What are computer viruses and their types. Malware and viruses (macro viruses, stealth and polymorphic viruses)
In fact, macro viruses are not an independent "species", but just one of the varieties of a large family of malicious programs - script viruses. Their isolation is connected only with the fact that it was macroviruses that laid the foundation for this entire family, besides, viruses “imprisoned” under Microsoft programs Office, have received the most distribution of the entire clan. It should also be noted that script viruses are a subgroup of file viruses. These viruses are written in various scripting languages (VBS, JS, BAT, PHP, etc.).
A common feature of script viruses is their attachment to one of the "built-in" programming languages. Each virus is tied to a specific "hole" in the protection of one of Windows programs and is not independent program, but a set of instructions that force the generally harmless "engine" of the program to perform destructive actions that are not characteristic of it.
As in the case of Word documents, the use of microprograms (scripts, Java applets, etc.) in itself is not a crime - most of them work quite peacefully, making the page more attractive or more convenient. chat, Guest book, voting system, counter - our pages owe all these conveniences to microprograms - "scripts". As for Java applets, their presence on the page is also justified - they allow, for example, to display a convenient and functional menu that unfolds under the mouse cursor ...
Conveniences are conveniences, but do not forget that all these applets and scripts are real, full-fledged programs. Moreover, many of them are launched and work not somewhere, on an unknown server, but directly on your computer! And by injecting a virus into them, the page creators will be able to access the content of your hard drive. The consequences are already known - from a simple theft of a password to formatting a hard drive.
Of course, you will have to deal with "killer scripts" a hundred times less than with ordinary viruses. By the way, in this case there is little hope for ordinary antiviruses, however, a malicious program opened along with the page will have to overcome the protection of the browser itself, the creators of which are well aware of such tricks.
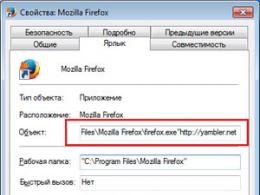
Setting the security level Internet Explorer.
Let's go back for a moment to Internet settings Explorer - namely in the menu Tools / Internet Options / Security. Internet Explorer offers us several levels of security. In addition to the standard level of protection (Internet zone), we can strengthen (Restrict zone) or weaken our vigilance (Trusted sites zone). By clicking the Custom button, we can manually adjust the browser's protection. However, most script viruses are distributed via email (such viruses are often referred to as "Internet worms"). Perhaps the brightest representatives of this family are the LoveLetter and Anna Kournikova viruses, whose attacks occurred in the 2001-2002 season. Both of these viruses used the same technique, based not only on weak protection operating system, but also on the naivety of users.
We remember that in most cases the carriers of viruses are e-mail messages containing attachments. We also remember that a virus can penetrate a computer either through programs (executable files with *.exe, *.com. extensions) or through Microsoft documents office. We also remember that from the side of pictures or sound files, no trouble seems to threaten us. And therefore, having unexpectedly dug out a letter in the mailbox with a picture attached to it (judging by the file name and extension), we immediately joyfully launch it ... And we find out that a malicious virus “script” was hidden under the picture. It’s good that we detect it immediately, and not after the virus has managed to completely destroy all your data.
The trick of the creators of the virus is simple - the file that seemed to us a picture had a double extension! For example, AnnaKournikova.jpg.vbs
It is the second extension that is the true file type, while the first is just part of its name. And since the Windows vbs extension is well known, she, without hesitation, hides it from the eyes of users, leaving only the name AnnaKournikova.jpg on the screen.
And Windows does this with all registered file types: the permission is dropped, and the icon should indicate the file type. Which, alas, we rarely pay attention to.
Nice trap, but easy to spot: the "double expansion" trick doesn't work if we activate the file type display mode beforehand. This can be done using the Folder Options menu in the Panel. Windows controls: Click this icon, then open the View tab and uncheck Hide extensions for known file types.
Remember: only a few types of files are allowed as an "attachment" to an email. txt, jpg, gif, tif, bmp, mp3, wma files are relatively safe.
And here is a list of unconditionally dangerous file types:
- § asx com inf msi
- § bas cpl ins pif
- § bat crt js reg
- § cmd exe msc vbs
As a matter of fact, the list of potential "virus carriers" includes more than a dozen types of files. But these are more common than others.
Before starting to write this article, I met with one of the founders of the domestic anti-virus industry, Evgeny Kaspersky, who gave me some figures about the state of the Russian and global anti-virus market. I also spoke with Maxim Skida, a representative of the famous anti-virus company DialogNauka, a manager for working with large clients. From the conversation, I learned a curious fact - it turns out that the anti-virus industry is about to celebrate its first decade.
Of course, antiviruses appeared more than ten years ago. However, at first they were distributed as a free antidote. There was no proper support for the service, since the projects were non-commercial. As an industry, the service of creating and providing anti-virus programs took shape around 1992, not earlier, which means it will soon celebrate its tenth anniversary. Ten years for the birth and development of an entire industry with a turnover of hundreds of millions of dollars is a very short period. During this time, a completely new market has emerged, a certain list of products has been formed, so many new terms have appeared that they would be enough for a whole encyclopedia. It should be noted that sometimes it is even difficult for an inexperienced user to distinguish a scientific term from a commercial name. Of course, in order to use anti-virus programs, it is not necessary to know all the details of the structure and behavior of viruses, but to have general ideas about what main groups of viruses have formed today, what principles are embedded in malware algorithms, and how the global and Russian anti-virus markets are divided, will be useful to a fairly wide range of readers, to whom this article is addressed.
Ten years of development of the anti-virus market in Russia
As already noted, the antivirus market is living on the eve of its decade. It was in 1992 that DialogNauka CJSC was created, which marked the beginning of the active promotion of the famous Lozinsky Aidstest program to the domestic market; since that time, Aidstest has been distributed on a commercial basis. Around the same time, Evgeny Kaspersky organized a small commercial department within KAMI, which at first employed three people. Also in 1992, the American market is rapidly gaining McAfee software VirusScan. In Russia, the market developed quite slowly at that time, and at least by 1994 (Fig. 1) the picture looked something like this: the dominant position was occupied by DialogNauka (about 80%), Kaspersky Anti-Virus owned less than 5% of the market, all the rest - another 15% of the market. In 1995, Evgeny Kaspersky ported his antivirus to 32-bit Intel Windows platforms, Novell NetWare and OS / 2, as a result, the product began to actively move to the market.
A variety of dual-purpose programs are behavioral blockers that analyze the behavior of other programs and, if suspicious actions are detected, block them.
Behavior blockers differ from the classic antivirus with an antivirus core that “recognizes” and cures viruses that were analyzed in the laboratory and for which a treatment algorithm was prescribed, behavioral blockers differ in that they cannot treat viruses, because they know nothing about them. This property of blockers is useful because they can work with any viruses, including unknown ones. This is especially true today, since the distributors of viruses and antiviruses use the same data transmission channels, that is, the Internet. In this case, the virus always has some head start (delay time), since the antivirus company always needs time to get the virus itself, analyze it and write the appropriate treatment modules. Programs from the dual-purpose group just allow you to block the spread of the virus until the company writes a treatment module.
"Checksum" algorithm
The checksum algorithm assumes that the actions of the virus change the checksum. However, synchronous changes to two different segments can cause the checksum to remain the same when the file changes. The main task of constructing the algorithm is to ensure that changes in the file are guaranteed to lead to a change in the checksum.
Methods for the detection of polymorphic viruses
On fig. 6 shows the operation of a program infected with a virus (a) and a program infected with an encrypted virus (b). In the first case, the scheme of the virus is as follows: the program is being executed, at some point the virus code starts to be executed, and then the program is executed again. In the case of an encrypted program, everything is more complicated.
The program is being executed, then the decoder is turned on, which decrypts the virus, then the virus is processed, and the code of the main program is executed again. The virus code in each case is encrypted differently. If in the case of an unencrypted virus, the reference comparison makes it possible to “recognize” the virus by some constant signature, then in the encrypted form the signature is not visible. At the same time, it is almost impossible to search for a decoder, since it is very small and it is useless to detect such a compact element, because the number of false positives increases sharply.
Script viruses and worms
Types of computer viruses
Today there is no such person who has not heard about computer viruses. What is it, what are types of computer viruses and malware, let's try to figure it out in this article. So, computer viruses can be divided into the following types:
under advertising and information programs refers to programs that, in addition to their main function, also display advertising banners and all kinds of pop-up ads. Such messages with advertising can sometimes be quite difficult to hide or disable. Such adware programs are based on the behavior of computer users and are quite problematic for system security reasons.
Backdoors
Hidden administration utilities allow you to bypass security systems and put the computer of the installed user under your control. program that works in stealth mode, gives the hacker unlimited rights to control the system. With the help of such backdoor programs, it is possible to gain access to the personal and personal data of the user. Often, such programs are used to infect the system with computer viruses and to covertly install malicious programs without the user's knowledge.
Boot viruses
Often the main boot sector of your HDD is affected by special boot viruses. Viruses of this type replace the information that is necessary for the smooth start of the system. One of the consequences of such a malicious program is the inability to boot the operating system...
botnet
A botnet is a full-fledged network on the Internet, which is subject to administration by an attacker and consists of many infected computers that interact with each other. Control over such a network is achieved using viruses or Trojans that penetrate the system. During operation, malicious programs do not manifest themselves in any way, waiting for a command from the attacker. Such networks are used to send SPAM messages or to organize DDoS attacks on the desired servers. Interestingly, users of infected computers may be completely unaware of what is happening on the network.
Exploit
An exploit (literally, a security hole) is a script or program that uses specific holes and vulnerabilities of the OS or any program. In a similar way, programs penetrate the system, using which administrator access rights can be obtained.
Hoax (literally joke, lie, hoax, joke, deceit)
For several years now, many Internet users have been receiving e-mail messages about viruses that are supposedly spread via e-mail. Such warnings are sent out en masse with a tearful request to send them to all contacts from your personal list.
Traps
Honeypot (pot of honey) is network service, which has the task of monitoring the entire network and fixing attacks when a outbreak occurs. A simple user is completely unaware of the existence of such a service. If a hacker investigates and monitors the network for gaps, then he can take advantage of the services offered by such a trap. This will write to the log files and trigger an automatic alarm.
Macroviruses
Macro viruses are very small programs that are written in an application macro language. Such programs are distributed only among those documents that are created specifically for this application.
To activate such malicious programs, the application must be launched, as well as the infected macro file must be executed. The difference from conventional macro viruses is that the infection occurs in the application documents, and not in the application's executable files.
Farming
Pharming is the covert manipulation of the browser's host file in order to direct the user to a fake site. The scammers host large servers, such servers store big base fake web pages. When manipulating the host file with the help of a Trojan or a virus, it is quite possible to manipulate the infected system. As a result, the infected system will only load fake sites, even if you enter the correct address in the browser bar.
Phishing
Phishing literally translates as "fishing out" the user's personal information while on the Internet. The attacker, in his actions, sends a potential victim email, where it is indicated that it is necessary to send personal information for confirmation. Often this is the user's first and last name, the required passwords, PIN codes to access user accounts online. With the use of such stolen data, a hacker may well impersonate another person and carry out any actions on his behalf.
Polymorphic viruses
Polymorphic viruses are viruses that use camouflage and reincarnation at work. In the process, they may change their programming code on their own, and therefore very difficult to detect, because the signature changes over time.
Software viruses
A computer virus is regular program, which has the ability to self-attach to other running programs, thus affecting their work. Viruses propagate their copies on their own, which significantly distinguishes them from Trojans. Also, the difference between a virus and a worm is that in order for a virus to work, it needs a program to which it can attach its code.
rootkit
A rootkit is a specific set software tools, which is hidden installed in the user's system, while ensuring the concealment of the cybercriminal's personal login and various processes while making copies of the data.
Script viruses and worms
These types of computer viruses are fairly simple to write and are distributed primarily via email. Script viruses use scripting languages to work to add themselves to newly created scripts or to propagate through operating network functions. Often, infection occurs by e-mail or as a result of the exchange of files between users. A worm is a program that replicates on its own, but which infects other programs as well. Worms, when multiplying, cannot become part of other programs, which distinguishes them from ordinary types of computer viruses.
Spyware
Spies can send the user's personal data without his knowledge to third parties. Spyware at the same time, they analyze the user's behavior on the Internet, and, based on the collected data, show the user advertising or pop-ups (pop-up windows) that will certainly interest the user.
Macro viruses are programs in languages (macrolanguages) built into some data processing systems (text editors, spreadsheets, etc.), as well as in scripting languages such as VBA ( Visual Basic for Applications), JS (Java Script). For their reproduction, such viruses use the capabilities of macrolanguages and with their help transfer themselves from one infected file (document or table) to others. Macro-viruses for Microsoft Office are the most widespread. There are also macro viruses that infect Ami Pro documents and databases. For the existence of viruses in a particular system (editor), it is necessary to have a macro language built into the system with the following capabilities:
1. binding a program in a macrolanguage to a specific file;
2. copying macro programs from one file to another;
3. Possibility of gaining macro program control without user intervention (automatic or standard macros).
Editors meet these conditions Microsoft Word, Office and AmiPro, as well as spreadsheet Excel and base Microsoft data access. These systems contain macro languages: Word - Word Basic; Excel, Access - VBA. Wherein:
1. Macro programs are tied to a specific file (AmiPro) or are inside a file (Word, Excel, Access);
2. macro language allows you to copy files (AmiPro) or move macro programs to system service files and editable files (Word, Excel);
3. when working with a file under certain conditions (opening, closing, etc.), macro programs (if any) are called, which are defined in a special way (AmiPro) or have standard names (Word, Excel).
This feature of macro languages is intended for automatic data processing in large organizations or in global networks and allows you to organize the so-called "automated workflow". On the other hand, the capabilities of the macro languages of such systems allow the virus to transfer its code to other files, and thus infect them. Viruses take control when opening or closing an infected file, intercept standard file functions, and then infect files that are accessed in some way. By analogy with MS-DOS, we can say that most macro viruses are resident: they are active not only at the time of opening/closing a file, but as long as the editor itself is active.
Word/Excel/Office viruses: general information
The physical location of the virus inside the file depends on its format, which in the case of Microsoft products is extremely complex - each Word document file, Excel spreadsheet is a sequence of data blocks (each of which also has its own format), interconnected using a large amount of service data . This format is called OLE2 - Object Linking and Embedding.
The structure of Word, Excel, and Office (OLE2) files resembles a complicated file system disks: the "root directory" of a document file or table points to the main subdirectories of various data blocks, several FAT tables contain information about the location of data blocks in a document, etc. Moreover, Office system Binder, which supports Word and Excel standards, allows you to create files that simultaneously contain one or more Word documents and one or more Excel spreadsheets. At the same time, Word viruses can infect Word documents, and Excel viruses can infect Excel spreadsheets, and all this is possible within a single disk file. The same is true for Office. Most known viruses for Word are incompatible with national (including Russian) versions of Word, or vice versa - they are designed only for localized versions of Word and do not work under the English version. However, the virus in the document is still active and can infect other computers with the corresponding version of Word installed on them. Viruses for Word can infect computers of any class. Infection is possible if this computer a text editor that is fully compatible with Microsoft Word version 6 or 7 or higher is installed (for example, MS Word for Macintosh).
The same is true for Excel and Office. It should also be noted that the complexity of Word document formats, Excel spreadsheets and especially Office has the following peculiarity: there are "extra" data blocks in document files and tables, i.e. data that is not related to the edited text or tables in any way, or are copies of other file data that accidentally appeared there. The reason for the occurrence of such data blocks is the cluster organization of data in OLE2 documents and tables - even if only one character of text is entered, then one or even several data clusters are allocated for it. When saving documents and tables in clusters that are not filled with "useful" data, "garbage" remains, which gets into the file along with other data. The amount of "garbage" in files can be reduced by deselecting the "Allow Fast Save" Word/Excel setting item, but this only reduces the total amount of "garbage", but does not remove it completely. The consequence of this is the fact that when editing a document, its size changes regardless of the actions performed with it - when adding new text, the file size may decrease, and when deleting part of the text, it may increase.
It is the same with macro viruses: when a file is infected, its size may decrease, increase, or remain unchanged. It should also be noted that some versions of OLE2.DLL contain a small flaw, as a result of which, when working with Word, Excel, and especially Office documents, random data from the disk, including confidential ones, can get into "garbage" blocks ( deleted files, directories, etc.). Virus commands can also get into these blocks. As a result, after disinfection of infected documents, the active code of the virus is removed from the file, but some of its commands may remain in the "garbage" blocks. Such traces of the presence of the virus are sometimes visible using text editors and may even cause some antivirus programs to react. However, these remnants of the virus are completely harmless: Word and Excel do not pay any attention to them.
Word/Excel/Office viruses: how they work
Performs various actions when working with a Word document versions 6 and 7 or higher: opens the document, saves, prints, closes, etc. At the same time, Word searches for and executes the corresponding "built-in macros" - when saving a file with the File / Save command, the FileSave macro is called, when saving with the File / SaveAs command - FileSaveAs, when printing documents - FilePrint, etc., if, of course, there are macros are defined. There are also several "auto macros" that are automatically called under various conditions. For example, when opening word document checks it for the presence of the AutoOpen macro. If such a macro is present, then Word executes it. When the document is closed, Word executes the AutoClose macro, when Word starts, the AutoExec macro is called, when it closes, AutoExit, and when creating a new document, AutoNew.
Similar mechanisms (but with different names of macros and functions) are used in Excel/Office, in which the role of auto- and built-in macros is performed by auto- and built-in functions present in any macro or macros, and several built-in functions can be present in one macro. and auto functions. Automatically (i.e. without user intervention) macros/functions associated with any key or time or date are also executed, i.e. Word/Excel calls a macro/function when a specific key (or key combination) is pressed, or when a certain point in time is reached. In Office, the possibilities for intercepting events are somewhat expanded, but the principle is the same.
Macro viruses that infect Word files, Excel or Office, as a rule, use one of the three methods listed above - either an auto-macro (auto-function) is present in the virus, or one of the standard system macros (associated with some menu item) is redefined, or the virus macro is called automatically when pressing any key or key combination. There are also semi-viruses that do not use all these tricks and multiply only when the user independently launches them. Thus, if the document is infected, when the document is opened, Word calls the infected AutoOpen macro (or AutoClose when the document is closed) and thus runs the virus code, unless it is prohibited by the DisableAutoMacros system variable. If the virus contains macros with standard names, they are controlled by calling the corresponding menu item (File/Open, File/Close, File/SaveAs). If any keyboard symbol is redefined, then the virus is activated only after pressing the corresponding key.
Most macro viruses contain all their functions as standard Word/Excel/Office macros. There are, however, viruses that use tricks to hide their code and store their code as non-macros. Three such techniques are known, all of them use the ability of macros to create, edit and execute other macros. As a rule, such viruses have a small (sometimes polymorphic) virus loader macro that calls the built-in macro editor, creates a new macro, fills it with the main virus code, executes and then, as a rule, destroys it (to hide traces of the presence of the virus). The main code of such viruses is present either in the virus macro itself in the form of text strings (sometimes encrypted), or is stored in the document variables area or in the Auto-text area.
Algorithm word work macro viruses
Most of the well-known Word viruses, when launched, transfer their code (macros) to the global macros area of the document ("general" macros), for this they use the commands to copy macros MacroCopy, Organizer.Copy or using the macro editor - the virus calls it, creates a new macro , inserts its code into it, which it saves in the document. When you exit Word, global macros (including virus macros) are automatically written to the global macros DOT file (typically NORMAL.DOT). Thus, the next time you start the MS-Word editor, the virus is activated at the moment when WinWord loads global macros, i.e. straightaway. Then the virus redefines (or already contains) one or more standard macros (for example, FileOpen, FileSave, FileSaveAs, FilePrint) and thus intercepts file manipulation commands. When these commands are called, the virus infects the file being accessed. To do this, the virus converts the file to the Template format (which makes it impossible to change the file format further, i.e. converting to any non-Template format) and writes its macros to the file, including the Auto-macro. Thus, if a virus intercepts the FileSaveAs macro, then every DOC file saved through the macro intercepted by the virus is infected. If the FileOpen macro is intercepted, the virus writes itself to the file when it is read from disk.
The second method of introducing a virus into the system is used much less often - it is based on the so-called "Add-in" files, i.e. files that are service additions to Word. In this case, NORMAL.DOT is not changed, and Word loads the virus macros from the file (or files) specified as "Add-in" on startup. This method almost completely repeats the infection of global macros, with the exception that virus macros are stored not in NORMAL.DOT, but in some other file. It is also possible to inject a virus into files located in the STARTUP directory - Word automatically loads template files from this directory, but such viruses have not yet been encountered. The above methods of introduction into the system are some analogue of resident DOS viruses. An analogue of non-residency are macro viruses that do not transfer their code to the area of system macros - to infect other document files, they either look for them using the file functions built into Word, or refer to the list of recently edited files (Recently used file list) . Then such viruses open the document, infect it and close it.
Algorithm Excel work macro viruses
The propagation methods of Excel viruses are generally similar to those of Word viruses. The differences are in macro copy commands (for example, Sheets.Copy) and in the absence of NORMAL.DOT - its function (in the viral sense) is performed by files in the Excel STARTUP directory. It should be noted that there are two possible options macro virus code locations in Excel tables. The vast majority of these viruses write their code in the VBA (Visual Basic for Applications) format, but there are viruses that store their code in the old Excel version 4.0 format. Such viruses are essentially no different from VBA viruses, except for differences in the format of the location of virus codes in Excel spreadsheets. Although newer versions of Excel (since version 5) use more advanced technologies, the ability to run macros from older versions of Excel has been retained to maintain compatibility. For this reason, all macros written in the Excel 4 format are fully functional in all subsequent versions, despite the fact that Microsoft does not recommend their use and does not include the necessary documentation with Excel.
Virus algorithm for Access
Because Access is part of Office package Pro, then viruses for Access are the same macros in the Visual Basic language, like other viruses that infect Office applications. However, in this case, instead of auto-macros, the system contains automatic scripts, which are called by the system on various events (for example, Autoexec). These scripts can then call various macro programs. Thus, when infecting bases Access data the virus needs to replace some auto-script and copy its macros into the infected database. Infection of scripts without additional macros is not possible, since the scripting language is quite primitive and does not contain the functions necessary for this.
It should be noted that in terms of Access, scripts are called macros (macro), and macros are called modules (module), however, in the future, unified terminology will be used - scripts and macros. Cleaning Access databases is a more difficult task than removing other macro viruses, because in the case of Access, it is necessary to neutralize not only virus macros, but also auto-scripts. And so a significant part Access work assigned just to scripts and macros, then incorrect deletion or deactivation of any element may lead to the impossibility of operations with the database. The same is true for viruses - incorrect substitution of auto-scripts can lead to loss of data stored in the database.
AmiPro viruses
When working with a document, the AmiPro editor creates two files - the text of the document itself (with the SAM name extension) and additional file, containing document macros and possibly other information (name extension - SMM). The format of both files is quite simple - they are the usual text file, in which both editable text and control commands are present as regular text strings. A document can be associated with any macro from an SMM file (AssignMacroToFile command). This macro is analogous to AutoOpen and AutoClose in MS Word and is called by the AmiPro editor when opening or closing a file. Apparently, AmiPro does not have the ability to put macros in the "general" area, so viruses for AmiPro can infect the system only when an infected file is opened, but not when the system boots, as happens with MS-Word after infecting the NORMAL.DOT file. Like MS Word, AmiPro allows you to override system macros (eg SaveAs, Save) with the ChangeMenuAction command. When calling overridden functions (menu commands), infected macros take control, i.e. virus code.
Stealth viruses
Representatives of this class use various means to mask their presence in the system. This is usually achieved by intercepting a series system functions responsible for working with files. "Stealth" technologies make it impossible to detect a virus without special tools. The virus masks both the length increment of the affected object (file) and its own body in it, "substituting" the "healthy" part of the file for itself.
During a computer scan, antivirus programs read data - files and system areas - from hard drives and floppy disks using the operating system and BIOS. Stealth - viruses, or invisible viruses, after launching, leave special modules in the computer's RAM that intercept programs' access to the computer's disk subsystem. If such a module detects that the user program is trying to read an infected file or system area disk, it replaces readable data on the go and thus goes unnoticed, deceiving anti-virus programs.
Also, stealth viruses can hide in the form of streams in system and other processes, which also makes their detection much more difficult. Such stealth viruses cannot even be seen in the list of all running ones, in this moment, in the process system.
There is an easy way to turn off the stealth virus masking mechanism. It is enough to boot the computer from an uninfected system diskette and scan the computer with an anti-virus program without running programs from the computer disk (they may turn out to be infected). In this case, the virus will not be able to gain control and install a resident module in RAM that implements a stealth algorithm, the antivirus will read the information actually written on the disk and easily detect the "bacillus".
Most anti-virus programs counteract the attempts of stealth viruses to go unnoticed, but in order not to leave them a single chance, before checking the computer with an anti-virus program, the computer should be loaded from a floppy disk, on which anti-virus programs should also be written. Many antiviruses are so successful in resisting stealth viruses that they detect them when they try to disguise themselves. Such programs read the program files to be checked from the disk, using several different methods for this - for example, using the operating system and through the BIOS: if mismatches are found, then it is concluded that there is probably a stealth virus in the RAM.
Polymorphic viruses
Polymorphic viruses include those whose detection is impossible (or extremely difficult) using the so-called virus signatures - sections of a permanent code specific to a particular virus. This is achieved in two main ways - by encrypting the main virus code with a non-permanent key and a random set of decryptor commands, or by changing the executable virus code itself. There are also other rather exotic examples of polymorphism - the "Bomber" DOS virus, for example, is unencrypted, but the sequence of commands that transfers control to the virus code is completely polymorphic.
Polymorphism of varying degrees of complexity is found in viruses of all types - from boot and file DOS viruses to Windows viruses and even macro viruses.
Most of the questions are related to the term "polymorphic virus". This type of computer virus is by far the most dangerous.
Polymorphic viruses are viruses that modify their code in infected programs in such a way that two instances of the same virus may not match in one bit.
Such viruses not only encrypt their code using different encryption paths, but also contain the generation code of the encryptor and decryptor, which distinguishes them from ordinary encryption viruses, which can also encrypt parts of their code, but at the same time have a constant code of the encryptor and decryptor.
Polymorphic viruses are viruses with self-modifying decoders. The purpose of such encryption is that if you have an infected and original file, you will still not be able to analyze its code using conventional disassembly. This code is encrypted and is a meaningless set of commands. Decryption is performed by the virus itself at run time. At the same time, options are possible: it can decrypt itself all at once, or it can perform such a decryption "on the go", it can again encrypt already worked out sections. All this is done for the sake of making it difficult to analyze the virus code.
Polymorphic decryptors
Polymorphic viruses use complex algorithms to generate the code of their decryptors: instructions (or their equivalents) are swapped from infection to infection, diluted with commands that do not change anything like NOP, STI, CLI, STC, CLC, DEC unused register, XCHG unused registers, etc. d.
Full-fledged polymorphic viruses use even more complex algorithms, as a result of which the virus decryptor may encounter the operations SUB, ADD, XOR, ROR, ROL, and others in an arbitrary number and order. Loading and changing keys and other encryption parameters is also performed by an arbitrary set of operations, in which almost all instructions can be found. Intel processor(ADD, SUB, TEST, XOR, OR, SHR, SHL, ROR, MOV, XCHG, JNZ, PUSH, POP...) with all possible addressing modes. Polymorphic viruses also appear, the decryptor of which uses instructions up to Intel386, and in the summer of 1997 a 32-bit polymorphic virus was discovered that infects Windows95 EXE files. Now there are already polymorphic viruses that can also use various commands of modern processors.
As a result, at the beginning of a file infected with such a virus, is recruiting seemingly meaningless instructions, and some combinations that are quite workable are not taken by proprietary disassemblers (for example, the combination CS:CS: or CS:NOP). And among this "porridge" of commands and data, MOV, XOR, LOOP, JMP occasionally slip through - instructions that are really "working".
Levels of polymorphism
There is a division of polymorphic viruses into levels depending on the complexity of the code that is found in the decoders of these viruses. This division was first proposed by Dr. Alan Solomon, after some time Vesselin Bonchev expanded it.
Level 1: viruses that have a certain set of decryptors with a permanent code and select one of them when infected. Such viruses are "semi - polymorphic" and are also called "oligomorphic" (oligomorphic). Examples: "Cheeba", "Slovakia", "Whale".
Level 2: The virus decoder contains one or more permanent instructions, but the main part of it is not permanent.
Level 3: The decryptor contains unused instructions - "garbage" like NOP, CLI, STI, etc.
Level 4: The decryptor uses interchangeable instructions and reordering (shuffling) instructions. The decryption algorithm does not change.
Level 5: all of the above tricks are used, the decryption algorithm is unstable, it is possible to re-encrypt the virus code and even partially encrypt the decryptor code itself.
Level 6: permutating viruses. The main code of the virus is subject to change - it is divided into blocks, which are rearranged in an arbitrary order during infection. The virus remains active. Such viruses may be unencrypted.
The above division is not free from shortcomings, since it is made according to a single criterion - the ability to detect a virus by the decryptor code using the standard method of virus masks:
Level 1: to detect a virus, it is enough to have several masks
Level 2: mask detection using "wildcards"
Level 3: mask detection after removal of garbage instructions
Level 4: The mask contains several possible code options, i.e. becomes algorithmic
Level 5: inability to detect the virus by mask
The insufficiency of such division was demonstrated in the virus of the 3rd level of polymorphism, which is called "Level3". This virus, being one of the most complex polymorphic viruses, falls into Level 3 according to the above division, since it has a constant decryption algorithm, which is preceded by a large number of commands-"garbage". However, in this virus, the "garbage" generation algorithm has been brought to perfection: almost all i8086 processor instructions can be found in the decryptor code.
If we divide into levels in terms of antiviruses that use systems for automatic decryption of the virus code (emulators), then the division into levels will depend on the complexity of emulating the virus code. It is also possible to detect a virus by other methods, for example, decryption using elementary mathematical laws, etc.
Therefore, it seems to me a more objective division, in which, in addition to the criterion of virus masks, other parameters also participate:
The degree of complexity of the polymorphic code (the percentage of all processor instructions that can be found in the decryptor code)
Using anti-emulator tricks
Persistence of the decryptor algorithm
Decoder length constancy
Changing the executable code
Most often, such a method of polymorphism is used by macro viruses that, when creating new copies of themselves, randomly change the names of their variables, insert empty lines, or change their code in some other way. Thus, the algorithm of the virus remains unchanged, but the code of the virus almost completely changes from infection to infection.
Less commonly, this method is used by complex boot viruses. Such viruses inject into the boot sectors only a fairly short procedure that reads the main code of the virus from the disk and transfers control to it. The code for this procedure is selected from several different options (which can also be diluted with "empty" commands), the commands are rearranged among themselves, and so on.
This technique is even rarer for file viruses, because they have to completely change their code, and this requires rather complex algorithms. To date, only two such viruses are known, one of which ("Ply") randomly moves its commands around its body and replaces them with JMP or CALL commands. Another virus ("TMC") uses a more complicated method - each time it infects, the virus swaps blocks of its code and data, inserts "garbage", sets new offset values for data in its assembler instructions, changes constants, etc. As a result, although the virus does not encrypt its code, it is a polymorphic virus - the code does not contain a permanent set of commands. Moreover, when creating new copies of itself, the virus changes its length.
Viruses by type of destructive actions
By the type of destructive actions, viruses can be divided into three groups:
Information viruses (viruses of the first generation)
The so-called first-generation viruses are all currently existing viruses whose actions are aimed at destroying, modifying or stealing information.
Hardware viruses (viruses of the second generation)
This type of virus is able to damage the hardware of the computer. For example, to erase the BIOS or corrupt it, to break the logical structure of the hard disk in such a way that it will only be possible to restore it low-level formatting(and even then not always). The only representative of this type is the most dangerous of all that ever existed, the Win95.CIH "Chernobl" virus. At one time, this virus disabled millions of computers. He erased the program from the BIOS, thereby disabling the computer, and the same destroyed all the information from the hard drive so that it was almost impossible to restore it.
Currently, no "wild" hardware viruses have been found. But experts are already predicting the emergence of new viruses of this kind that can infect the BIOS. It is planned to make protection against such viruses on each motherboard special jumpers that will block writing to the BIOS.
Psychotropic viruses (third generation viruses)
These viruses are able to kill a person by influencing him through the monitor or computer speakers. By reproducing certain sounds, a given frequency, or a certain flickering of various colors on the screen, psychotropic viruses can cause an epileptic seizure (in people prone to this), or cardiac arrest, cerebral hemorrhage.
Fortunately, the real existence of such viruses is not known to date. Many experts question the general existence of this type of virus. But one thing is for sure. Psychotropic technologies have long been invented to influence a person through sound or image (not to be confused with frame 25). It is very easy to cause an epileptic seizure in a person prone to this. A few years ago, there was a buzz in some media about the emergence of a new virus called "666". This virus, after every 24 frames, displays a special color combination on the screen that can change the life of the viewer. As a result, a person goes into a hypnotic trance, the brain loses control over the work of the body, which can lead to a painful condition, a change in the mode of operation of the heart, blood pressure, etc. But color combinations today are not prohibited by law. Therefore, they can appear on the screen quite legally, although the results of their impact can be disastrous for all of us.
An example of such an impact is the cartoon "Pokemon", after showing one of the series in Japan, hundreds of children ended up in hospitals with a terrible headache, cerebral hemorrhage. Some of them have died. There were frames in the cartoon with a bright generation of a certain palette of colors, as a rule, these are red flashes on a black background in a certain sequence. After this incident, this cartoon was banned from showing in Japan.
One more example can be given. Everyone probably remembers what happened in Moscow after the broadcast of the match between our football team and the Japanese team (if I'm not mistaken). But on the big screen there was only a video showing how a man with a bat crushed a car. This is also a psychotropic effect, seeing the video "people" began to destroy everything and everyone in their path.
Materials and data were taken from the resources:
http://www.stopinfection.narod.ru
http://hackers100.narod.ru
http://broxer.narod.ru
http://www.viruslist.com
http://logic-bratsk.ru
http://www.offt.ru
http://www.almanet.info
- To post comments, please login or register
Before starting to write this article, I met with one of the founders of the domestic anti-virus industry, Evgeny Kaspersky, who gave me some figures about the state of the Russian and global anti-virus market. I also spoke with Maxim Skida, a representative of the famous anti-virus company DialogNauka, a manager for working with large clients. From the conversation, I learned a curious fact - it turns out that the anti-virus industry is about to celebrate its first decade.
Of course, antiviruses appeared more than ten years ago. However, at first they were distributed as a free antidote. There was no proper support for the service, since the projects were non-commercial. As an industry, the service of creating and providing anti-virus programs took shape around 1992, not earlier, which means it will soon celebrate its tenth anniversary. Ten years for the birth and development of an entire industry with a turnover of hundreds of millions of dollars is a very short period. During this time, a completely new market has emerged, a certain list of products has been formed, so many new terms have appeared that they would be enough for a whole encyclopedia. It should be noted that sometimes it is even difficult for an inexperienced user to distinguish a scientific term from a commercial name. Of course, in order to use anti-virus programs, it is not necessary to know all the details of the structure and behavior of viruses, but to have a general idea of what main groups of viruses have formed today, what principles are embedded in malware algorithms, and how the global and Russian anti-virus markets are divided. , will be useful to a fairly wide range of readers, to whom this article is addressed.
Ten years of development of the anti-virus market in Russia
As already noted, the antivirus market is living on the eve of its decade. It was in 1992 that DialogNauka CJSC was created, which marked the beginning of the active promotion of the famous Lozinsky Aidstest program to the domestic market; since that time, Aidstest has been distributed on a commercial basis. Around the same time, Evgeny Kaspersky organized a small commercial department within KAMI, which at first employed three people. Also in 1992, McAfee VirusScan was rapidly conquering the American market. In Russia, the market developed quite slowly at that time, and at least by 1994 (Fig. 1) the picture looked something like this: the dominant position was occupied by DialogNauka (about 80%), Kaspersky Anti-Virus owned less than 5% of the market, all the rest - another 15% of the market. In 1995, Evgeny Kaspersky ported his antivirus to 32-bit Intel platforms Windows, Novell NetWare and OS / 2, as a result, the product began to be actively promoted to the market.
A variety of dual-purpose programs are behavioral blockers that analyze the behavior of other programs and, if suspicious actions are detected, block them.
Behavior blockers differ from the classic antivirus with an antivirus core that “recognizes” and cures viruses that were analyzed in the laboratory and for which a treatment algorithm was prescribed, behavioral blockers differ in that they cannot treat viruses, because they know nothing about them. This property of blockers is useful because they can work with any viruses, including unknown ones. This is especially true today, since the distributors of viruses and antiviruses use the same data transmission channels, that is, the Internet. In this case, the virus always has some head start (delay time), since the antivirus company always needs time to get the virus itself, analyze it and write the appropriate treatment modules. Programs from the dual-purpose group just allow you to block the spread of the virus until the company writes a treatment module.
"Checksum" algorithm
The checksum algorithm assumes that the actions of the virus change the checksum. However, synchronous changes to two different segments can cause the checksum to remain the same when the file changes. The main task of constructing the algorithm is to ensure that changes in the file are guaranteed to lead to a change in the checksum.
Methods for the detection of polymorphic viruses
On fig. 6 shows the operation of a program infected with a virus (a) and a program infected with an encrypted virus (b). In the first case, the scheme of the virus is as follows: the program is being executed, at some point the virus code starts to be executed, and then the program is executed again. In the case of an encrypted program, everything is more complicated.
The program is being executed, then the decoder is turned on, which decrypts the virus, then the virus is processed, and the code of the main program is executed again. The virus code in each case is encrypted differently. If in the case of an unencrypted virus, the reference comparison makes it possible to “recognize” the virus by some constant signature, then in the encrypted form the signature is not visible. At the same time, it is almost impossible to search for a decoder, since it is very small and it is useless to detect such a compact element, because the number of false positives increases sharply.