Windows 7 kernel debug mode runtime. Windows Kernel Mode Debugging Tools
To debug the kernel, you need to connect to the computer using null modem cable or modem connection. The computer doing the debugging will be called “Host”, and the name “Target” will be given to the problem computer.
Both computers must be running the same version of Windows, and the symbol files for the Target computer must be installed on the Host computer. The symbol files are provided on the Windows installation CD in the Support\Debug directory.
To enable debugging, you need to make changes to the BOOT.INI file on the Target computer.
1. Change the attributes of the BOOT.INI file:
attrib c:\boot.ini -r -s
2. Edit this file and to the line Windows startup add the /debug option (to tell the system to load a kernel debugger into RAM when Windows boot). Additional options are /Debugport to tell the system which COM port to use (COM2 by default) and /Baudrate to specify the baud rate (default is 19200 baud, but 9600 is better). For example:
multi(0)disk(0)rdisk(0)partition(0)\WINDOWS="Windows NT" /debug /debugport=com2 /baudrate=9600
3. Save the file.
4. Set the previous attributes of the BOOT.INI file:
attrib c:\boot.ini +r +s
IN this example the Target computer allowed the connection through the COM2 port at a speed of 9600 bps.
The Host computer must be configured with the settings required for debugging. In addition, symbol files must be installed. To install them, navigate to the \support\debug directory on the installation CD and enter the following command:
expndsym
For example:
expndsym f: d:\symbols
Installation may take some time. Remember that if service packs have been installed on the Target computer, the symbol files of those packages must also be installed on the Host computer. Symbol files for service packs can be downloaded from the Microsoft website.
The next step is to set up the environment variables needed for debugging, such as variables specifying the location of symbol files, and so on. The following is a description of these variables.
Description of system variables
The definition of these variables can be placed in a batch file in order to avoid typing the appropriate commands on every boot:
echo off
set _nt_debug_port=com2
set _nt_debug_baud_rate=9600
set _nt_symbol_path=d:\symbols\i386
set _nt_log_file_open=d:\debug\logs\debug.log
Now you need to copy the kernel debugging software, which is located in the support\debug\ directory<процессор>on the installation CD (support\debug\I386). The easiest way is to copy the entire directory, because it is small (about 2.5 MB). For the I386 platform, a debugger is used, which is supplied as the I386KD.EXE file. The debugger is launched using the I386KD command. To enter a command, press the key combination
The term "kernel debugging" means examining the kernel's internal data structure and/or stepping through functions in the kernel. This debugging is a very useful way to explore the internal Windows devices, because it allows you to get displays of internal system information that is not available using any other means, and gives you a clear view of the progress of the code in the kernel.
Before considering various ways kernel debugging, let's examine the set of files that will be needed to perform any kind of such debugging.
Kernel Debugging Symbols
Symbol files contain the names of functions and variables, as well as the schema and format of data structures. They are generated by the linker program and are used by debuggers to refer to these names and to display them during a debug session. This information is usually not stored in binary because it is not needed when the code is executed. This means that without it, the binary becomes smaller and runs faster. But it also means that when debugging, you need to make sure that the debugger has access to the symbol files associated with the binary images that are referenced during the debugging session.
To use any kernel-mode debugging tool for research purposes internal device Windows kernel data structures (list of processes, thread blocks, list of loaded drivers, memory usage information, etc.) you need correct files symbols and, at a minimum, the symbol file for the binary kernel image, Ntoskrnl.exe. Symbol table files must match the version of the binary image from which they were extracted. For example, if installed Windows package Service Pack or some fix that updates the kernel, you need to get the symbol files updated accordingly.
Download and install symbols for various versions Windows is not difficult, but it is not always possible to update the symbols for corrections. Easiest to get desired version symbols for debugging by accessing a dedicated Microsoft symbol server using special syntax for the symbol path specified in the debugger. For example, the following symbol path causes the debugger to download symbols from an Internet symbol server and store a local copy in c:\symbols:srv*c:\symbols*http://msdl.microsoft.com/download/symbols
Detailed instructions for using the character server can be found in the Debugging Tools help file or on the Internet at http://msdn.microsoft.com/en-us/windows/hardware/gg462988.aspx.
This series of articles came about for two reasons. Firstly, I like working with the project HackSysExtremeVulnerableDriver. Second, I got a lot of wishes to highlight this topic.
All the code used in writing this series is in my .
In this series of articles, we will look at writing kernel-level exploits in Windows. It is important to note that we will be dealing with known vulnerabilities and there is no need for reverse engineering (at least not for a driver).
It is assumed that after reading all the articles, you will know all the most common classes of breaches and methods of exploitation, as well as be able to port exploits from x86 architecture to x64 architecture (if possible) and familiarize yourself with the new protection methods in Windows 10.
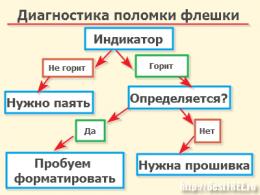
Kernel debug scheme
Unlike user-level debugging, when a single process is paused, the entire system is involved at the kernel level, and we will not be able to use this method. Accordingly, a separate debugging machine is needed that can communicate with the system where the kernel is being debugged, view memory and kernel structures, and also catch system crashes.
Additional material for study:
Exploitation of kernel vulnerabilities
This process is much more fun than user-level exploitation J.
The main goal is to achieve privileged execution in the context of the kernel. And then everything depends on our imagination, starting from a feast with homemade beer and ending with the introduction of state-sponsored malware.
In general, our task is to get a shell with system privileges.
Topics of articles in this series
- Part 1: Setting up the working environment
- Configuring three virtual machines and a system that will act as a debugger.
- Configuring the WinDBG debugger.
- Part 2: Payloads
- Explore the most common payloads. Subsequent parts will address specific vulnerabilities and provide links to this article if necessary.
- The rest of the parts.
- Consideration of vulnerabilities.
Development life cycle of a kernel-level exploit
- Finding a vulnerability. This topic will not be covered in this series, since we already know exactly where the gaps are.
- Intercepting the flow of execution. Some vulnerabilities involve code execution, some have additional requirements.
- Privilege Expansion. The main goal is to get a shell with system privileges.
- Restoring the flow of execution. Unhandled exceptions at the kernel level cause the system to crash. If you are not going to write an exploit for a DoS attack, you should consider this fact.
Types of target systems
We will work with vulnerabilities in the following systems (the specific version is not critical):
- Win7 x86 VM
- Win7 x64 VM
- Win10 x64 VM
Let's start with the x86 architecture, and then we will port the exploit to the Win7 x64 system. Some exploits will not run on Win10 machines due to the presence of new protections. In this case, we will either change the logic of the exploit, or we will use a completely different approach.
Software used:
- Hypervisor (many options).
- Windows 7 x86 VM
- Windows 7 x64 VM
- Windows 10 x64 VM
Setting up systems for debugging
The debug systems we will be interacting with are designed to load a vulnerable driver. Crashes will often occur on these machines, since most exceptions in the kernel contribute to this sort of thing. It is necessary to allocate enough random access memory for these systems.
On each machine that will be debugged, you need to do the following:
- Inside the VirtualKD directory, run the target\vminstall.exe file. A new boot entry will be added and debugging functions and automatic connection to the VirtualKD server installed on the system acting as the debugger will be available.
In the case of the Windows 10 VM, you must enable the test signing mode, which allows unsigned drivers to be loaded into the kernel.
After executing the bcdedit /set testsinging on command and rebooting, "Test Mode" will appear on the desktop.
Short description HEVD module
The DriverEntry procedure is the starting one for each driver:
NTSTATUS DriverEntry(IN PDRIVER_OBJECT DriverObject, IN PUNICODE_STRING RegistryPath) (
UINT32 i = 0;
PDEVICE_OBJECT DeviceObject = NULL;
NTSTATUS Status = STATUS_UNSUCCESSFUL;
UNICODE_STRING DeviceName, DosDeviceName = (0);
UNREFERENCED_PARAMETER(RegistryPath);
PAGED_CODE();
RtlInitUnicodeString(&DeviceName, L"\\Device\\HackSysExtremeVulnerableDriver");
RtlInitUnicodeString(&DosDeviceName, L"\\DosDevices\\HackSysExtremeVulnerableDriver");
// Create the device
Status = IoCreateDevice(DriverObject,
0,
&DeviceName,
FILE_DEVICE_UNKNOWN,
FILE_DEVICE_SECURE_OPEN,
false,
&DeviceObject);
- This procedure contains a call to the IoCreateDevice function containing the name of the driver that we will use during communication.
- Will be added to the DriverObject object desired structures and function pointers.
- What matters to us is the function pointer associated with the procedure DriverObject->MajorFunction , which is responsible for handling IOCTL (I / O Control; input / output control);
- In HEVD, this function is called IrpDeviceIoCtlHandler , which is a large conditional expression with many branches for each IOCTL. Each vulnerability has a unique IOCTL.
Example: HACKSYS_EVD_IOCTL_STACK_OVERFLOW is an IOCTL used to trigger a stack overflow vulnerability.
This concludes the first part. In the next article, we will talk about payloads. On the this moment only the token-stealing payload is available, which will be used in the third part.
P.S. I understand that there are many subtleties and problems that you may encounter. Since this cycle focuses on exploit development, you will have to solve all the problems along the way yourself. However, you can ask any questions you have in the comments.
- The authors:
Barinov S.S., Shevchenko O.G.
- Year:
- A source:
Informatics and Computer techologies/ Materials of the VI International Scientific and Technical Conference of Students, Postgraduates and Young Scientists - November 23-25, 2010, Donetsk, DonNTU. - 2010. - 448 p.
annotation
Brought comparative analysis user mode and kernel mode debugging as applied to the operating system Microsoft Windows, the differences and problems of organizing the debugging of the latter are highlighted. Based on the results obtained, the main requirements for the construction of kernel-mode debuggers in the case of emergency and interactive debugging are formulated. Analyzed existing solutions for compliance with the requirements. In particular, special attention is paid to the Microsoft Windows Debugger.
Main part
Debugging is the process of identifying and eliminating the causes of errors in software. In some projects, debugging takes up to 50% of the total development time. Debugging can be greatly simplified by using specialized tools that are constantly being improved. The main such tool is the debugger, which allows you to control the execution of software, monitor its progress and interfere with it. Kernel debugging tools are primarily used by driver developers.
The application software development toolkit offers the programmer a wide range of possibilities. Any integrated development environment also includes the ability to debug without the need for third-party utilities. If we are talking about system software and driver development in particular, then due to its specificity, the development process is extremely difficult and little automated. All development phases, including debugging, are separate. Each of them requires special conditions: the programming code is written on a full-fledged computer system, debugging - on a debugging system, testing - depending on the circumstances, etc. The kernel-mode debugger itself is more difficult to learn and, accordingly, less friendly.
In general, we can talk about the lack of kernel debugging tools. While these tools are available, alternatives are often not discussed. For example, the Microsoft Windows Debugger has an entry threshold that is too high. Many programmers talk about the first negative experience when they get acquainted with it, and most of its features remain unclaimed.
Based on the structure of the virtual address space, if an application makes a mistake that causes the application to write data to an arbitrary memory location, then the application will only damage its own memory and will not affect the operation of other applications and the operating system. Whereas kernel mode code is able to corrupt important structures data operating system, which will inevitably lead to a general failure. An inefficiently written driver can also cause serious degradation of the entire operating system.
- Modern debuggers provide the following basic functions:
- level debugging source code;
- execution management;
- viewing and changing memory;
- viewing and changing the contents of processor registers;
- call stack view.
To facilitate work with disassembled code, so-called. debug symbols. During the operation of the linker, in addition to the image of the executable file, a data file can also be created containing information that is not required when executing the program, but is extremely useful when debugging it: the names of functions, global variables, and descriptions of structures. Debugging symbols are available to everyone executable files operating room Windows systems.
Execution control refers to the ability to interrupt and resume the execution of program code upon reaching a given instruction in the program code. If the program code is executed in step by step mode- an interrupt occurs for each token of the programming language or when exiting a subroutine. With free execution, execution interruption occurs in predetermined sections of code - places where breakpoints are set.
Aborting kernel-mode code raises the following dilemma. The debugger uses the user interface to interact with the programmer. Those. at least the visible part of the debugger runs in user mode and naturally uses the interface to build it application programming(Windows API), which in turn relies on kernel-mode modules. Thus, suspending kernel-mode code can lead to a deadlock: the system will become unresponsive to the user.
Parts of the debugger must also run in kernel mode to access kernel memory. This leads to two problems at once, which are an obvious consequence of the organization of memory in the protected mode of the processor.
The first problem concerns the translation of virtual memory addresses. Drivers constantly interact with user-mode applications by accessing their memory. The Windows operating system translates virtual addresses into physical ones, guided by the concept of flow context. Thread context - a structure that reflects the state of the thread and includes, in particular, a set of registers and some other information. When control is transferred to another thread, a context switch occurs that saves information about one thread and restores information about another. Switching the context of a thread to a thread of another process also switches the page directory used to translate virtual addresses into physical ones.
The peculiarity lies in the fact that when dispatching system calls The Windows operating system does not switch context. This allows kernel-mode code to use user-mode virtual addresses.
The situation is different when interrupt dispatching or executing system threads. An interrupt can occur at any time, so there is no way to predict which thread context will be used. System threads, on the other hand, do not belong to any process and cannot translate user-mode virtual addresses. It follows that user-mode memory cannot be accessed in these situations.
The second problem is relocatable memory access. Most of the information in memory is movable and can be moved from physical memory to HDD to a page file. If a page is accessed that is not in physical memory, the processor will normally generate a Page Fault interrupt, which will be handled by the memory manager, and as a result the page will be read from the page file and loaded into physical memory.
The described behavior is broken if the debugger code is forced to use high level interrupt requests (interrupt request levels, IRQL). If the IRQL is equal to or greater than the IRQL of the memory manager, the latter will not be able to load the missing page, because the operating system will block the Page Fault interrupt. This will crash the operating system.
Debugging is usually divided into interactive and emergency. With interactive local debugging, the debugger runs on the same system as the debug object. In interactive remote debugging, the debugger and the debug object run on different systems. When debugging the kernel code, the system must be controlled from the first stages of its boot, when the network is not yet functioning, so simple serial interfaces such as COM, FireWire, USB are used to connect systems. Recently, thanks to the trends in the development of software virtualization at different levels of abstraction, more and more often attract virtual machines. The guest OS acts as the debugged OS, the host OS includes a debugger user interface.
Therefore, emergency debugging does not require a debugging tool to be installed on the test computer. The distribution of the Windows operating system includes mechanisms to implement emergency debugging. Before rebooting, the operating system can save information about its state, which the developer can analyze and find out the cause. This information saved to a file is called a memory dump.
The main kernel-mode debugging tools are provided by the manufacturer of the Windows operating system as part of the freely distributed Debugging Tools for Windows package. Tools include graphical and console debuggers WinDbg and KD, respectively (hereinafter referred to as Windows Debugger). The work of these debuggers is based on the mechanisms provided by the developers of the operating system and embedded in its kernel.
The main mode for the Windows Debugger is command interpreter mode. Thanks to modular structure, along with supplied developers Windows commands Debugger supports third party modules called extensions. In fact, most of the built-in commands are also formatted as extensions.
Windows Debugger is focused on remote interactive and emergency debugging, using which all its capabilities are revealed. At the same time, full-fledged local interactive debugging is not supported: the debugger only allows you to view some kernel structures.
There is an extension for Windows Debugger called LiveKD, created by Mark Russinovich, which implements local interactive debugging in a sense. LiveKD creates a memory dump on the go working system and use it for debugging.
Debugging Tools for Windows is regularly updated and supports all modern Windows operating systems.
The SoftICE kernel debugger, released by Compuware in the DriverStudio software package, has traditionally acted as an alternative to the Debugging Tools for Windows package. A distinctive feature of SoftICE was the implementation of local interactive debugging on a supported hardware. The debugger could almost completely control the operation of the operating system.
As of April 3, 2006, the DriverStudio product family has been discontinued due to "many technical and business issues, as well as general market conditions." latest version The supported operating system is Windows XP Service Pack 2. Service packs generally do not change the operating system application interface, but system call numbers and other undocumented information may change. SoftICE debugger relied on hardcoded addresses internal structures data. As a result, with the release of Service Pack 3, compatibility was broken. Obviously, later versions of the Windows operating system are also not supported.
Syser Kernel Debugger was created by a small Chinese company Sysersoft as a replacement for the SoftICE debugger. The first final version was released in 2007. Like SoftICE, Syser Kernel Debugger is capable of interactive debugging on a running system. Only 32-bit editions of modern Windows versions.
Windows Debugger is currently the main tool among developers of kernel modules. It is also used by the Windows operating system kernel development team.
ChPF OELPFPTSCHE HLBBOYS RP TBVPFE U PFMBDLPK SDTB U BCHBTYKOSHCHNY DBNRBNY RBNSFY. LBL RTBCHYMP, CHBN OKHTSOP VKHDEF ЪBDBFSH PDOP YЪ HUFTPKUFCH RPDLBYULY, RETEYUMEOOOSCHI CH ZHBKME /etc/fstab. uVTPU PVTBCHBNY RBNSFY ABOUT KHUFTPKUFCHB, OE SCHMSAEYEUS KHUFTPKUFCHBNY RPDLBYULY, OBRTYNET, MEOFSHCH, CH DBOOSCHK NPNEOF OE RPDDETSYCHBAFUS.
Note: YURPMSHЪKhKFE LPNBODH dumpons (8) DMS HLBBOYS SDTH NEUFB, ZDE OHTSOP UPITBOSFSH BCHBTYKOSHCHE DBNRSHCH. rPUME OBUFTPCLY RP LPNBODE swap (8) TBDEMB RPDLBYULY DPMTSOB VSHCHFSH CHSHCHCHBOB RTPZTBNNB dumpon . PVSHYUOP LFP CHSHCHRPMOSEPHUS BDBOYEN RETENEOOPK dumpdev H JBKME rc.conf (5). eUMMY BDBOB LFB RETENEOOBS, FP RPUME UVPS RTY RETCHPK NOPZPRPMSHPCHBFEMSHULPK RETEEBZTHЪLE VHDEF BCHFPNBFYUEULY BRHEEO RTPZTBNNB savecore(8). pOB UPITBOYF BCHBTYKOSHK DBNR SDTB W LBFBMPZ, JBDBOOSCHK H RETENEOOPC dumpdir JBKMB rc.conf . rp HNPMYUBOYA LBFBMPZPN DMS BCHBTYKOSHCHI DBNRPC SCHMSEFUS /var/crash .
MYVP CH NPCEFE ЪBDBFSH HUFTPKUFCHP DMS UVTPUB PVTBYB RBNSFY SCHOP Yuete RBTBNEFT dump CH UFTPL config LPOZHJZHTBGYPOOPZP ZHBKMB CHBYEZP SDTB. fBLPK URUPUPV YURPMSHЪPCHBFSH OE TELPNEODHEFUS Y PO DPMTSEO YURPMSHЪPCHBFSHUS, FPMSHLP EUMY CHSH IPFYFE RPMHYUBFSH BCHBTYKOSHCHE PVTBJSCH RBNSFY SDTB, LPFPTPE BCHBTYKOP ЪBCHETYTBYBKHUBHUCH.
Note: dBMEE FETNYO gdb POBUBEF PFMBDUYL gdb , BRHEEOOSCHK H ``TETSYNE PFMBDLY SDTB "". RETEIPD H FFPF TETSIN DPUFYZBEFUS BRHULPN gdb U RBTBNEFTPN -k . h TETSYNE PFMBDLY SDTB gdb YЪNEOSEF UCHPЈ RTYZMBYOEOYE ABOUT (kgdb) .
tip: eUMMY CHSH YURPMSHHEFE FreeBSD CHETUYY 3 YMY VPMEE TBOOAA, CHSH DPMTSOSCH CHSHCHRPMOYFSH HUEYUEOYE PFMBDPYUOPZP SDTB LPNBODPK strip, B OE HUFBOBCHMYCHBFSH VPMSHYPE PFMBDPYUOPE SDTP:
# cp kernel kernel.debug # strip -g kernel
ffpf ybz oe fbl hts y eepvipdyn, op telpneodhen. (PE FreeBSD 4 J VPMEE RPDOYI TEMYBI FPF YBZ CHSCHRPMOSEFUS BCHFPNBFYYUEULY H LPOGE RTPGEUUB RPUFTPEOYS SDTB make.) LPZDB RAS HUEYUEOP, BCHFPNBFYYUEULY YMY RTY RPNPEY LPNBOD CHSCHYE, BL NPTSEFE HUFBOPCHYFSH EZP PVSCHYUOSCHN PVTBPN, OBVTBCH make install.
ъBNEFSHFE, UFP CH UVBTSCHI CHETUYSI FreeBSD (DP 3.1, OE CHLMOYUBS FFPF TEMY), YURPMSH'HEFUS SDTB CH ZHPTNBFE a.out, RPFPPNH YI FBVMYGSCH UYNCHPMCH DPMTSOSH TBURPMBZBFSHUS RBNSFPSOOP. at VPMSHYPK FBVMYGEK UYNCHPMCH CHOE HUEYUEOOOPN PFMBDPYUOPN SDTE LFP YЪMYYOSS FTBFB. rPUMEDOYE TEMYJSHCH FreeBSD YURPMSHJHAF SDTB CH JPTNBFE ELF, HERE EFP OE SCHMSEFUS RTPVMENPK.
eUMY BL FEUFYTHEFE OPCHPE RAS, ULBTSEN, OBVYTBS YNS OPCHPZP SDTB RTYZMBYEOYY BZTHYUYLB W, OP CHBN OHTSOP BZTHTSBFSH J TBVPFBFSH have DTHZYN SDTPN, YUFPVSCH UOPCHB CHETOHFSHUS A OPTNBMSHOPNH ZHHOLGYPOYTPCHBOYA, BZTHTSBKFE EZP FPMSHLP B PDOPRPMSHPCHBFEMSHULPN TETSYNE RTY RPNPEY ZHMBZB -s, HLBSCHCHBENPZP RTY BZTHLE, B UBFEN CHSHCHRPMOYFE FBLIE YBZY:
# fsck -p # mount -a -t ufs # so your filesystem for /var/crash is writable # savecore -N /kernel.panicked /var/crash # exit # ...to multi-user
uFB RPUMEDPCHBFEMSHOPUFSH HLBSCHCHBEF RTPZTBNNE savecore(8) ABOUT YURPMSH'PCHBOYE DTHZPZP SDTB DMS Y'CHMEYUEOYS UINCHPMYUEULYI YNEO. yOBYUE POB VHDEF YURPMSHЪPCHBFSH SDTP, TBVPFBAEEEE CH DBOOSCHK NPNEOF Y, ULPTEE CHUEZP, OYUEZP OE UDEMBEF, RPFPNH UFP BCHBTYKOSHCHK PVTB RBNSFY Y Uinchpmshch SDTB VHDHF PFMYUB.
b FERETSH, RPUME UVTPUB BCHBTYKOPZP DBNRB, RETEKDYFE H LBFBMPZ /sys/compile/WHATEVER Y BRHUFYFE LPNBODH gdb -k . y RTPZTBNNSC gdb UDEMBKFE CHPF UFP:
Symbol-file kernel.debug exec-file /var/crash/kernel.0 core-file /var/crash/vmcore.0 DTHZPK RTPZTBNNPK.
ChPF TsHTOBM LPNBOD UEBOUB TBVPFShch gdb, YMMAUFTYTHAEYK LFH RTPGEDHTX. dMYOOSH UFTPLY VSCHMY TBPTCHBOSH DMS HMHYUYOYS YUYFBVEMSHOPUFY Y DMS HDPVUFCHB UFTPLY VSCHMY RTPOHNETPCHBOSHCH. CHUE PUFBMSHOPE SCHMSEFUS FTBUUYTPCHLPK PYYVLY, TEBMSHOP CHPOYLOKHCHYEK CHP CHTHENS TBVPFSCH OBD DTBCCHETPN LPOUPMY pcvt.
1:Script started on Fri Dec 30 23:15:22 1994 2: # cd /sys/compile/URIAH 3: # gdb -k kernel /var/crash/vmcore.1 4:Reading symbol data from /usr/src/ sys/compile/URIAH/kernel ...done. 5:IdlePTD 1f3000 6:panic: because you said to! 7:current pcb at 1e3f70 8:Reading in symbols for ../../i386/i386/machdep.c...done. 9: (kgdb) where 10:#0 boot (arghowto=256) (../../i386/i386/machdep.c line 767) 11:#1 0xf0115159 in panic () 12:#2 0xf01955bd in diediedie ( ) (../../i386/i386/machdep.c line 698) 13:#3 0xf010185e in db_fncall () 14:#4 0xf0101586 in db_command (-266509132, -266509516, -267381073) 15:#0 0x10101 db_command_loop () 16:#6 0xf01040a0 in db_trap () 17:#7 0xf0192976 in kdb_trap (12, 0, -272630436, -266743723) 18:#8 0xf019d2eb in trap_fatal (...) 19:#9 0xfault19 ...) 20:#10 0xf019cb2f in trap (...) 21:#11 0xf01932a1 in exception:calltrap () 22:#12 0xf0191503 in cnopen (...) 23:#13 0xf0132c34 in spec_open () 24: #14 0xf012d014 in vn_open () 25:#15 0xf012a183 in open () 26:#16 0xf019d4eb in syscall (...) 27: (kgdb) up 10 28:Reading in symbols for ../../i386/i386 /trap.c...done. 29:#10 0xf019cb2f in trap (frame=(tf_es = -260440048, tf_ds = 16, tf_\ 30:edi = 3072, tf_esi = -266445372, tf_ebp = -272630356, tf_isp = -27\ 31:2630 266427884, TF_Edx = 12, TF_ECX = -266427884, TF \ 32: _EAX = 64772224, TF_TRAPNO = 12, TF_ERR = -272695296, TF_EIP = -26 \ 33: 6672343, TF_CS = -266469368, TF_EFLAGS = 66066, TF_ESP = 3072, tf_\ 34:ss = -266427884)) (../../i386/i386/trap.c line 283) 35:283 (void) trap_pfault(&frame, FALSE); 36: (kgdb) frame frame->tf_ebp frame->tf_eip 37:Reading in symbols for ../../i386/isa/pcvt/pcvt_drv.c...done. 38:#0 0xf01ae729 in pcopen (dev=3072, flag=3, mode=8192, p=(struct p\ 39:roc *) 0xf07c0c00) (../../i386/isa/pcvt/pcvt_drv.c line 403) 40:403 return ((*linesw.l_open)(dev, tp)); 41: (kgdb) list 42:398 43:399 tp->t_state |= TS_CARR_ON; 44:400 tp->t_cflag |= CLOCAL; /* cannot be a modem (:-) */ 45:401 46:402 #if PCVT_NETBSD || (PCVT_FREEBSD >= 200) 47:403 return ((*linesw.l_open)(dev, tp)); 48:404 #else 49:405 return ((*linesw.l_open)(dev, tp, flag)); 50:406 #endif /* PCVT_NETBSD || (PCVT_FREEBSD >= 200) */ 51:407 ) 52: (kgdb) print tp 53:Reading in symbols for ../../i386/i386/cons.c...done. 54:$1 = (struct tty *) 0x1bae 55: (kgdb) print tp->t_line 56:$2 = 1767990816 57: (kgdb) up 58:#1 0xf0191503 in cnopen (dev=0x00000000, flag=3, mode=8192 , p=(st\ 59:ruct proc *) 0xf07c0c00) (../../i386/i386/cons.c line 126) 60: return ((*cdevsw.d_open)(dev, flag, mode, p) ); 61: (kgdb) up 62:#2 0xf0132c34 in spec_open () 63: (kgdb) up 64:#3 0xf012d014 in vn_open () 65: (kgdb) up 66:#4 0xf012a183 in open () 67: (kgdb) up 68:#5 0xf019d4eb in syscall(frame=(tf_es=39, tf_ds=39, tf_edi=\69:2158592, tf_esi=0, tf_ebp=-272638436, tf_isp=-272629788, tf\ 70:_ebx,= = 1, tf_ecx = 0, tf_eax = 5, tf_trapno = 582, \71:tf_err = 582, tf_eip = 75749, tf_cs = 31, tf_eflags = 582, tf_esp \ 72 := -272638456, tf_ss = 39)) (. ./../i386/i386/trap.c line 673) 73:673 error = (*callp->sy_call)(p, args, rval); 74: (kgdb) up 75:Initial frame selected; you cannot go up. 76: (kgdb) quit 77: # exit 78:exit 79:80:Script done on Fri Dec 30 23:18:04 1994
lPNNEOFBTYY L CHSHCHYERTYCHEDEOOOPNKH TsHTOBMH:
UFTPLB 6:
yFP DBNR, CHJSFC RTY RPNPEY DDB (UNPFTY OYCE), RPFPNH LPNNEOFBTYK L BCHBTYKOPNH PUFBOPCH YNEEF YNEOOP CHYD ``because you said to! PDOBLP YOBYUBMSHOPK RTYUYOPK RETEIPDB CH DDB VSCHMB BCHBTYKOBS PUFBOPCHLB RTY CHPOYOLOPCHEOYA PYYVLY UFTBOIGSC RBNSFY.
UFTPLB 20:
ffp NEUFPOBIPTSDEOYE JHOLGYY trap() H FTBUUYTPCHLE UFEBL.
UFTPLB 36:
rTYOHDYFEMSHOPE YURPMSH'PCHBOYE OPCHPK ZTBOYGSCH UFEBL; FERESH FF OE OHTSOP. RTEDRPMBZBEFUUS, UFP ZTBOYGSC UFELB HLBSCCHCHBAF ABOUT RTBCHIMSHOPE TBURPMPTSEOYE, DBTSE CH UMHYUBE BCHBTYKOPZP PUFBOPCHB. zMSDS ABOUT UFTPLH YUIPDOPZP LPDB 403, NPTsOP ULBBFSH, UFP CHEUSHNB CHETPSFOP, UFP MYVP CHYOPCHBF DPUFHR RP HLBBFEMA ``tp "", MYVP VSCHM CHSHHIPD IB ZTBOYGSCH NBUUYCHB.
UFTPLB 52:
RPIPTSE, UFP CHYOPCHBF HLBBFEMSH, OP BY SCHMSEFUS DPRHUFYNSCHN BDTEUPN.
UFTPLB 56:
pDOBLP, PYUECHIDOP, UFP ON HLBSCHCHBEF ABOUT NHUPT, FBL UFP NSC OBYMY GENERAL PYYVLH! (DMS FEI, LFP OE OBBLPN U YFPK YUBUFSHHA LPDB: tp->t_line UMKhTSYF DMS ITBOOEOYS TETSYNB LBOBMB LPOUPMSHOPZP HUFTPKUFCHB, Y LFP DPMTSOP VShFSH DPUFBFPYuOP NBMEOSHLPE GEMPE YUYUMP.)