Vulnerabilities in the control system of flash drives ESET NOD32 Antivirus
More recently I have researched reliability Device control in antivirus solutions from Kaspersky, in the article -. There it turned out to be quite full of holes in all positions, in every way with the controllers in question from SMI... And I didn't feel like digging further, because all the bottlenecks had already been dismantled.
With antivirus from ESET everything turned out to be much more interesting, which I will tell you about. In the article, we will largely compare the previously studied Kasperich With NOD32 Antivirus... The purpose of this action is to make you feel a noticeable difference, which in any case I felt.
ABOUT DEVICE CONTROL
The functionality here is clearly less than that of Kaspersky, but what we have works much better than the competitor.
The main disadvantages are the impossibility of blocking on the bus and a smaller list of the devices themselves subject to control:
– Disk drive
– CD / DVD
– USB Printer
– FireWire storage
– Bluetooth device
– Smart card reader
– Imaging device
– Modem
– LPT / COM port
– Portable device
– All device types – this item blocks everything from the list above.
METHODS TO BYPASS PROTECTION
In the course of experiments with GCD, controllers from such companies as:
– Alcor
– Innostor
– Phison
– Skymedi
– SMI
And only with the last two have at least some success been achieved.
But if we talk about the so-called white list of flash drives, then everything is even easier here than in Kaspersky since fewer variables are involved. Therefore, there will be much less unsuitable controller models.
List of methods:
1] SUBSTITUTION OF THE DATA OF THE FLASH DRIVE SO THAT THEY CORRESPOND TO THE WHITE LIST.
2] FIRMWARE IN FLOPPY DEVICE.
3] USING PRE-LOADING FILES THROUGH THE FIRMWARE.
In general, the methods are the same as for Kaspersky, only their implementation is very different.
WHITE LIST OF DEVICES
Unlike the same Kaspersky, which checks as many as 4 parameters ( VEN, DEV, SN, REV), NOD32 limited to only three:
– Manufacturer
– Model
– Serial number
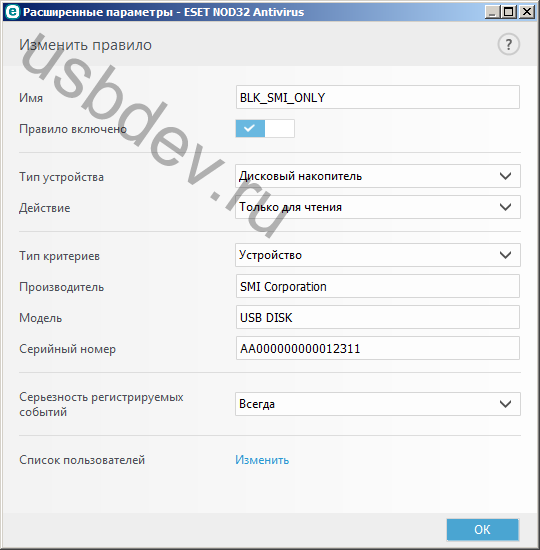
Moreover, the first two of them are not at all the same VEN and DEV which uses Casper... Those. this is not something that can be found in a familiar line Path to the device instance.
USBSTOR \ DISK & VEN_USBDEV & PROD_MYPENDRIVE & REV_1101 \ AA000000000012311 & 0
From this line with NOD32 only a common serial and no more. The audit is not presented in any of the two forms at all.
If you turn to the utility for polling controllers ChipGenius, then she interprets these parameters as follows:
Device Vendor: SMI Corporation
Device Name: USB DISK
Device Revision: 1101Manufacturer: USBDEV
Product Model: MyPendrive
Product Revision: 1101
From which we can conclude about the variables used by antivirus:
NOD32: Device Vendor and Device Name
KAV: Manufacturer, Product Model and Product Revision
Changing data for the controller SMI SM3261AB will look something like the one shown in the screenshot.
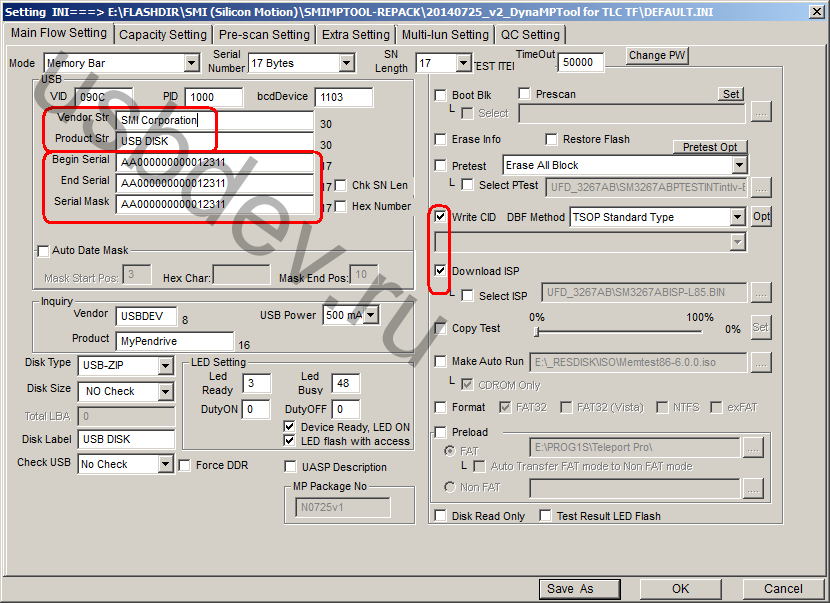
Those. the following lines are edited:
– Vendor Str
– Product Str
– Serial Mask
FLOPPY DEVICE
The floppy box is the weakest point in the products from ESET and it is this card that we will play in the future to achieve our goals. But for now, let's talk about a simple modification of the flash drive in Floppy-device.
Things are so that NOD32 in principle, it does not know how to block floppy disks, so you can safely sew a USB flash drive in FLOPPY-device and use it as much as you want.
I will not screen it here, if you really need it you can look in the article about Kaspersky or scroll a little lower, where in one of the schemes will be used FLOPPY-mode as intermediate.
HOW TO USE THE PRELOAD FUNCTION
It all depends on the controller model, so with Skymedi SK6221 everything goes smoothly and without any hesitation. When working with Skymedi the main thing is not to create CDROM- a partition on a USB flash drive, otherwise the production utility will stop recognizing it from under a computer with blocked devices through NOD32.
To do this, in the settings Skymedi Production Tool you need to activate the option Enable PreCopy and specify the folder that should be preloaded to disk.
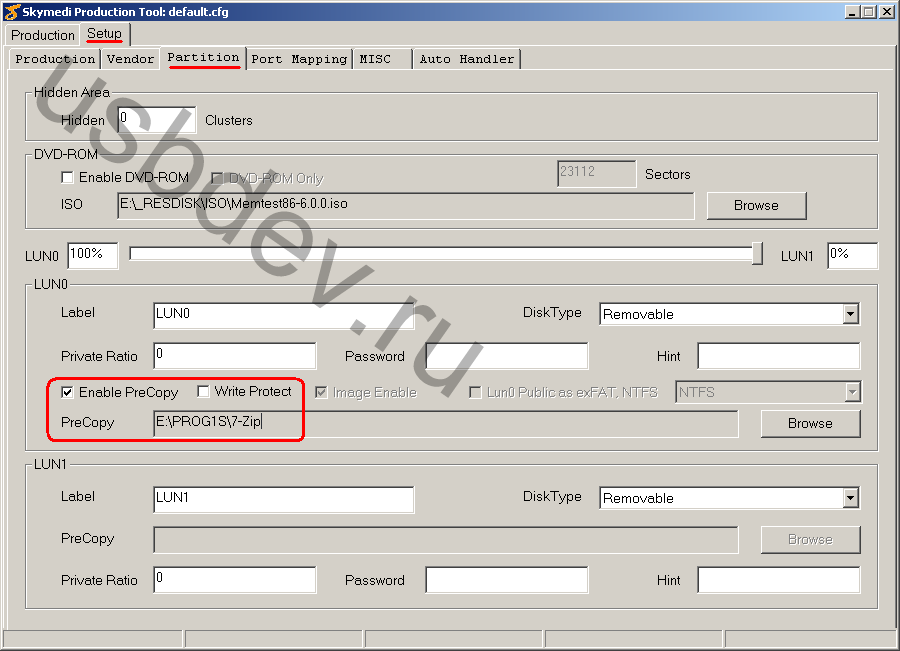
When flashing, the previous data will be lost, this is not a leaky trough from Kaspersky.
Have SMI-shek, who have shown their reliability in the experiment with Kaspersky, use in the forehead as an option PRELOAD will not work. The fact is that the flasher stubbornly refuses to see the flash drive, even with the service driver installed SMI Factory Driver.
But you can get around this limitation by using the previously created FLOPPY-section that is not able to block ESET NOD32... Those. HOUSES create FLOPPY-section, roll up the archive with the production utility on it, then on WORK you can already merge files.
Just in case, I will notice what to fit SMIMPTool quite real on a floppy disk 1.38MB... I conducted the experiment myself, shoved it SMI MPTool 2015 based on shell sm32Xtest_V36-7.exe v RAR-archive volume 1.13MB... True, I first had to remove all the firmware except those used for my flash drive, other unnecessary files and cut the service file to a minimum ForceFlash.SET... And in the end, you can bring the program in two passes, cutting the archive into two parts.
I'll tell you a little more, for those who are not in the subject, what settings and in what sequence are needed.
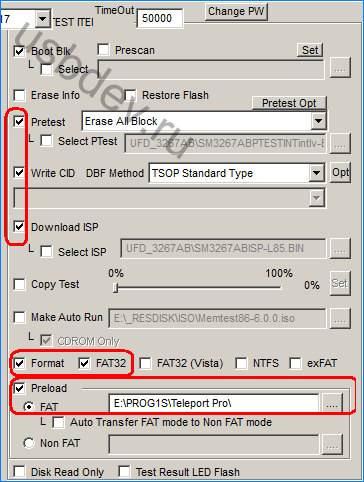
HOUSES, take the first screenshot, that is, on the first tab Main Flow Setting, activate:
– Pretest
– Write CID
– Download ISP
– Format and FAT32
In the tab Multi-lun Setting:
– Enable Floppy Support
– Floppy format
We flash and get a flash drive with two partitions: a regular large flash partition and a floppy drive.
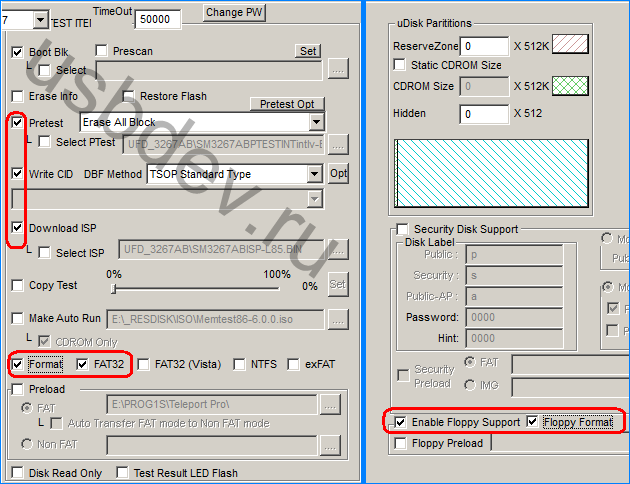
A USB flash drive, as a device, in this state is not able to block an antivirus for flashers NOD32... Although one can freely write-delete on FLOPPY-area, but we still cannot access the flash section by standard Windows- by means.
As long as there is a floppy partition on the flash drive, we can do in SMI MPTool with her, what we want. Because change simultaneously with floppy and PRELOAD- I categorically refused the flash drive option, then we have only one attempt at WORK merge files. Further HOUSES, you can either return the flash drive to its original form or prepare it for the second run.
On the WORK connect the flash drive, deactivate the parameters that respond to Floppy-device and turn on Preload-option, as shown in the screenshot below.
SMI MPTool does its job, but we enjoy the result.
CONCLUSION
Maybe tomorrow these instructions will not help to overcome NOD-antivirus, but firstly, you still have to live until tomorrow, and secondly, knowledge is not superfluous.
Know you can always consult me for free at.