber access networks, using a traditional copper subscriber pair as a transmission medium and at the same time preserving already provided services in the form of an analog telephone or basic access to ISDN. The implementation of this strategic direction in the evolution of subscriber access networks depends on the specific conditions of the existing subscriber access network of each country and is determined by each telecom operator, taking into account these specific conditions. It is clear that the variety of local conditions determines a large number of possible ways to migrate the existing subscriber access network to ADSL technology.
Telecommunication technologies are constantly improving, quickly adapting to new requirements and conditions. More recently, the main and only means of subscriber access to network services - and primarily to Internet services - was an analog modem. However, the most advanced analog modems are the modem that meets the requirements of ITU-T V.34 recommendation, with a potential transmission rate of up to 33.6 Kbps, as well as the next generation modem that meets the requirements of ITU-T Recommendation V.90, with a potential transmission rate 56 Kbit/s practically cannot provide effective user experience on the Internet.
Thus, a sharp increase in the speed of access to network services, and primarily to Internet services, is critically important. One of the methods for solving this problem is the use of the xDSL high-speed subscriber line technology family. These technologies provide a high throughput of the subscriber access network, the main element of which is a twisted copper pair of the local subscriber telephone network. Although each of the xDSL technologies occupies its own niche in the telecommunications network, it is nevertheless undeniable that the ADSL asymmetric digital high-speed subscriber line and VDSL ultra-high-speed digital subscriber line technologies are of the greatest interest to telecommunications service providers, equipment manufacturers, and users. And this is not accidental - ADSL technology appeared as a way to provide the user with a wide range of telecommunication services, including primarily high-speed access to the Internet. In turn, VDSL technology is able to provide the user with a wide bandwidth that allows him to access almost any broadband network service both in the near and distant future, but not in a pure copper, but in a mixed, copper-optical access network . Thus, both of these technologies will provide an evolutionary path for the introduction of optical fiber into the subscriber access network, protecting the past investments of local network operators in the most effective way. Thus, ADSL can be seen as the most promising member of the xDSL family of technologies, which will be succeeded by VDSL technology.
Although the key idea of migrating network service delivery methods using xDSL technologies is to move from the analogue public telephone network first to ADSL, and then, as necessary, to VDSL, this does not exclude the use of other intermediate steps for the same purpose. types of xDSL technologies. For example, IDSL and HDSL technologies can be used to increase subscriber line capacity.
From analog modem to ADSL
The most common migration scenario for accessing Internet services is by far the transition from a source access network using analog PSTN modems to a target access network using ADSL modems.
ADSL (Asymmetric Digital Subscriber Line - asymmetric digital subscriber line). This technology is asymmetric. This asymmetry, combined with the "always connected" state (where there is no need to dial a phone number each time and wait for a connection to be established), makes ADSL technology ideal for providing access to the Internet, access to local area networks (LANs), etc. When organizing such connections, users usually receive much more information than they transmit. ADSL technology provides downstream data rates ranging from 1.5 Mbps to 8 Mbps and upstream data rates from 640 Kbps to 1.5 Mbps. ADSL technology makes it possible to maintain the traditional service without significant costs and provide additional services, including:
- § preservation of the traditional telephone service,
- § high-speed data transmission at a speed of up to 8 Mbps to the user of the service and up to 1.5 Mbps - from him,
- § high-speed Internet access,
- § transmission of one television channel with high quality, video-on-demand,
- § distance learning.
Compared to alternative cable modems and fiber optic lines, the main advantage of ADSL is that it uses existing telephone cable. At the ends of the existing telephone line, frequency dividers are installed (some use a tracing paper from the English splitter), one for the PBX and one for the subscriber. A regular analog telephone and an ADSL modem are connected to the subscriber splitter, which, depending on the version, can act as a router or bridge between the subscriber's local network and the provider's border router. At the same time, the operation of the modem absolutely does not interfere with the use of conventional telephone communication, which exists regardless of whether the ADSL line is functioning or not.
Currently, there are two versions of ADSL technology: the so-called full-blown ADSL, which is simply called ADSL, and the so-called "light" version of ADSL, which is called "ADSL G. Lite". Both versions of ADSL are currently covered by ITU-T G.992.1 and G.992.2, respectively.
The full ADSL concept was originally born as an attempt to compete with local telephone network operators against cable television (CATV) operators. Almost 7 years have passed since the appearance of ADSL technology, but so far it has not received mass practical application. Already in the process of developing full-scale ADSL and the first experience of its implementation, a number of factors emerged that required correction of the original concept.
The main of these factors are the following:
- 1. Change in the main targeted use of ADSL: at present, the main type of broadband subscriber access is no longer the provision of cable TV services, but the organization of broadband access to the Internet. To meet this new challenge, 20% of the maximum throughput of full-blown ADSL is sufficient, which corresponds to a downstream (network-to-subscriber) rate of 8.192 Mbps and an upstream (subscriber-to-network) rate of 768 Kbps.
- 2. Unavailability of the Internet to provide full-scale ADSL services. The fact is that the ADSL system itself is only part of a network of broadband access to network services. Already the first experiences of introducing ADSL into real access networks have shown that today's Internet infrastructure cannot support transmission rates above 300,400 Kbps. Although the backbone of the Internet access network is usually carried out on an optical cable, however, it is not this network, but other elements of the Internet access network - such as routers, servers and PCs, including the characteristics of Internet traffic, that determine the real throughput of this network. Therefore, the use of full-scale ADSL on the existing network practically does not solve the problem of broadband subscriber access, but simply moves it from the subscriber section of the network to the backbone network, exacerbating the problems of the network infrastructure. Therefore, the introduction of full-scale ADSL will require a significant increase in the bandwidth of the backbone section of the Internet, and, consequently, significant additional costs.
- 3. High cost of equipment and services: for a wide deployment of technology, it is necessary that the cost of an ADSL subscriber line be no more than $500; existing prices are significantly higher than this value. Therefore, other xDSL products are actually used and, first of all, HDSL modifications (such as multi-rate MSDSL) with a bandwidth of 2 Mbps over a single copper pair.
- 4. The need to modernize the infrastructure of the existing access network: the concept of a full-scale ADSL requires the use of special crossover filters - the so-called splitters (splitter "s), separating the low-frequency signals of an analog phone or BRI ISDN main access and high-frequency broadband access signals both in the PBX premises and at the user's premises.This operation is labor-intensive, especially in a branch exchange where thousands of subscriber lines terminate.
- 5. The problem of electromagnetic compatibility, which consists in the insufficient study of the effect of full-scale ADSL on other high-speed digital transmission systems (including the xDSL type) operating in parallel in the same cable.
- 6. Large power consumption and footprint: Existing ADSL modems, in addition to high cost, require a lot of space and consume significant power (up to 8 W per active ADSL modem). In order for ADSL technology to be acceptable for deployment in a switching office, it is necessary to reduce power consumption and increase port density.
- 7. Asymmetric operation of full-scale ADSL: with a constant bandwidth of the ADSL line, it is an obstacle for some applications that require symmetrical transmission mode, such as video conferencing, as well as for organizing the work of some users who have their own Internet servers. Therefore, an adaptive ADSL capable of operating in both asymmetric and symmetrical modes is needed.
- 8. User premises hardware and software have also been tested to be the bottleneck of ADSL systems. Testing has shown, for example, that popular programs such as Web browsers and PC hardware platforms can limit PC bandwidth to 600 Kbps. Thus, in order to fully utilize high-speed ADSL connections, improvements in the user's client hardware and software are needed.
These problems of full-scale ADSL initiated the emergence of its "light" version, which is the already mentioned ADSL G.Lite. Here are the most significant features of this technology.
Opportunity to work in both asymmetric and symmetric modes: in asymmetric mode at a transmission rate of up to 1536 Kbps in the downstream direction (from the network to the subscriber) and up to 512 Kbps in the upstream direction (from the subscriber to the network); in symmetrical mode - up to 256 Kbps in each direction of transmission. Both modes use the DMT code to automatically adjust the transmission rate in steps of 32 Kbps depending on the line length and interference power.
Simplifying the process of installing and configuring ADSL GLite modems by eliminating the use of crossover filters (splitters) at the user's premises, which allows the user to perform these procedures himself. It does not require replacement of internal wiring in the user's premises. However, as the test results show, this can not always be done. An effective measure to protect a broadband data transmission channel from pulse dialing signals and ringing signals is to install special microfilters directly in the telephone socket.
Realizable lengths of ADSL GLite lines make it possible to provide the vast majority of home sector users with high-speed Internet access. It should be noted that many ADSL equipment manufacturers have chosen the concept of ADSL equipment that supports both full speed ADSL mode and ADSL G.Lite mode. It is assumed that the emergence of ADSL G.Lite equipment will sharply activate the market for broadband Internet access devices. It is highly likely that it will occupy the niche of broadband access to network services for home users.
The advent of the ADSL intermediate stage in the form of ADSL G.Lite creates the possibility of a seamless transition from existing analog modems to broadband access - first to the Internet using G.Lite, and then to multimedia services using full-blown ADSL.
Migration from an analog modem to any of the ADSL modifications is beneficial to the service provider, since calls of increased duration, such as user calls to the Internet, are routed bypassing the public switched telephone network. If the service provider is a traditional local network operator, then this scenario gives him another additional (but no less important) advantage, since there is no need for a costly upgrade of the existing telephone network switch to an ISDN switch, which would be needed to increase the speed of access to Internet services with option of migration from public telephone network services to ISDN network services. The significant additional investment in migrating from analog PSTN to ISDN is because the latter is a networking concept with its own very powerful layered protocol stack. Therefore, this upgrade requires significant changes in the hardware and software of the PSTN digital switching station. At the same time, an ADSL modem is simply a high-speed modem that uses standard data network protocols based on ATM packet or cell transmission. This significantly reduces the difficulty of accessing the Internet and hence the investment required.
Also, from the point of view of Internet users, network operators, and Internet service providers, it makes more sense to move directly from a PSTN modem not to an ISDN modem, but directly to an ADSL modem. With a maximum throughput of narrowband ISDN of 128 Kbps (which corresponds to the combination of two B-channels of the main ISDN access), the transition to ISDN gives an increase in access speed compared to the PSTN network by a potentially slightly more than 4 times and requires in addition significant investment. Therefore, the intermediate stage of transition from the PSTN to ISDN as an effective means of accessing the Internet is practically meaningless. Of course, this does not apply to those regions where there is already widespread adoption of ISDN. Here, of course, the determining factor is the protection of the investments made.
Thus, the main incentives for the considered method of access network migration are:
- § A huge increase in the speed of access to Internet services.
- § Preservation of analog telephone or basic access to ISDN (BRI ISDN).
- § Moving Internet traffic from the PSTN network to an IP or ATM network.
- § No need to upgrade the PSTN switch to an ISDN switch.
If the main incentive for migrating from an analog modem to an ADSL modem is high-speed Internet access, then the most appropriate way to implement this service should be considered to be the implementation of a remote ADSL terminal, called ATU-R, in the form of a personal computer (PC) card. This reduces the overall complexity of the modem and eliminates internal wiring problems (from modem to PC) at the user's premises. However, telephone network operators are generally reluctant to rent an ADSL modem if it is an internal PC board, as they do not want to be held responsible for possible damage to the PC. Therefore, remote ATU-R terminals have become more widespread so far in the form of a separate unit, called an external ADSL modem. An external ADSL modem is connected to the LAN port (10BaseT) or serial port (USB serial bus) of the computer. This design is more complex as it requires additional space and a separate power supply. But such an ADSL modem can be purchased by a subscriber of the local telephone network and put into operation by a PC user on his own. In addition, an external modem can be connected not to a PC, but to a LAN hub or router in cases where the user has several computers.
And this situation is typical for organizations, business centers and residential complexes.
Migration to ADSL in the presence of DSPAL access in the network
The previous migration scenario requires a continuous physical copper pair between the local PBX premises and the customer premises. This situation is more typical for developing countries with a relatively underdeveloped telecommunications network, including Russia. In countries with a developed telecommunications network on the subscriber telephone network, digital subscriber transmission systems (DTSTS) are widely used to increase the overlapping distances, mainly using the equipment of primary digital transmission systems of the plesiochronous hierarchy (E 1). For example, in the United States in the early 90s, approximately 15% of all subscriber lines were serviced using DSLSL (in the United States they are called Digital Local Carrier - DLC), in the future it is expected to increase their total capacity to 45% of the total number of subscriber lines. Currently, very reliable subscriber access networks are being built that use a combined copper-optical transmission medium and secure ring structures using SDH synchronous digital hierarchy equipment.
Modern DSLTS not only multiplex the signals of a certain number of subscribers into a digital stream transmitted over two symmetrical pairs, but can also perform the functions of load concentration (2: 1 or more), which makes it possible to reduce the load on switching stations. In this case, one terminal terminal of the DSPAL is located in the PBX, and the other is located at an intermediate point between the PBX and the user's premises. Therefore, an individual physical subscriber line exists only between the user's premises and the remote terminal of the DSPAL. Therefore, the ADSL access multiplexer (DSLAM - DSL access multiplexor) and its component - the station ADSL ATU-C terminal - should not be located at the PBX, but at the installation site of the remote terminal (RDT). At the same time, the following technical solutions are used to organize ADSL systems:
- 1. Remote DSLAM, which is located in a separate container near the RDT container and is designed to serve a large number of users (typically 60 to 100 ADSL lines). In this case, no special management and maintenance system is required, since the control system for setting up and monitoring the status of ADSL lines of a typical DSLAM installed in the PBX premises is used. Such a DSLAM can work with almost any DSSL equipment, since it is a stand-alone equipment; The DSLAM simply separates the PSTN traffic from the actual ADSL line traffic and passes it to the DSLAM equipment in analog form. At the same time, such a solution is very expensive: since DSLAM equipment is autonomous, serious installation and assembly work, equipment power supply, and much more are required; therefore, this solution is expedient only for a large number of DSSL users.
- 2. ADSL line cards built into the DSPAL equipment. In this case, free places are used in the boards of the DSPAL equipment placed in the RDT container, and two options are possible:
- § The DSLB equipment is used only for placement and mechanical protection of ADSL boards, and all connections are made using cables, which is typical for traditional DSPs;
- § The ADSL line card is part of the DSPAL equipment and is simply integrated into the latter. This second method is usually used in the new generation of DSPAL equipment and makes it possible to eliminate the need for any installation work in the DSPAL unit.
- § Remote access multiplexor (RAM -- remote access multiplexor), which performs the same functions as the DSLAM. It differs from DSLAM in that it is integrated into the existing DSLAM infrastructure and does not require significant upgrades of the existing subscriber access network infrastructure associated with significant costs. The use of RAM is universal, since it provides the ability to work with any type of DSLSL equipment. Typically, RAM blocks are small and can be placed in existing containers with RDT equipment. The main problem with currently known RAMs is their lack of scalability.
From ISDN to ADSL
In the 1990s, ISDN lines became widely used as a way to access the Internet faster where possible. Over time, when ISDN bandwidth becomes insufficient, the natural solution will be to "complement" the ISDN subscriber line with a high-speed ADSL channel. As with conventional analog lines, this method, called "ISDN under ADSL", uses filters to separate the ADSL and ISDN signals.
Such a solution is particularly attractive in that it causes virtually no problems with the implementation of narrowband ISDN standards and, therefore, with the implementation of the transition from ISDN to ADSL. Therefore, this mode of evolution will be especially popular in countries where narrowband ISDN has been widely adopted, and the transition from ISDN to full-scale ADSL is likely to prevail.
From HDSL to ADSL
HDSL (High Bit-Rate Digital Subscriber Line) technology is by far the most mature and cheapest of the xDSL technologies. It arose as an effective alternative to the obsolete equipment of primary DSPs E! for use on LAN trunks, and as ISDN Primary Access (PRA ISDN). Due to the widespread use of HDSL in various regions of the world, procedures for deploying such systems, their maintenance and testing are well established; The high quality parameters and high reliability of HDSL systems are also well known. Therefore, telecom operators and network service providers are willing to use HDSL equipment for high-speed Internet access. However, most often the use of HDSL in a subscriber access network requires the use of at least two copper pairs, which is practically not always possible. The use of only one pair for the organization of the HDSL line significantly reduces the overlapping distances. In addition, HDSL equipment does not provide for the possibility of organizing an analog telephone, which requires the use of an additional subscriber pair for this purpose. Thus, there are significant factors driving the feasibility of moving from HDSL to ADSL. With such a migration, the throughput of the access network in the downstream direction (ie from the network to the subscriber) increases sharply, just one pair is enough and it becomes possible to organize an analog telephone. However, this migration scenario can be problematic. Thus, the throughput of an ADSL access network in the upstream direction (ie from the subscriber to the network) is generally less than the corresponding throughput of the HDSL throughput.
From IDSL to ADSL
One of the modifications of xDSL technologies is the so-called IDSL technology, which has a more complete abbreviation "ISDN DSL". IDSL (ISDN Digital Subscriber Line - IDSN digital subscriber line). This technology appeared as an adequate response of equipment manufacturers and Internet service providers to the problems associated with the overload of the switched ISDN network with Internet user traffic, and the insufficient speed of access to the Internet using analog modems for many users.
IDSL technology simply involves the formation of a digital point-to-point path with a bandwidth of 128 Kbps based on the BRI ISDN basic access format by combining two basic B-channels of 64 Kbps each; however, the auxiliary D-channel provided in the BRI ISDN format is not used, i.e., the IDSL path has a "128+0" Kbps structure. IDSL uses standard ISDN digital subscriber line chips (so-called U-interface). However, unlike the ISDN U-interface, IDSL equipment is connected to the Internet not through a PSTN or ISDN switch, but through a router. Therefore, IDSL technology is only used for data transmission and cannot provide PSTN or ISDN voice services.
The most attractive properties of IDSL are the maturity of ISDN technology, the low cost of ISDN U-interface chips, the ease of installation and maintenance compared to the installation and maintenance of standard ISDN (because IDSL bypasses the ISDN exchange), and the ability to use standard ISDN metering equipment. In addition, carriers and ISPs deploying ISDN are generally very familiar with the latter. Therefore, there are no problems associated with the planning and maintenance of IDSL lines. The main driver behind the migration from IDSL to ADSL is the provision of faster Internet access compared to an analog modem. However, keep in mind that when using IDSL to access the Internet, a second subscriber line is needed to access the PSTN. The transition to ADSL technology, which retains the possibility of subscriber access to the switched telephone network (and, if necessary, to the Internet), allows the user to limit himself to only one subscriber line, which is beneficial not only to the latter, but also to the telecom operator.
SDSL (Symmetric Digital Subscriber Line - symmetrical digital subscriber line). Like HDSL technology, SDSL technology provides symmetrical data transmission at rates corresponding to T 1 /E 1 line rates, but SDSL technology has two important differences. Firstly, only one twisted pair of wires is used, and secondly, the maximum transmission distance is limited to 3 km. The technology provides the advantages necessary for business representatives: high-speed access to the Internet, organization of multi-channel telephone communication (VoDSL technology), etc. The same subfamily should also include MSDSL (Multi-speed SDSL) technology, which allows you to change the transmission speed to achieve optimal range and vice versa.
SDSL can be described in the same way as HDSL. True, it allows you to travel a shorter distance than HDSL, but you can save on the second pair. Very often, the user's office is at a distance of no more than 3 km from the point of presence of the operator, and then this technology has a clear advantage over HDSL in terms of price / quality of service for its user. The MSDSL option allows, in case of not very good cable condition, to cover the same distance, but at a lower speed, besides, not all clients need the full 2 Mbps and very often 256 or even 128 kbps is enough.
As another modification of SDSL, HDSL2 equipment is used, which is an improved version of HDSL using a more efficient transmission line code.
Opportunities for self-evolution of ADSL: from Internet access to the provision of a full set of network services
The considered methods of broadband access migration relate to the lower, physical layer of a multi-layer telecommunication model, since the xDSL technologies themselves are essentially technologies of the physical layer. No less interesting are the ways of ADSL's own evolution from access to the Internet to the provision of a full range of network services. Under the full set of network services, we mean primarily multimedia services and interactive video.
At present, approximately 85% of the total broadband service is Internet access, and only 15% is access to multimedia services and interactive television. Therefore, the first stage of broadband access will in the vast majority of cases be access to the Internet. The strategy for providing broadband services is now fairly well represented by the ITU-T concept of a broadband network with ISDN service integration, abbreviated as B-ISDN. As a key element of the B-ISDN network, the asynchronous transmission method (ATM) was chosen, which is based on the concept of optimal use of the channel bandwidth for the transmission of heterogeneous traffic (voice, images and data). Therefore, ATM technology claims to be a universal and flexible transport, which is the basis for building other networks.
ATM, like any revolutionary technology, was created without taking into account the fact that large investments have been made in existing technologies, and no one will refuse old soundly working equipment, even if new, more advanced equipment has appeared. Therefore, the ATM method first appeared on territorial networks, where the cost of ATM switches compared to the cost of the transport network itself is relatively small. For a LAN, the replacement of switches and network adapters is practically equivalent to a complete replacement of network equipment, and the transition to ATM can only be caused by very serious reasons. Obviously, the concept of the gradual introduction of ATM into the existing user network looks more attractive (and, perhaps, more realistic). In principle, ATM allows you to directly transfer messages of application layer protocols, but is more often used as a transport for protocols of the link and network layers of networks that are not ATM networks (Ethernet, IP, Frame Relay, etc.).
ATM technology is currently recommended by both the ADSL Forum and ITU-T and for the ADSL line equipment itself (ie, the ATU-C Access Point Modem and the ATU-R User Premises Remote Modem). This is primarily due to the fact that ATM is the B-ISDN broadband access network standard.
At the same time, the vast majority of servers and user equipment on the Internet support the TCP/IP and Ethernet protocols. Therefore, when moving to ATM technology, it is necessary to make maximum use of the stack of existing TCP/IP protocols as the main tool for broadband access to the Internet. This applies not only to the transport and network layer of TCP / IP, but also to the link layer. The above primarily refers to the protocol (more precisely, to the protocol stack) PPP ("Point to point protocol"), which is a link layer protocol of the TCP / IP protocol stack and regulates the procedures for transmitting information frames over serial communication channels.
The PPP protocol is currently widely used by network providers to access Internet services using analog modems and provides the ability to control the so-called AAA functions:
- § Authentication (authentication, i.e., the process of user identification).
- § Authorization (authorization, i.e., access rights to specific services).
- § Accounting (resource accounting, including billing of services).
When performing all these functions, the protocol also guarantees the necessary protection of information. Just as important for an ISP is the ability to dynamically allocate a limited number of IP addresses to its customers. This feature is also supported by the PPP protocol. Thus, it is very important for both the ISP and the user to maintain the PPP protocol for broadband Internet access via an ADSL line using the ATM method.
In addition to the considered method of operating an ADSL network using ATM technology, which is briefly called "PPP over ATM", there are a number of others: "Classical IP over ATM" ("Classical IP and ARP over ATM" or IPOA), developed by the ATM Forum specification "Emulation local area networks" (LAN emulation or LANE), a new specification of the ATM Forum "Multiprotocol Over ATM" (or MPOA).
Although the ATM standard is recognized as the most promising universal standard for the transmission of heterogeneous information (voice, video and data), however, it is not without drawbacks, the main of which is still the complex and long process of setting up a permanent virtual PVC channel.
Currently, the most popular data transfer protocol, and primarily for Internet applications, is the TCP / IP protocol stack. In connection with the advent of ATM technology, the question arises: "Should we not completely abandon TCP / IP and adopt only ATM?" Life has shown that the most correct thing is to combine the advantages of these two technologies. Therefore, as a tool for migrating ADSL technology from Internet access to providing a full set of network services, the ADSL Forum considers not only the ATM method, but also the TCP / IP standard. This is quite logical and in the interests of both telecom operators and users, given the wide variety of local access network conditions.
From ADSL to VDSL
As user demand for increased bandwidth grows, pure copper subscriber access networks will increasingly migrate to combined copper-optical networks, collectively known as FITL (Fiber In The Loop). As the optical fiber in this combined network approaches the user's premises on its copper section, VDSL technology may be in demand, which will replace ADSL. VDSL (Very High Bit-Rate Digital Subscriber Line - ultra-high-speed digital subscriber line). VDSL technology is the highest speed xDSL technology. In the asymmetric version, it provides the data rate of the "downstream" stream in the range from 13 to 52 Mbps, and the data rate of the "upstream" stream in the range of 1.6 to 6.4 Mbps, in the symmetrical version - in ranging from 13 to 26 Mbps, and one twisted pair of telephone wires. VDSL technology can be seen as a cost effective alternative to running fiber optic cable to the end user. However, the maximum transmission distance for this technology is between 300 m (at 52 Mbps) and up to 1.5 km (at up to 13 Mbps). VDSL technology can be used for the same purposes as ADSL; in addition, it can be used for transmission of high-definition television (HDTV) signals, video-on-demand, etc.
Our lag in the development of data transmission networks played a positive role - operators did not have time to invest significant funds in the equipment of narrow-band ISDN switched networks, as well as in the development of subscriber sections of data transmission networks based on HDSL and IDSL equipment.
From the foregoing, it is clear that in Russian conditions the scenario of the evolution of wired subscriber access networks from an analog modem to ADSL will be most widespread. Already today, the demand for high-speed Internet access services has grown so much that it makes sense, at least, to start working out the economic and technical issues of deploying subscriber access networks based on xDSL technologies.
Thus, each technology from the family of xDSL technologies successfully solves the problem for which it was developed. Two of them, ADSL and VDSL, allow telecom operators to provide new types of services, and the existing telephone network has real prospects of becoming a full-service network. As for the operators themselves, most likely, over time, only those that can provide the user with the maximum range of services will remain.
Connecting subscribers using optical fiber
Equipment for connecting subscribers using an optical cable has become widespread in Europe and the USA. The advantages of such a solution are obvious: high reliability, transmission quality, as well as throughput, therefore, practically unlimited speed on the user interface. Unfortunately, this solution also has disadvantages. First, the time required to lay the cable and obtain all the necessary permits can be quite significant, which reduces the rate of return on investment. Secondly, the use of optical fiber can be economically justified only when connecting a large number of subscribers concentrated in one place, for example, in mass construction areas or in office buildings. In areas where the density of subscribers is low, the resources of the optical cable are used only by 5 - 10%, so it is more cost-effective to compact the existing cable network or use radio access.
Now, fiber optics is widely used instead of multi-core telephone cables in the area between the telephone exchange (PBX) and a remote hub, to which, for example, telephones installed in apartments of a multi-storey building or several houses are connected. The equipment that implements multiplexing / demultiplexing of individual subscriber connection lines is called Digital Loop Carrier (DLC), which can be translated as “digital telephone line concentration system”. Such systems are produced in the USA, Western Europe, Asia (AFC, SAT, Siemens, etc.). Several enterprises are preparing to release the DLC in Russia as well.
The architecture of the DLC equipment is a time division multiplexer with various user interfaces and a line interface for direct connection to fiber. Thus, it is ensured that a plurality of subscriber lines are combined into one high-speed digital stream arriving at the PBX (network node) via an optical cable.
The set of user interfaces typically includes an analog two-wire subscriber interface (ordinary telephone), an analog interface with E&M signaling, a digital interface (V.24 or V.35), an ISDN interface. Station interfaces provide for connection to analog exchanges (via subscriber's two-wire junction or E&M interface), digital exchanges (via E! junction with V.51 signaling or E3 junction with V.52 signaling). Naturally, it also provides for connection via ISDN interface and digital interface V.24/V.35 (to connect to a data network).
The line interfaces of modern DLC equipment can be divided into several groups:
- § An optical interface is required for direct connection to optical fibers (line speed is typically between 34 and 155 Mbps). For example, in the NATEKS 1100E system, the speed is 49.152 Mbps, reception and transmission are carried out separately over two fibers, the wavelength of the laser emitter is 1310 nm.
- § Electrical interface -- from E! (2 Mbps) to E3 (34 Mbps) - allows you to connect to high-speed networks that provide transparent transmission of digital streams (for example, to the SDH network). The electrical interface also allows you to connect equipment via HDSL paths or radio relay lines, and directly connect system elements at short distances (up to 1 km along E!)
Organization of a subscriber access network
Subscriber access network- a set of technical means for transmitting messages in the area from the subscriber device to the terminal station of the local telephone network;
Options for organizing subscriber access
In today's world of telecommunications, the factor of coexistence of standard and new technologies is becoming increasingly important. This situation is the basis for next generation NGN networks. User and signaling information is always transmitted via interfaces and predefined protocols.
Triple play technology provides simultaneous voice, video, Internet, data transmission. The technology is implemented using optical fiber in the subscriber line.
Interface heterogeneous devices. Interfaces always implement some kind of protocol.
The concept of an interface includes:
Hardware that connects various devices with each other or with the user (communication lines, interface devices, physical characteristics of the communication channel)
Software tools that provide communication between various devices between themselves or with the user (programs that provide information transfer between different users; data types; a list of available memory areas; a set of valid procedures and operations and their parameters)
Rules and algorithms on the basis of which software and hardware operate. (e.g. signal and data conversion methods)
Protocol are software and hardware designed to interface homogeneous devices. The protocol provides interaction between elements that are at the same hierarchical level, but in different network nodes.
The protocol is a set of rules for the interaction of the CU within the CSC and on the network, which determine:
An algorithm for the interaction of devices, programs, data processing systems, processes or users.
Network equipment addressing rules.
Codes used to represent data.
Information transfer rates.
Information transfer methods.
Message formats.
Rules for the formation of message packets.
Methods for detecting and correcting errors.
Methods of electrical connections.
Choice of message transfer route.
ISDN DIGITAL LINES
ISDN - (Integrated Services Digital Network) - integrated service digital networks. ISDN technology allows one physical line arrange some temporary channels
ITU-T has defined the following groups of ISDN subscriber devices:
TE1 - ISDN terminal. Terminals of this type are fully compatible with ISDN standards and are connected to the network via a 4-wire line, in which 3 time slots (TI) are organized: B, B, D.
TE2 is a non-ISDN terminal. A telephone set TA, facsimile, telex, videotex, PC are considered as such a terminal.
TA - terminal adapter for connecting terminals that are not compatible with ISDN. TA converts signals from other standards to the ISDN standard.
NT is a network termination that provides the following functions:
power supply to the subscriber unit,
maintenance of lines,
performance monitoring, synchronization,
multiplexing, switching and concentration,
resolving access conflicts.
A network termination can be a single physical NT equipment, or it can be divided into two categories of network terminations: NT1 and NT2, taking into account the categories of subscribers served.
(NT1 is a layer 1 network termination. (These are the levels of the reference model of open systems interconnection.) The functions of NT1 include supplying power to the subscriber unit, providing line maintenance, performance monitoring, synchronization, multiplexing, access conflict resolution.
NT2 - network ending of levels 2,3. Performs layer 2 and layer 3 protocol processing, multiplexing, switching and concentration, line maintenance, performance monitoring, access conflict resolution. As a functional block NT2 can be, for example, PBX, LAN.)
LT - CSC line termination to which ISDN line is connected. LT is an integral matching line kit.
ET - station termination of the CSC, which is a subscriber module for connecting ISDN subscribers. (for example, in S-12 this is the ISM module).
Interfaces at reference points:
Interface at point R
connects non-ISDN TE2 equipment to a TA terminal adapter.
Interface at point T associates a user equipment with an NT network termination, or the two kinds of network terminations NT1 and NT2.
Interface at point U is an interface between NT equipment and PSTN PBX equipment and provides:
linear coding of information for transmission over pairs of copper wires;
two-way exchange of information on any existing physical pairs of wires;
connection of ISDN subscribers using a two-wire scheme via NT.
Interface at point S provides connection of ISDN subscribers by 4-wire scheme without NT.
Interface at point V
(V5.1 and V5.2) provides the ability to share equipment from different manufacturers with various subscriber access systems, including wireless communication lines, fiber optic lines and copper cables
Currently, there are three main ways to improve the efficiency of the use of AL in the presence of analog switching systems:
- 1) the use of paired inclusion of two subscribers;
- 2) the inclusion of telephone sets TA according to the scheme with high-frequency multiplexing AL (AVU);
- 3) use of substations of analog automatic telephone exchanges.
Twin inclusion call the connection of two closely spaced subscriber terminals with different telephone numbers to one PBX subscriber line. As a rule, subscriber numbers differ only in the last or penultimate digit of the number. The peculiarity of this inclusion is that when the line is occupied by one of the subscribers, the terminal of the other is automatically turned off. A call from the PBX comes only to the telephone whose number was dialed. In the station part of the network (at the PBX) there are sets of paired devices (KSA), and in the subscriber part, separating diode circuits are mounted. The principle of operation of the equipment for paired inclusion of a telephone set (TA) is shown in Figure 3.1.
Rice. 3.1.
A set of paired devices performs a constant survey of subscribers by changing the polarity of the line with a frequency of 0.5 ... 1.0 Hz. The operation of the diode separation attachment is based on providing power to the SLT that occupied the subscriber line and blocking the power circuit of another SLT connected in parallel through the blocker. This is achieved by turning on blocking diodes so that the diodes of one TA are directed towards the diodes of another device. Therefore, voltage is applied to each device in turn. The subscriber who first picks up the handset seizes the line. At the same time, at the exchange, the station pairing device sets the polarity that provides power to the TA that occupied the line.
In paired telephones, the alternating voltage of the ringing signal is applied not relative to zero potential, but relative to the polarity of the supply voltage called by the SLT. AC signals (conversational or ringing) are passed by the diodes of only one of the two SLTs from which the call is received or to which the call is directed. This ensures call selectivity.
Subscriber high-frequency multiplexing system(AVU) on one AL allows organizing, in addition to the main unmodulated source signal with frequencies of 0.3 ... 3.4 kHz, another additional high-frequency channel. This channel is obtained by a single conversion of the original frequency band of the spoken signal into a linear band on transmission and inverse transformation on reception. Thus, when using AVU on one subscriber line, it is possible to transmit signals from two subscribers at the same time. Figure 3.2 shows the frequency spectra of the main channel, the signal through which is transmitted without conversion, and the channel formed by the AVU.

Rice. 3.2.
The main channel occupies a frequency band up to 3.4 kHz. For transmission over a high-frequency channel from SLT to PBX, a frequency of 28 kHz is used, and from PBX to SLT - a frequency of 64 kHz. With the help of these carriers, signals are formed, the spectra of which occupy mutually non-overlapping frequency ranges. At the same time, a signal is transmitted from the subscriber to the station in the range of 24.6 ... 31.4 (28 ± 3.4) kHz, and from the station to the subscriber - 60.6 ... 67.4 (64 ± 3.4) kHz. A carrier and two side frequencies, obtained by converting the original signal, are transmitted to the line. With this method, most of the power of the linear signal is wasted, but the construction of the system is simplified and cheaper as much as possible.
The AVU system (Fig. 3.3) consists of two filters for selecting the frequencies of the main channel (D-3.5), two filters for selecting the frequencies of the additional channel (K-20) and two blocks of high-frequency converters: station (VChS) and linear (VChL ). The AVU system has low reliability and poor communication quality (especially the high-frequency channel), which necessitates its replacement with digital systems.