Installing iis on desktop versions of windows 10. Installing and configuring IIS
We continue to study web servers and today we will look at installation and basic settings Internet Information Services (IIS) version 7.0 on Windows platform Server 2008. We will also learn how to bind such separate technologies as PHP to our web server.
As you know, PHP works great with Apache and MySql, but suddenly you need to use IIS in conjunction with PHP, then this article is for you. Today we will look at the basics of IIS 7.0, learn how to install this web server and bind PHP to it. We will consider the IIS 7 version, but do not be discouraged if, for example, you have Windows Server 2008 R2, where IIS version 7.5 is installed, it is almost the same as version 7.
First, let's talk a little about the architecture of IIS 7.0. This web server fully built on a modular basis, i.e. unlike IIS 6.0, which was simply installed as a server role and that's it. In IIS 7, you can customize your web server more flexibly by installing only the necessary modules that you need. This is a huge plus because:
- unnecessary modules are disabled, thereby increasing performance;
- the fewer modules involved, the higher the security of the Web server, in other words, the so-called " holes' becomes smaller.
Installing IIS 7.0 Web Server on Windows Server 2008
Before installing, I want to give a little advice, install this server role to the full " naked» server, i.e. besides the IIS service, nothing should be installed there ( I mean from server roles) only the DNS server can be an exception. There is even a separate edition of Windows Server 2008 Web Server, which is completely focused on the Web server, by the way, it is much cheaper than other editions of this operating system.
There are several options for installing this role in Windows:
- Via GUI ( we will use);
- Through the command line ( in my opinion, it is not convenient, since you have to manually write all the necessary modules that you need, and their names are case-sensitive);
- Also through the command line, but already using an XML file ( convenient if you need to set up a lot of web servers, you just tinker with the xml file once, and then you just run one command on the command line and that's it).
Now let's go directly to the installation of this server itself. It is assumed that you already have the Windows Server 2008 operating system installed.
Click Start -> Administrative Tools -> Server Manager -> go to the roles item and click "Add Roles".

In the next step, just click " Further”, but in the next step, stop and think. Which components ( modules) You need, if you leave everything by default, then you will be able to process only static content, and in general you will have few functions available on your server. But still, you do not need to install everything, select only what you need.
In my case, we will fasten PHP and to support this, you need to select the CGI item, and if you suddenly use asp.net, then select the appropriate items, and in general read what else is there ( description is on the right), so as not to be surprised later, “ why don't I have this and this doesn't work". Click next.

And now we press " Install". We wait a few minutes, and after the Add Roles Wizard says that " Installation was successful", click close. And we can immediately check the performance of our web server by simply opening the browser and typing in the address bar http://localhost and if you have the following picture, then your server is working!

How to administer IIS?
For web control the server uses a graphical interface, but I can immediately say that you can also manage it by directly editing xml files. Everything web settings IIS7 servers are stored as xml files. Settings for the entire IIS server at once ( for all sites at once) are stored in a file applicationHost.config, which is located in the following path:

But for the configuration of a single site, you can use the file web.config, it will be created automatically when you change any setting for one site. This scheme reminded me of configuring web Apache server, where you can use the .htaccess file to configure a single site.
By the way, by default, the root directory of your web server is located at: C:\inetpub, in which all your sites are located, when you opened the default site, then you opened files from the wwwroot folder.
Let's go directly to our graphical control panel for the IIS 7 web server, for this open " Start->Administrative Tools->IIS Manager". As a result, you will open, here is the panel:

Where, on the left there will be a tree of your sites ( we only have a default site for now) and applications, all settings are grouped in the center, and the properties of a particular setting are grouped on the right.
Linking PHP to IIS
Now we need to install PHP, for this we need to download the php distribution kit from the official website (http://windows.php.net/download/) as an msi package ( by clicking on the installer link), I downloaded the php-5.3.10-nts-Win32-VC9-x86.msi version, but you can download the newer version.
Let's move on to PHP installation, in general there should be no problems, only on one window, be sure to select the following item: IIS Fast CGI.

Create a new site in IIS
After that, let's create a new site ( in IIS it would be node), click right click under the item " Knots» and press « Add Web Site". Fill in as in the picture, I created a local directory for the new site in the folder C:\inetpub\my, but you can create it at least on another disk.

If you have more than one site, then you will need to separate them from each other. There are several ways, the first, for example, to put them on different ports, but in some cases this is not convenient. The default site has 80, and the new site has 8080, but if you have many sites and you want them to work on the same port, say 80, then you need to fill in the field " Node name”, in other words, this is the domain of the site. After you have indicated here, for example, as I am mysite, you need to make an appropriate entry on the DNS server or, if you have few computers and simply do not DNS servers, or you are just a developer, then write this correspondence in hosts file (e.g. 10.10.10.2 mysite)
Now create a file in the folder of the new site (C:\inetpub\my), for example, index.php with the following content
Using this simple function in the php language, you can find out the settings of the php itself installed on this server, if you see a page indicating the version of php, which is listed just below, then everything works for you.

As you noticed, we did not do any special actions on the IIS 7 server for php binding ( except that we added a CGI component during installation), the php distribution itself and the iis server did it for us.
Useful IIS Settings
Now let's look at a couple of settings for the IIS 7 server, for example, we want the mydoc.php document to open on one site by default. To do this, go to the desired site and open the settings " Default Document” and add the document you need, and you can specify several documents by setting the required priority for them.

And after that, you will immediately see that in your folder with the new Mysite site, a web.config file has appeared ( like i said before). In order to check that you have done everything correctly, create a mydoc.php file with any content, and open the address of your site in the browser, and this document should be loaded by default.
I also want to draw your attention to the fact that if you read somewhere or someone suggested some setting on the IIS server, but you cannot find it on the panel, then most likely you do not have the module necessary for this, as the settings appear according to the installed modules.
For example, you want to set up on your site Basic authentication, but in this moment You cannot find this setting on the server, for this you need to install the required component before. Open Server Manager Roles->Web Server(IIS)->Add Role Services” and choose “ Basic authentication"or in English. basic authentication.

Rediscovering" IIS Manager" and we notice that in the item "Authentication" we have another item " Basic authentication". In order to enable it, you need to disable " Anonymous authentication” and enable accordingly “ Basic authentication". Don't forget to create users, in this case " Local Users». « Server Manager ->Configuration ->Local Users» right click « Create user", I created the user test. Now, when accessing our site, an authentication form will appear.

Enter your user and if you did everything correctly, then you will again be taken to your site!
Now let's talk about the most favorite bunch - this is PHP + MySql. In order to add support for MySql, just install this DBMS ( detailed installation is discussed in the article - Installing the MySql server and reviewing its management and administration tools) and that's it! You can create sites in conjunction IIS 7+PHP+MySql.
I think this is quite enough for the basics, if you have questions, write in the comments, I will try to help. Good luck!
First, familiarize yourself with the IIS Microsoft Management Console (MMC) snap-in. Open the IIS MMC by selecting Start\Administrative Tools\Internet Information Services (IIS) Manager. The MMC configures all installed IIS components. Web sites are configured in the Web Sites folder in the left pane of the console. When this folder is opened, a list of all websites of this server is displayed on the left side of the window, and basic information about each of them is displayed on the right side (see Fig. 2.1).
SSL port(SSL port). Specifies the port on which the website receives Secure Sockets Layer data. SSL allows you to encrypt and/or authenticate data in transit between a client and a server (see Lecture 10).
As in the previous case, when changing the default 443 number for this port, clients must add the port number to the URL to open the website. For example, if you change the port number to 1543, clients must use https://www.beerbrewers.com:1543 instead of https://www.beerbrewers.com to access the site.
Advanced (Optional)
Clicking the Advanced button opens the Advanced Web Site Configuration window ( Additional setting website) in which additional addresses and identifiers are configured. Additional identifiers allow users to access the site from multiple addresses. This approach is used when you want to direct users entering the URL of one site to another site on the same computer without using DNS (Domain Name System). (More information is given in lecture 8). The Advanced Web Site Configuration window specifies host header names so that multiple websites can use the same IP address and port.
About host headers. Host headers allow you to separate one website address from another. They are usually used to configure different websites to use the same IP address and port. The host header is the fully qualified DNS name entered in the browser's address bar to open the site. Host headers save address space when there is only one available IP address. When a page is requested by an HTTP 1.1 web browser, the first part of the request looks like this.
GET./.HTTP/1.1 Accept:.image/gif,.image/xxbitmap,. image/jpeg,.image/pjpeg,.application/vnd.mspowerpoint,. application/vnd.ms-excel,.application/msword,.*/* Accept-Language:.en-us..Accept-Encoding:.gzip,.deflate.. Use61 r-agent:.Mozilla/4.0.(compatible ;.MSIE.6.0;.Windows.NT.5.2) Host: www.mywebsite.com
The part of the code after Host is the host header name - www.mywebsite.com. IIS uses it to send a message to the corresponding website.
Host header names first appeared in HTTP 1.1, and all browsers that are compatible with HTTP 1.1 work with them. Older browsers do not pass the host header and will always navigate to the default website for any IP address.
Advice. To support older browsers, you can create a default page for an IP address with a list of websites and use cookies to direct customers to those sites. Versions of Internet Explorer 4 and up and Netscape 3 and up support host headers, so we won't dwell on that. For more information on support for older browsers, please visit the Microsoft website.
Note. Host header names are part of the HTTP 1.1 protocol and therefore cannot be used on FTP sites, mail sites, and news sites in IIS. When creating multiple sites on the same server, you should get multiple IP addresses or use different ports. Host headers are also not available when working with Secure Sockets Layer (SSL) because the header is in the encrypted request.
Adding an Additional Identity Identifier. You can assign multiple addresses to the same website. The site will respond to requests from each individual address and all at once. Each address associated with a website is called an identity identifier. To create an additional website identity, click the Add button in the Web Site Identification section of the Web Site tab. The Advanced Web Site Identification dialog box will open (see Figure 2.3).

Rice. 2.3. Advanced Web Site Identification Dialog Box
Each identical identifier must be unique and use one of three addresses (IP address, TCP port, or host header value). Enter any valid IP address, port, or host header name. As with the IP Address field on the Web Site tab, the system does not check for this address on the computer, so enter any permitted address. Keep in mind that it will be of little use if your site cannot be found at the specified address in the future.
Removing identical identifiers. To remove an identical identifier, select it and click the Remove button. All identical site IDs in this window cannot be deleted, so the OK button will be unavailable.
Editing identical identifiers. To change an identical identifier, select it and click on the Edit button.
Assigning identical SSL identifiers. A website can be assigned multiple identical SSL IDs. Because SSL does not have host headers, only the IP address and port number change. If there is no certificate installed on the site, all options for identical SSL identifiers will be disabled.
Adding Identity SSL IDs. To add an additional SSL ID to the website, click the Add button. You can add multiple identifiers; just remember that SSL certificates are based on the site name, not the IP address. Any IP address specified must be resolved through the DNS name. If you try to access through the IP address, the site will be unavailable.
Removing identical SSL IDs. To remove an SSL identity from a website, highlight it and click the Remove button. You cannot remove all identical SSL IDs.
Changing SSL identities. To change a website's SSL Identity, select it and click the Edit button.
Connection time limit
The Connection Timeout option on the Web Site tab specifies the length of time, in seconds, that the server maintains an open connection for the client. Typically, the browser sends a request to the server to keep the connection open. This process is called HTTP connection support(keep-alive). The client uses an open connection for multiple requests, and neither the client nor the server needs to re-establish a connection for each request. This greatly improves performance, especially for low speed connections. When it finishes processing requests, the client informs the server that the connection can be closed and resources occupied by it can be freed.
Suppose for some reason the client did not close the connection. It will remain open indefinitely unless the server is told to close it. Value Connection Timeout (Connection time limit) is designed just to set this time interval.
Enabling HTTP connection support
The Enable HTTP Keep-Alives option is enabled by default, which allows the server to accept requests HTTP keep-alive from clients. If this option is disabled, the performance of both the client and the server will be drastically reduced.
Enable log
By default, websites have logging enabled. standard type log file is the W3C Extended Log File. In the window, you can disable logging or change its type. Logging is covered in detail in Lecture 11.
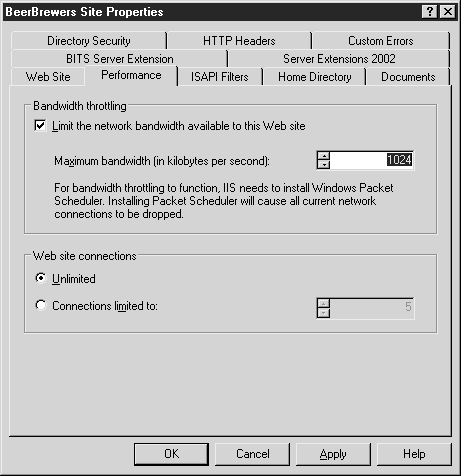
In the Performance tab of the Web Site Properties window (see Figure 2.4), bandwidth management and the number of site connections are configured.
Rice. 2.4.
Bandwidth Management
Using the Bandwidth Throttling parameter, you can configure the maximum bandwidth of the communication channel (Kb / s). Setting the parameter requires the Windows Packet Scheduler program (QOS - Quality Of Service application), which determines whether a packet can be sent over the network. The program queues the data and sends it over the network at the specified speed. IIS automatically installs the Windows Packet Scheduler after setting the bandwidth limit and clicking OK.
When configuring this parameter, remember that the bandwidth of the communication channel local network has values of 10, 100 or 1000 Mb/s, and the speed of the Internet, as a rule, is much lower. For example, a full T1 link provides 1.544 Mbps. If the accepted default value is 1024 KB, then it will be much higher than the T1 link speed.
Note. 1 byte is equal to 8 bits. 1 kilobyte is equal to 8192 bits.
Website connections
The Web Site Connections radio buttons allow you to configure the number of client connections for a given site. The default value is Unlimited. If you select Connections Limited To, enter any number of connections between 0 and 2,000,000,000.
ISAPI Filters tab (ISAPI filters)
In the ISAPI Filters tab (ISAPI Filters) (see Figure 2.5), you can add ISAPI filters for the site. All HTTP traffic directed to the site will be passed to the ISAPI filters in the order specified here. An ISAPI extension applies only to the extension it is associated with, while an ISAPI filter applies to all site traffic. This can cause a significant performance hit for the site, especially if the ISAPI filter is not well-written to waste memory resources. (For more information on ISAPI technology, see Lesson 5 of the Programming in IIS course.)

Rice. 2.5.
The ISAPI filter has a specific state. A red arrow pointing down indicates that the filter is currently disabled. An upward green arrow means the filter is on.
Adding an ISAPI filter
To add an ISAPI filter, click the Add button, give the filter a name, and then select the executable file that will be used to filter traffic. The filter name should be friendly and easy to use.
Removing the ISAPI filter
To remove an ISAPI filter, select the filter and click the Remove button.
Changing the ISAPI filter
To edit an ISAPI filter, select the filter and click the Edit button. Keep in mind that you can only edit the executable pointed to by the filter. The filter name cannot be changed.
Enabling and disabling the ISAPI filter
If the filter is currently is active, it can be disabled by highlighting the filter name and clicking the Disable button. If a filter is currently disabled, it can be enabled by highlighting the filter name and clicking the Enable button. Disabling a filter allows you to pause its operation without removing it from the list of filters.
Changing the order of execution
When multiple ISAPI filters are used, they are usually executed in a specific order. This order is set in this window. To increase the priority of a filter in the list, highlight its name and click the Move Up button. To lower the priority of a filter in the list, highlight its name and click the Move Down button.
The Home Directory tab (see Figure 2.6) indicates the location of this site and how it handles data.
Pointing IIS to the location of site content
To point IIS to the location of the site content, select the appropriate radio button.
A Directory Located on This Computer. Select this option, then in the Local Path field, specify any logical drive and directory where the content of the site is located. Button Browse (Overview) will help you navigate to the desired directory or enter the path in the field.

Rice. 2.6.
A Share Located on Another Computer. Selecting this option will change the text on the Home Directory tab. The text field Local Path (Local path) will be called Network Directory (Network folder), the button Browse (Browse) - Connect As (Connect as). Enter the Universal Naming Convention (UNC) path in the form \\servername\locationname. Click the Connect As button and set the username and password used by IIS to connect to the specified location in the Network Directory Security Credentials dialog box. If the server is not registered with the system, then it does not have a network share access token. And the entered username and password will allow IIS to authenticate.
IIS can use the username and password provided by the client when authenticating to the site. To do this, select the option Always Use The Authenticated User’s Credentials When Validating Access To The Network Directory (Always use the credentials of an authenticated user when confirming access to network folder) in the Network Directory Security Credentials dialog box. If the user is not allowed to access the remote network resource, it will not have access to IIS resources either.
Redirect to URL. When you select an option, the Redirect To text box appears. Specify in it the URL address to which clients will go when connecting to this resource. Check one of the options.
- The Exact URL Entered Above(Exact URL listed above). Redirects the client to the URL specified in the Redirect To field. The field must contain a complete and valid URL.
- A Directory Below URL Entered(The folder under the specified URL). Redirects the client to a child folder under the parent directory specified by the client in the browser. When this option is selected, simply enter the name of the subdirectory, prefixed with a slash (/).
- A Permanent Redirection For This Resource(Permanent redirect to this resource). Used when moving a site from one URL to another. It sends an "HTTP 301 Permanent Redirect" message to the client. Some clients automatically update their bookmarks after receiving this message.
Home directory options
Selecting the A Directory Located on This Computer or A Share Located on Another Computer radio buttons provides access to the following options. Keep in mind that IIS is based on file systems, so an authenticated (or anonymous) user must have the appropriate permissions when working with permissions.
Script Source Access option(Access to script source codes). When this option is enabled, clients get access to source code scripting (Active Server Pages, ASP) when appropriate read/write permissions are set. Since the scripts are processed on the server side, do not give the client access to their source code and leave the option disabled.
Read option(Reading). When this option is enabled, clients get permission to read files. If the clients on the website are working with web content, it is recommended to enable this option. The Read option is disabled if clients are allowed to upload files with write permission and exclude reading uploaded files (see the related technote).
Write option(Record). When enabled, clients with HTTP 1.1 browsers that support the PUT function are allowed to upload files to this directory.
Warning. If users are allowed to read and write files to a directory, any user can upload a file and then execute it. When scripts are enabled, they run on the server, so an attacker can upload a malicious ASP file, execute it, and damage the server.
Directory Browsing option(Browse directories). When this option is enabled, clients get permission to view directories, and, consequently, all its files. If a default page exists, it will be displayed to the client. V otherwise the client will see a list of all files and directories, except for virtual ones, since they are not in file system. Enabling this option poses a security risk, as any user can view the site's file structure.
Log Visits option(Keep a log of visits). When enabled, all visits to this directory are logged if IIS logs.
Index This Resource option(Index this resource). When enabled, the directory will be indexed by the Microsoft Indexing Service, if installed and enabled.
Application settings
The Application Settings section configures application settings to define their boundaries. When you create an application, you can specify that it runs in an application pool that you create. This allows you to isolate applications from each other and set up workflows to deal with problematic applications, scripts, or content that should be isolated.
application name(Application Name). Specifies the name of the application to be created. If the text field is dimmed and the Create button is available, this means that the application has not yet been created. If the Remove button is available, then an application is defined for the directory and the Application Name text box displays its name.
Execute Permissions(permissions to execute). Specifies the type of content allowed on this site.
- None(Not). The default value for IIS is 6. This is a significant change to the out-of-the-box IIS configuration. Previous versions allowed scripts (such as ASP) to run on a standard IIS installation. This caused problems, especially since IIS was installed by default when Windows was installed, and therefore Windows was configured to run both IIS and its scripts. Disabling scripting in a standard installation now provides the most secure default IIS configuration.
- Scripts Only(Scripts only). Allows ASP scripts to run on the site. This option should only be enabled when needed, as it allows you to run any type of script.
- Scripts And Executables(Scripts and executables). Allows scripts and executable files to run on the site. The executable category includes files (.exe), dynamic link libraries (.dll), and common gateway interface scripts (.cgi). This option should only be enabled when needed, as it allows access to and execution of any type of file.
Warning. Ensure that Write NTFS and Write IIS permissions are disabled on directories that are not set to None in execute permissions.
Application Pool(Application pool). Used to specify in which application pool the content of the site will run. This list is populated with data from application pools created in IIS MMC. The field will be grayed out if there is no application already defined for the home directory.
Unload
The Unload button unloads the sandboxed application from memory. If an application is loaded into memory and a configuration change is made, it must be unloaded for the change to take effect. If the button is not available, it means that the application is not loaded into memory, or you are not in the application's start directory.
Configuration
The Configuration button changes the application configuration settings for the directory. In the Application Configuration window that appears (see Figure 2.7), you can configure some settings for how the home directory interacts with scripts and executable content.

Rice. 2.7.
The Application Configuration window has the following tabs.
Mappings Tab(file types). It specifies the associations of file extensions with ISAPI DLLs. By default, all ASP libraries (.asa, .asp, .cdx, .cer), database connectors (.idc), and backend includes (.shtm, .shtml, .stm) are listed. When a request is made, this list is used to figure out which DLL to pass the content to, based on the extension of the requested file.
If the Cache ISAPI Extensions option is enabled, ISAPI DLLs are cached in memory and IIS processes requests for associated extensions without reloading the DLL. This improves the performance of most ISAPI applications, including ASP. The option is enabled by default and it is highly recommended not to disable it. If this option is disabled, IIS will load ASP.DLL and create application and session state objects on each request to an ASP page. After processing the request, IIS immediately unloads ASP.DLL. If the client requests an ASP page during application unloading, an error may occur. As a rule, the option is disabled only when testing the ISAPI.DLL code, when a reboot is required every time
You can add your own ISAPI.DLLs and assign links to them. To add and customize DLLs do the following.
- Click on the Add button. The Add/Edit Application Extension Mapping dialog box will appear.
- Enter the name of the executable file (or navigate to it) that will process the content.
- Enter a name for the extension. You don't need to put a dot before the extension.
- Specify whether to pass only certain HTTP commands to the application, or all. To limit the set of commands, enter the allowed commands separated by commas.
- Leave the Script Engine and Verify That File Exists options checked unless there is a reason to disable them. Next, we will talk about their purpose.
Limiting HTTP verbs(Restrict HTTP commands). HTTP clients use commands to request server actions. These commands (methods) are defined in the W3C specification for HTTP. The most common methods are GET, HEAD, POST, and TRACE, although PUT and DELETE are also used. It is recommended to limit the set of commands to reduce the vulnerability to attacks. For example, linking to ASP files restricts the set to GET, HEAD, POST, and TRACE commands. If there is a restriction, only the commands in the list will be passed to the application for processing.
- Script Engine(Script Engine). The option is enabled by default. In this case, IIS will treat the content as a script rather than an executable, which precludes including execute permissions on the directory because scripts are bound to the interpreter.
- Verify That File Exists(Checking if the file exists). When this option is enabled, IIS checks for the existence of the script file and the user's right to work with the file before sending it to the interpreter. Since each script is opened twice (once for review and once for reading and sending to the script engine), enabling this option results in performance degradation. This option is disabled by default in IIS 5, and, like many other options, is disabled in IIS 6 for security purposes.
Note. Even when ISAPI extensions are bound and enabled, they may not work unless the Scripts Only option is selected in the home directory permissions. In this case, enable the Scripts And Executables permission to successfully process the content.
To change the association of an application with an extension, select the extension and click the Edit button. The same window will appear as after clicking on the Add button, with identical options.
To remove an application's association with an extension, select the extension and click the Remove button, then confirm the removal.
The wildcard is used when linking an ISAPI application with all file extensions. The question arises why not just apply the ISAPI filter. There are some differences between an ISAPI filter and application communication using a wildcard. At the administration level, ISAPI filters are applied to the entire website, while ISAPI extensions are configured for individual directories. A subdirectory inherits group extension links from its parent directory, unless it contains its own (in which case parent links are ignored).
To add an application link, click the Insert button. Then enter the name of the executable file (or navigate to it) to process the content. The Verify That File Exists option has the same effect as for extension associations and is a security measure.
To change the application association, highlight the extension and click the Edit button. The Add window will appear with similar options.
To remove an application association, highlight the extension and click the Remove button, then confirm the removal.
The Move Up and Move Down buttons set the communication priority for ISAPI applications. Requests will be sent through the specified application links in the order specified here.
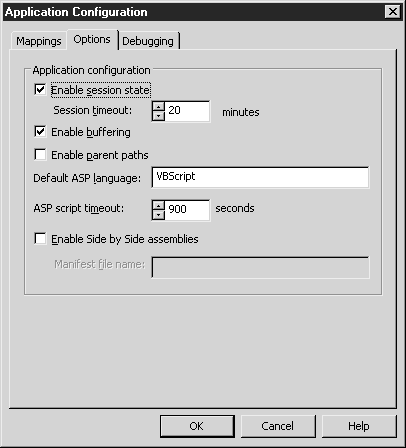
Options tab(Parameters). The Options tab (see Figure 2.8) is used to configure the application, the script engine, and determine how sessions are supported.
The Enable Session State option configures ASP to create a back-end session for each client session on the server. This approach only applies to regular ASP scripts because session state is configured in the web.config file for ASP.NET applications. The session stores data about the user that navigates to each page they visit. In the program, this data is stored in variables in the session object. Session variables can take up a significant amount of memory, so it is not recommended to use them in large numbers on high-traffic sites in order not to degrade performance.
The Session Timeout parameter specifies the amount of time a session is idle before being closed. Specify any value between 1 and 2,000,000,000 minutes. Who knows, you might need a session variable in 3800 years.
Rice. 2.8.
Advice. Take your time to use session states if you are working with ASP web framework or using workflow recycling. In the ASP web framework, each time a user connects to a website, they may be taken to a different server. Because session state is created on a different server (not where the user is currently logged in), session state information is lost. This also happens when a workflow containing session information is recycled. As a result, we recommend that you either stop using session state or use ASP.NET.
Check the Enable Buffering option to configure the server to cache all ASP script output before sending it to the browser. The option sends the output all at once, not line by line. However, if you are processing a large script, you want to display the page immediately after processing the content, so this option should be disabled.
Parent paths allow you to link to directories using relative path names in ASP code. The path to the script in the parent directory is indicated by two dots (".."). This only applies to dynamic content such as include files. Static content can be accessed using relative paths. The Enable Parent Paths option is disabled by default for security purposes because dynamic content can be executed on the same page without specifying a directory structure to navigate to the desired location.
Note. In IIS 6, parent paths are disabled by default. If you have relative paths in your code and that code used to run in IIS 5, then you either need to change the code or check the Enable Parent Paths option to make dynamic content run in IIS 6.
The Default ASP Language option determines the language that processes script content. Script content is tagged<% и %>. IIS 6 ships with two languages: Microsoft Visual Basic Scripting Edition (default) and Microsoft JScript. Install any ActiveX scripting engine to interpret content on the site.
The ASP Script Timeout option specifies the maximum amount of time for a script to run. If the option is disabled, then an illiterately written script can run indefinitely and cause problems on the server. At the end of the specified time, the script stops, the processed content is sent to the browser with an error message stating that the time limit has been reached. Specify any interval from 1 to 2,000,000,000 s (that's 63 years!).
The Enable Side By Side Assemblies option allows an ASP application to execute code in certain version applications. You can install the latest version of the application on the server, but run specific code in an older version of the DLL or EXE. To customize the versioning build, create a manifest file ( XML file) containing configuration, location, and COM registration information. It will tell IIS the correct component to use. Add a manifest file to each virtual directory that uses the different version builds.
Debugging tab(Debug). The Debugging tab of the Application Configuration window (see Figure 2.9) helps you troubleshoot problems when testing your ASP script code. When enabled, IIS uses the Microsoft Script Debugger to inspect code. IIS is configured to debug both server-side and client-side scripts. Enabling server-side scripting has a performance impact, so only use it when necessary. You can customize the message that is sent to clients when an error occurs in a script.

Rice. 2.9.
- Enable ASP Server Side Script Debugging(Enable server-side script debugging). Enabling the option will configure IIS to use the script debugger to inspect code as it is being processed.
- Enable ASP Client-Side Script Debugging(Enable client-side script debugging). Enabling this option will allow debugging ASP pages using Microsoft ScriptDebugger on the client side. When an error occurs, the client will receive a message asking if the error needs to be debugged.
- Send Detailed ASP Error Messages to Client(Send verbose error messages to the client). As the default option, sends a standard error message with the file name and relative path, a special error message, and the line number where the error occurred. This gives clients access to detailed information about site settings, so it makes more sense to send other error messages for security reasons.
- Send the Following Text Error Message to Client(Send the following error text message to the client). Check this option and enter the text of your own message to be sent to the client when an error occurs in the ASP script. For example, enter a message with an email address where the client can send a bug report.
Creating a Neighbor Version Layout
Let's create a manifest file that allows the application to use more old version DLLs. It is a key object when linking neighboring versions, so we start with it. It contains information for IIS about which graphical user interface to use for the loaded COM object. Let's name our file Myapp.xml ; it must be placed in each virtual directory that uses this DLL.
Now we need to instruct IIS to use the neighbor build. On the Options tab, check the Enable Side By Side Assemblies option. Then enter Myapp.xml in the Manifest File Name field. Our manifest file is in the same directory, so only the file name is specified.
The Web Site Properties window has another tab, Documents (see Figure 2.10). It is configured standard pages website, as well as the footer placed on each page.

Rice. 2.10.
Enable Default Content Page
This option specifies the default page that is displayed when a document name is not specified in the URL string of the request. For example, when a client enters http://www.microsoft.com, the IIS Web server checks for a default document. When this option is enabled, this document is displayed. This approach does not require the client to specify a document name for each site visited. If no default document is defined, and the client has not specified a document name, then what happens next depends on whether directory browsing is enabled or disabled.
- Directory browsing is enabled. The server sends a list of the contents of the directory.
- Directory browsing is disabled. The server sends an error message: "Viewing the contents of this virtual directory is prohibited."
Add or remove pages with default content
IIS looks up the names of given pages if no specific page is specified in the request. The file name must exactly match the page name, so be sure to include the extension, and do it right (Default.htm is not the same as Default.html). To add a file name to the list, click the Add button and enter a page name. To remove a filename from the list, select it and click the Remove button. Deletion confirmation is not requested.
Setting the default page order
When searching for a default page, IIS checks the list in the order specified in this window. IIS uses the first page whose name matches the search criteria. To change the order of the list items, highlight the page name and use the Move Up and Move Down buttons to move it to the desired location.
Enable Document Footer
Check this option to include the document footer. The footer is an HTML document that appears at the bottom of every page. It is used if you want to place some information, for example, about copyright, on all pages of the site, without entering a code (or file) into each page. HTML document contains only specific code to display without opening tag . Tags are used to format footer text. Unfortunately, footers can only be placed on pages with static content (HTML).
After enabling this option, click on the Browse button to select the document to use as the footer. The code in the document must be HTML-compatible (should not contain scripts), and it does not have to be a .htm file.
The Directory Security tab (see Figure 2.11) is used to configure site security settings: IIS client authentication settings, specifying clients that can connect to the server, and setting connection security between client and server.

Rice. 2.11.
Changing Authentication and Access Control Settings
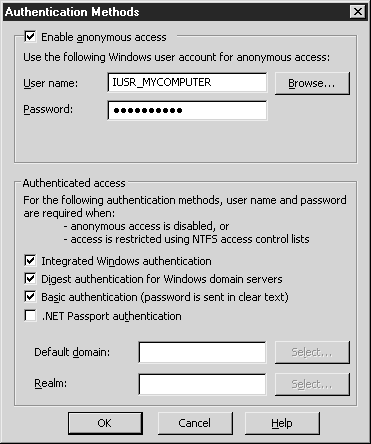
This section selects the type of site authentication to ensure its security. Be aware of the interaction between NTFS security and IIS security measures and their impact on users who authenticate to a web page. To change the Authentication and Access Control setting, click the Edit button. The Authentication Methods dialog box will open (see Figure 2.12).
Rice. 2.12.
Enable Anonymous Access option(Enable anonymous access). When this option is enabled, users connect to the web page without entering authentication data. The security context uses the Guest account, which is the Internet guest account. It is created when IIS is installed and named IUSR_<имя_компьютера>. The option allows you to configure security measures for all anonymous users visiting the site using this account. You can opt out of the Internet guest account and use another account (local or located on a trusted domain) instead.
Advice. Any account used to access web pages must have file access permissions at the NTFS level. See Chapter 6 for more information about setting these permissions.
To select an anonymous access account, follow these steps:
- Enter the account name in the Authentication Methods dialog box. For a domain account, use the name format domainname\username.
- Click the Browse button to search for the desired name. The standard Windows 2003 object selection window will appear.
- In this window, select the user account name and location. You can search by clicking on the Advanced button.
- After selecting an account, click the OK button.
- Enter the account password in the Password text box. After clicking on the OK button, a password confirmation window will appear.
When you specify a username and password, IIS does not check that the information is correct. If the data is entered incorrectly, IIS will run with anonymous access to the site disabled. This is difficult to detect, as Internet Explorer will automatically use other authentication methods, such as logged in user credentials. As an administrator, you will have access to resources, but as a guest user, you will not. You can find out which user is currently authenticating by looking at the log file of the site that logs this process. When using an account that does not have access to the specified resource, a window for entering authentication data will appear.
Authenticated Access. The Authenticated Access section of the Authentication Methods window displays the types of authentication enabled on the site. If the IIS guest account does not have access to the resource, IIS checks for available authentication types.
- Integrated windows authentication . The most secure authentication method, great for any version Internet browser Explorer in the absence of an HTTP proxy. It is built into all IE browsers starting from version 2.0. Browsers like Netscape do not support this authentication method. Integrated Windows Authentication uses the NT challenge/response or Kerberos protocol on the server. If Kerberos is supported by the client and server, and if a trusted Key Distribution Center (KDC) is available, the Kerberos protocol is used; otherwise, the NT request/response principle.
- Basic Authentication. The simplest and most versatile authentication method, in which the username and password are transmitted in clear text. Because this method does not use encryption, it is easy to crack. The advantage of the method is its versatility. As with analytical authentication, specify the user account database used for authentication. Enter a realm name in the Realm text box, or click the Select button to select the desired realm from the list.
- .NET Passport Authentication. New method authentication used in Microsoft technologies. It allows customers to use single sign-on to passport-supporting websites. Passport support requires a functioning .NET Central Passport Server. The .NET Passport Server can be downloaded from the Microsoft MSDN website (http://msdn.microsoft.com). When this authentication method is selected, the Default Domain field becomes active. The IIS server must be a member of a domain; you need to specify the default domain for authentication. Specify its name in the field or click on the Select button to select from the list.
Analytical Authentication for Windows Domain Servers. Analytic authentication is available when using Active Directory accounts. This method, although associated with some dangers, is still more secure than basic authentication. Along with Active Directory, HTTP 1.1 is also required, so analytical authentication only works with new versions of browsers that support this protocol. It is also necessary that the domain controller maintain an open copy of each password in order to check passwords for random information sent by the client. This is where the security threat lies. Storing passwords in clear text on disk is a clear risk, so make sure that the domain controller is well protected from intrusions, otherwise an attacker can find out the passwords he needs. The advantage of analytical authentication is that the password is not transmitted over the network in clear text, as in basic authentication.
Analytic authentication is a simple hash and therefore works through firewalls and proxy servers. It is also available for Web-based Distributed Authoring and Versioning (WebDAV) directories. Because analytical authentication requires a domain, selecting it makes the Realm field available. If analytical (or basic) authentication is not enabled, the Realm field is not available. This field specifies the user account database used for authentication. Enter the area name in the field using the keyboard or use the Select button to select desired name from the list of areas.
Restricting access by IP address or domain name
IIS allows you to restrict access to a user's site without specifying a username and password. With the help of restrictions on IP addresses, a specific group of users is specified, which is granted or denied access to the site. This is used in the following cases.
- It is necessary to provide access to the site to a specific group of users.
- All IP addresses of users who are granted access are known.
- You need to prevent other users from accessing the site.
- There is no need for authentication as a means of access control, or another restriction needs to be used.
If you decide to restrict access by IP addresses, then these restrictions must be configured. Click the Edit button in the IP Address And Domain Name Restrictions area. domain name) in the Directory Security tab. After clicking on the Edit button, the IP Address And Domain Name Restrictions dialog box will open (see Figure 2.13). You need to choose how to set the restriction: deny access to all users, except for specific individuals, or allow access to everyone and restrict access to the site to certain users. If you select the Granted Access option, the approach to the restriction will be loyal; selecting the Denied Access option will enforce the "deny access to everyone, with a few exceptions" principle.
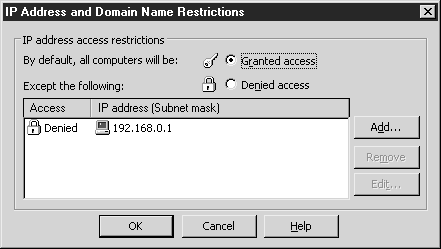
Rice. 2.13.
Changing IP Restrictions. To add an IP address to the list, click the Add button. The Grant Access or Deny Access window will appear, depending on which option is selected.
The choice to grant or deny access is a global decision. You cannot deny access to some IP addresses and allow access to others. Here you need to act on the principle of "all or nothing." Select the required type of access.
- One computer. Allows you to enter an IP address in the access list. You can specify multiple computers in this way. If you don't know the computer's IP address, click the DNS Lookup button to look up the IP address by name.
- Computer group. Allows you to enter a network ID and subnet mask to add computers to the list. Using variable length subnet masks, you can determine the IP addresses in the list fairly accurately.
- Domain name. Allows you to enter a domain name to block access to the site from it. Be careful when using this option, as it does a reverse lookup against each client that connects to the server to see if it is a member of the restricted domain. This negatively impacts performance and causes delays in client authentication. Operations reverse lookup, as a rule, require a large amount of time to execute.
After selecting and setting the type of access, click on OK to make the corresponding entry appear in the list.
To remove, highlight the entry and click the Remove button. To change, highlight the entry and click the Edit button.
Connection security
The Secure Communications area on the Directory Security tab is used to configure certificates for authentication and encryption. It allows you to create certificate requests, assign, export, import and backup certificates, configure server interaction with client certificates.
To set up a certificate for this server click on the Server Certificate button. The Web Server Certificate Wizard window appears. Click the Next button to change the certificate assignment settings.
Create A New Certificate(Create new certificate). Allows you to configure a request to be sent to a Certificate Authority (CA) (see Lecture 10). The request is either sent to an online CA or saved to a file and the file is then sent to the CA through the registration process. To submit a request to an online CA, install Certificate Services on the server.
Advice. Corporate certificate authorities (CAs) are located in Active Directory and have SRV records in DNS so you can find them. See Chapter 8 for more information on SRV and DNS records. If there is a separate CA installed on this computer, IIS will not be able to recognize it. But this is not such a big problem, since you can manually approve and install the certificate (see lesson 7 of the course "Programming in IIS"). We recommend that you locate the CA in a secure location; a vulnerable web server is not suitable for this purpose.
When creating a request to submit to a CA, complete the following steps.
- Select the Create A New Certificate option, then click the Next button.
- Select the Prepare The Request Now, But Send It Later option, then click the Next button
- Enter the desired name for the certificate - you can enter any name.
- Specify the length of the certificate in bits. You can choose 512, 1024, 2048, 4096, 8192, or 16384 bits to create a complex hash.
- If you want to select a Cryptographic Service Provider (CSP) to generate this certificate, check the appropriate box. CSP is an algorithm used to generate certificates.
- Enter the name of your organization and select the organizational unit. Remember that when using a commercial certificate authority, you must provide your legal business name. Click on the Next button.
- Enter a common site name. It must match the DNS or NetBIOS name used for the site. Since each certificate corresponds to a specific name, it is only valid for one name. If you use a different DNS or NetBIOS name, you must obtain a new certificate. Click on the Next button.
- Enter data in the fields City (City), State (State) and Country (Country). Don't cut short. Click on the Next button.
- Enter the name and location of the file to place the request. Be aware of this file as it will be used in the certificate request. Click on the Next button.
- The next window is a report window. Make sure the information you entered is correct. Click on the Next button.
- Assign An Existing Certificate(Assign an existing certificate). Allows you to assign the correct certificate stored on this computer to the website. Selecting the option will display a list of certificates for this computer. Select one of them and click on the Next button. Select the SSL port for the site. The current window is set to the default port value (443). Do not change this value unless absolutely necessary, as clients establish an SSL connection on port 443 by default. After selecting the port number, view the resulting windows and complete the wizard. The installed certificate is available for immediate use by clients.
- Import A Certificate From A Key Manager Backup File(Import the certificate from the key manager archive). Allows you to import a certificate exported using the Windows NT 4.0 Key Manager program. After selecting the option, navigate to the location of the saved .key file and select the file. Then specify the SSL port for the site, review the resulting windows, and complete the wizard.
- Import A Certificate From A .pfx File(Import certificate from .pfx file). Allows you to import a certificate file that conforms to the Personal Information Exchange Syntax Standard or PKSC #12. It is a standard for storing or transporting certificates in a portable format. If you need to archive or export the certificate after import, check the Mark Cert As Exportable option. After selecting the .pfx file, provide a password to secure the file when exporting. Then specify the SSL port for the site, review the resulting windows, and complete the wizard.
Copy Or Move A Certificate From A Remote Server Site To This Site(Copy or move the certificate from the remote server to this site). It is possible to obtain certificates from another website. This option does not allow you to export the certificate to a file, which is a security risk. Follow these steps to copy or move a certificate from a remote web server.
- In the IIS Certificate Wizard window, select the Copy Or Move A Certificate From A Remote Server Site To This Site option, then click the Next button.
- In the Copy/Move Certificate dialog box, select the desired action.
- Specify whether to export the certificate from this website. Click on the Next button.
- Enter the name of the computer (or browse to it) from which the certificate is being imported.
- Enter the credentials of a user who has sufficient permissions to access the certificate, then click the Next button.
- Specify the location of the site from which the certificate is imported. Use the Browse button to select this location from the list. Click on the Next button.
- Check the data in the resulting window and make sure the correct certificate is imported.
Certificate Processing. After receiving a response from the CA, process the pending certificate request. To do this, follow these steps.
- Run the Web Server Certificate Wizard again by clicking the Server Certificate button on the Directory Security tab.
- In the Server Certificate dialog, select the Process The Pending Request option and install the certificate. Click on the Next button.
- Enter the name of the response file (or navigate to its location) received from the CA, then click the Next button.
- Enter the SSL port number to be used by the site. Click on the Next button.
- Review the report window and verify that the information provided is correct.
- Click on the Next button, then click on the Finish button.
Your site now has the correct certificate and can use it for the port specified when you installed the certificate request response file. If there is no response, delete the pending request. To do this, follow the steps below.
- In the Web Server Certificate Wizard window, select the Delete The Pending Request option. The next dialog box displays a message stating that if you continue the wizard, it will become impossible to process responses to this request, as well as a suggestion to refuse to continue.
- Click on the Next button to delete the request.
- Click the Finish button to complete the wizard.
View details of an installed certificate. If you have a certificate installed, view information about it by clicking the View Certificate button on the Directory Security tab.
- General tab(Are common). Contains information about the certificate: the purpose of the certificate, the person who issued it, the customer of the certificate, the validity period of the certificate.
- Details tab(Details). Contains very important information about the certificate. Here you can view all the properties of the certificate, run the Certificate Export Wizard, enable or disable the purposes of this certificate, and specify multiple download locations from various CAs.
- Certification Path Tab(Certificate Path). Allows you to view the CA certificate hierarchy for this certificate. Displays whether the certificate is valid.
Changing secure connections. Using the Edit button, you can change the certificate associations and trust lists (see Figure 2.14). It is possible to configure the forced use of SSL.

Rice. 2.14.
The Require Secure Channel option enforces the use of SSL on the site. Any browser that does not use the SSL protocol will be denied access to the site.
The Require 128-Bit Encryption option allows you to force the use of strong encryption. This prevents browsers with weaker encryption from accessing the site. Updates for Internet Explorer that implement 128-bit encryption are available on the Microsoft site (http://www.microsoft.com/ie). They can be downloaded by any user in a country that is not part of a number of states that the US has imposed an information embargo on (since Microsoft is a US government corporation).
The use of client certificates implements identification of connecting users on the site. Client certificates are a way to control access. You can specify the following settings.
- Ignore(Ignore). Default option. Any client certificate presented is not accepted.
- Accept(To accept). Accepts a certificate. Allows you to configure certificate associations, which is optional. Any browser without a client certificate will be able to access the site.
- Require(Demand). Requires the use of certificates. Any client without a certificate access to the site is prohibited. To select this option, you must also check the Require Secure Channel option.
Establishing certificate associations is designed to authenticate a client computer with a Windows account. There are two types of relationships: one-to-one and many-to-one.
- Communication "one to one". Used when the user account has its own certificate. Multiple certificates can be associated with a user account, but at least one unique certificate is required to enable this functionality. The certificate is imported and associated with the account, after which it is used to authenticate the user.
- Many-to-one relationship. Used when multiple certificates are associated with a user account. Specifies a client certificate group criteria with information about the certificate, such as the name of a department or organization. If these details match, the specified account is used.
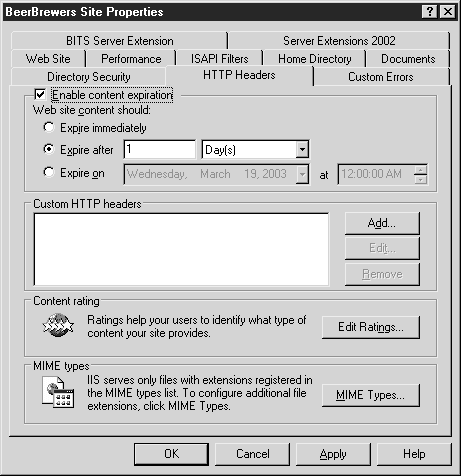
In the HTTP Headers tab of the Properties window (see Figure 2.15), content expiration, content evaluation, and MIME types are configured, and HTTP headers are added.
Rice. 2.15.
Set an expiration date for content
The option sets the expiration date of the files on the website and is used to stop caching content after the expiration date. The expiration date is passed along with the content when requested. Use the RESPONSE object with the CACHECONTROL or EXPIRES property to set the cache expiration and expiration period in ASP pages, but it does not work for graphics. Option performs specified functions using the following options.
Expire Immediately(Immediate expiration). Prevents the requester from caching data. It is advisable to use it on a test site or development site when making changes to the code so that old versions are not cached in IE folders. The option also works for pages with dynamically changing content, when the user gets a new result each time, so that the data of this page is not cached in offline folders.
Expire After(Expires after). Sets the time span in minutes, hours, or days. You can enter any value between 1 minute and 32,767 days (that's just 90 years).
Expire On(expiry in). Sets the content to expire at a specific time. You cannot specify an expiration date earlier than the current date. Any date up to December 31, 2035 is specified. Since this date is handled by the client, it is controlled by the client's time zone, so there may be some variation in content expiration dates depending on the zone.
Custom HTTP Headers
In this section, you can create a custom HTTP header to send to the client, in addition to the regular header that the client receives from the server. The special header contains additional data useful to the client. It also supports the new HTTP standard not natively supported by IIS 6.
Follow the steps below to add a custom title.
- Click on the Add button. The Add/Edit Custom HTTP Header dialog box will appear.
- Enter the name of the custom header in the corresponding field.
- Enter the custom header value in the corresponding field.
- Click on the OK button.
The title is changed with the Edit button and removed with the Delete (Remove) button. When deleting a special header, confirmation of the deletion is not requested.
Content rating
It is possible to evaluate the content of the site. It is a voluntary system developed by the Internet Content Rating Association (ICRA). ICRA is a non-profit, independent organization that empowers parents to make an objective decision about what their children can view online. This system consists of two parts: first the site is evaluated by the webmaster (ICRA does not evaluate), then the end user sets the browser settings to block certain sites based on their content.
Two content rating standards are used: the old RSACi standard and more new system ICRA. IIS 6 supports RSACi, which evaluates content in four categories.
- Violence.
- Sex.
- Nudism.
- Obscene language.
After evaluating the system, the webmaster provides the e-mail address of the person who evaluated the content for feedback and discussion of estimates. You can set an expiration date for assessments, after which they cease to function.
Enabling Site Content Rating. Do the following.
- Open the Content Ratings dialog box by clicking the Edit Ratings button on the HTTP Headers tab.
- In the Content Ratings window, check the Enable Ratings For This Content option.
- Select the rating you want to set.
- Use the slider to set the level from 0 to 4.
- Set one rating or all together (if necessary).
- Enter your email address in the corresponding field. As a rule, an address is indicated here that reflects a characteristic account (for example, [email protected]).
- Specify an expiration date. The date must be greater than the current date. Enter any date up to December 31, 2035.
- Click on the OK button.
MIME types
Multipurpose Internet Mail Extensions (MIME) define the types of files that IIS serves as clients. IIS 6 only serves files associated with scripts or matching a specific MIME type. When IIS detects an extension for which there is no MIME association, the client receives a 404 "Not Found" error, and the server captures a substate code of three.
Note. There is one exception to the MIME rule: text files with a .txt extension that are not MIME type files or are associated with a script are served by IIS.
MIME types are configured globally, at the website or directory level, and are inherited in descending order of levels. Let's look at an example of adding a MIME association.
- Click the MIME Types button in the HTTP Headers tab at the desired level (global, site, or directory, depending on the option selected in the MMC).
- Click on the New button.
- In the MIME Type dialog box, enter the file extension in the Extension field. In this case, specify the .log extension.
- Enter the MIME type in the corresponding field. Since the file is in plain text format, the appropriate MIME type would be text/plain.
- Click on the OK button. The new extension will be added to the list.
- Click on the OK button, then again.
Your directory (server, site) is now configured to serve .log files. Clients that select a file in this directory will see it in their browsers. In this window, you can edit and remove associations with MIME types.
At incorrect setting MIME type IIS will serve the file, but the system will not know what to do with the file. IE users will have to choose a program to open this file from the list provided.
Note. How can I find out if the MIME type matches the file in question? RFC2045 and RFC2046 define fields for MIME types and how types are assigned and reviewed by the IANA (Internet Assigned Names and Unique Parameters Agency). This is the same organization that assigns IP addresses. Full list types is located on the organization's website at http://www.iana.org.
The Custom Errors tab (see Figure 2.16) is used to change the standard error messages sent by IIS. It displays the association of each HTTP error with a substatus code. In the tab, you can create custom error messages and set scripts to run when errors occur.

Rice. 2.16.
Special error messages are used for error reporting and help in troubleshooting. For example, a message type has been created that matches the ASP script for notifying the webmaster. The script logs the incident, displays a problem message to the end user, and redirects the end user to the default page. When using scripts, error messages become useful in diagnosing problems that occur on a website.
Three message types are available for selection.
- Default(Default). Default error programmed into IIS. Lets recover the initial state if the special error is no longer needed.
- file(File). Allows you to select a file using its full name (for example, C:\windows\help\errors\iiserror404.asp).
- URL. Allows you to direct the client to a page on the site by the absolute path of the URL (starting from the top level of the site). Therefore, the HTTP error pages must be in the same site, although they may be in a virtual directory. If you enter a URL in the wrong format, an error message will be displayed.
Changing the Properties of Special Errors
To change the properties of specific errors, follow these steps:
- Highlight the HTTP error, then click the Edit button. The Edit Custom Error Properties window appears.
- Select the message type for this error from the drop-down menu.
- When using a file, specify the path to that file or navigate to its location.
- If using a URL, enter the absolute file name.
- If you select the Default option, you do not need to specify anything.
- After selecting and setting the option, press the OK button.
- Click on the OK button.

Rice. 2.22.
Create an application pool
The default application pool is named DefaultAppPool. Each site that you create uses the DefaultAppPool unless another pool is specified. Follow these steps to create a new application pool.
- Highlight the Application Pools node in the IIS MMC.
- Select Action\New\Application Pool (Action\Create\Application Pool). The Add New Application Pool dialog box will appear.
- Enter the Application Pool ID in the text box. It should be a friendly, descriptive name.
- If using another application pool as a template, select the Use Existing Application Pool As Template option and select the one you want from the list.
- Click on the OK button.
After creating a new application pool, configure its settings. To open the Application Pool Properties window, select the application pool in the MMC and run the Action\Properties command. The Properties window opens, allowing you to configure all application pools at once. To do this, select the level Application Pools (Application Pools) instead of a separate pool. All parameters of this level are identical to the parameters of individual pools.
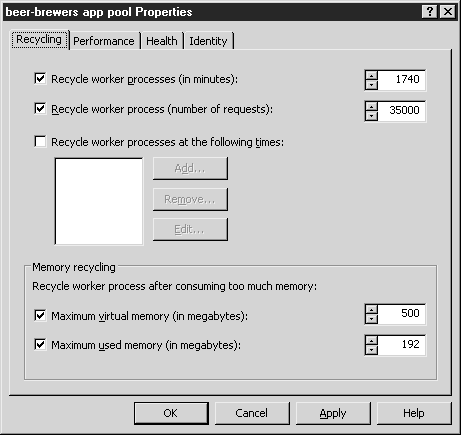
In tab Recycling (Recirculation) (see fig. 2.23) recirculation of memory and worker processes is configured. Worker process recycling helps keep IIS running by killing a worker process and starting a new one, reclaiming all memory used by the worker process.
Rice. 2.23.
You can set up five process recycling criteria and use them individually or all at once.
- Recycle Worker Processes(In Minutes) (Workflow recycling, in minutes). Allows you to configure how long a workflow is active before it is killed and a new process is started. Specify any value between 1 and 4,000,000 minutes. With a value of one minute, the recirculation will be so frequent that it will become a very heavy load for the server. A value of 4,000,000 min (7.6 years) is interpreted as no recirculation. To minimize memory leaks, set the recycle rate to match the technology used by the site. ASP/COM applications cause more memory leak problems than ASP.NET or CGI applications. The volume of requests addressed to the site is an important parameter in this case. Each application is different, so to determine how often it is recycled, find out how the application provides its support.
- Recycle Worker Processes(Number Of Requests) (Workflow recycling, number of requests). Specifies the number of requests processed by the workflow before being recycled. Specify any value between 1 and 4,000,000.
- Recycle Worker Processes At The Following Times(Perform recycling workflows at the next time). Sets specific times of the day for daily workflow recycling. You can add, remove and change the time.
Fixing a Memory Leak
Memory leaks are caused by running applications that do not fully free up system RAM. Every time an application is executed, some amount of memory is wasted, resulting in not enough RAM left for normal system operation. A memory leak is very easy to implement. For example, with the following ASP code:
SET MyBadApp = Server.CreateObject("SomeApp.ThisHurts") MyBadApp.DoSomething
In this case, close the application and set MyBadApp to Nothing by adding the line SET MyBadApp = Nothing to the code. Without this parameter, the memory occupied by the program is not released.
Memory Recycling(Memory recycling) It is possible to carry out recycling based on memory usage. This is a great way to prevent memory leaks, as the recycle occurs as soon as the threshold is reached.
- Maximum Virtual Memory(In Megabytes) (Max. virtual memory, Mb). Allows workflows to be recycled when a threshold is reached. This measure is intended to address virtual memory issues. Specify a value from 1 to 2,000,000 MB. Please note that it is possible to specify a value greater than the immediate amount of virtual memory (about 1.9 TB). Of course, the threshold of 1 MB is almost always reached, in which case recirculation will be carried out regularly.
- Maximum Used Memory(In Megabytes) (Maximum amount of memory used, in MB). Allows recycling based on physical memory usage. Specify a value between 1 and 2,000,000 MB, which is much more than the amount of memory installed on a typical Windows server.
In the tab Performance (Productivity) (see fig. 2.24) settings are configured to avoid overloading the processor.

Rice. 2.24.
- idle timeout(idle period). Specifies the amount of time a workflow can be idle before shutting down. Allows you to implement the work of more applications that are often inactive, since they will not take up processor time. Specify any time period from 1 to 4,000,000 minutes.
- Request Queue Limit(Queue request limit). Specifies the number of requests queued by the application pool before new requests are rejected. Allows you to prevent the server from being overloaded with requests. When the limit is reached, the server responds to all requests with an HTTP 503 "ServiceUnavailable" error message. Specify any value between 0 and 65,535 queued requests.
- Maximum CPU Use (Percentage)(Maximum CPU usage, in percent). Allows the application pool to use a certain amount of CPU time, no more than the set value. The option calculates the CPU to keep track of processor time, and does it not in real time. Specify any value between 1 and 100 percent.
- Refresh CPU Usage Numbers (In Minutes)(Update CPU usage values in, min). Sets the update time for the CPU calculation function. The number of CPU processes is updated after the specified time. Set any value from 1 to 1440 min.
- Action Performed When CPU Usage Exceeds Maximum CPU(Action to be taken when the maximum CPU usage is exceeded). There are two options: No Action and Shutdown. The No Action option simply logs the event. The Shutdown option requests worker processes in the application pool.
Web kits. Allows requests to be distributed across multiple worker processes in a given application pool, achieving greater levels of performance and reliability because the application will use multiple worker processes and a bug in one of them will not affect the others. The Maximum Number Of Worker Processes setting sets the number of worker processes in this application pool. Specify any value between 1 and 4,000,000.
Warning. Installing too many worker processes will have a negative impact on system performance, as each process takes up about 5 MB of memory just at startup. Keep this in mind when specifying the maximum number of worker processes to run on the server.
The Health tab (see Figure 2.25) configures the settings that keep this application pool running and the problem detection settings.

Rice. 2.25.
- Enable Pinging(Enable ping requests). Configures the system to periodically send ping requests to worker processes. No response from the workflow means there is a problem with it; IIS destroys this process and creates a new one instead. Specify any value from 1 to 4,000,000 s.
- Rapid Fail Protection(On-line error protection). Provides server protection by tracking errors in workflows. When a service encounters a certain number of errors within a certain amount of time, IIS shuts down that application pool to protect the server. The server will respond to all new requests with an HTTP 503 "Service Unavailable" error message.
- failures(Mistakes). Sets the number of errors allowed by the server before executing the online error protection function. Specify any value between 1 and 4,000,000.
- Time Period (Time In Minutes)(Time period, in minutes). Sets the amount of time for errors to occur before the online error protection function is executed. Specify any period of time from 1 to 4,000,000 minutes.
Below is a description of the operation of the process in question.
- An error occurs in the workflow.
- IIS writes an unexpected process termination event to the application log, indicating the process ID and exit code.
- IIS restarts the worker process automatically when another process arrives.
- Actions are repeated until the threshold value is reached.
- When the threshold is reached, IIS writes an event about automatic shutdown application pool due to repeated occurrence of errors.
- All clients using this application pool will receive a 503 "Service Unavailable" error message.
- The steps are repeated until the application pool is stopped and reloaded.
Startup and Shutdown Time Limits. Worker processes are not killed immediately after stopping, they take some time to load as well. To stop a worker process, a request to cancel is sent to it, then it is given time to complete the current operations and exit the queue, and only then the process is canceled. With recycle, the newly created process is ready to start running before the old process terminates, so as not to interrupt the service. Sometimes the workflow does not stop completely, or there are problems starting it. Time limits are used to set the amount of time that IIS waits for a problem to occur.
- Startup Time Limit(Load time limit). Used to set the length of time that IIS waits for a worker process to start. Specify any time interval from 1 to 4,000,000 s.
- Shutdown Time Limit(Off time limit). Used to set the length of time that IIS waits for a scheduled completion of a worker process. Specify any time interval from 1 to 4,000,000 s.
The Identity tab (see Figure 2.26) specifies the security account used by the worker process in the application pool. By default, workflows run as network services (the Network Service option [ Network Service]) with limited rights in the operating system.

Rice. 2.26.
Specify the authentication method to be used by the workflows. Select a specific identity or provide a user account. The latter option is a security risk because the accounts have extended access rights to the operating system.
- Network Service(Network Service). The default setting, which is the most secure and recommended for running workflows. In this case, worker processes cannot directly access and manage the operating system.
- local service(Local service). Provides a wider set of rights in the operating system than the previous option. Grants access to the operating system, but prevents access to objects outside the server. Interaction with the desktop is also prohibited.
- local system(Local system). Provides more rights than Local Service. In fact, the option provides full access rights to the entire system.
All three accounts are members of the IIS_WPG group, located on the local system, to which access rights are assigned to processes. If a worker process requires more rights than it currently has, enable those rights for the IIS_WPG group. When setting up an account for a workflow, make sure that the account is a member of the IIS_WPG group.
- Configurable(Customizable). Specifies the account under which the workflows will run. Enter an account name or click on the Browse button and select an account in the window that appears.
When a workflow starts, it has the identity access token it is configured to use. When a request is received from a client, the client's access token is used to process the request. This action is called impersonation and allows workflows to run at a low level of security while performing high-level operations.
Learn how to install Internet Information Services (IIS) on servers running Windows Server 2012 R2 and Windows Server 2008 R2.
IIS (Internet Information Services) is a set of services from Microsoft for the operation of a web server and other Internet services. IIS is installed on the server and works with HTTP/HTTPS, POP3, SMTP, FTP, NNTP protocols. In 2015, version 10 of IIS was released, developed for Windows Server 2016.
Installing IIS on Windows Server 2008
Login to the server with administrator rights. Launch Server Manager from the Start menu or taskbar. From the Server Manager menu, select Roles.
From the Server Manager menu, select Roles.  Click the Add Roles button.
Click the Add Roles button.  Review the information on the initial installation page and click Next.
Review the information on the initial installation page and click Next.  Select "Web Server (IIS)" (Web Server IIS) from the list of server roles and click "Next".
Select "Web Server (IIS)" (Web Server IIS) from the list of server roles and click "Next".  Review the web server information and click Next.
Review the web server information and click Next. 
Please note that services such as ASP.NET, ISAPI filters, etc. are not installed by default.
 Click "Install" to start the installation.
Click "Install" to start the installation.  Launch Server Manager and open the Roles tab > Web Server IIS > Internet Information Services Manager.
Launch Server Manager and open the Roles tab > Web Server IIS > Internet Information Services Manager. The features available to you in IIS are listed in IIS Manager. From here, manage IIS features, configure and restart.
 Test the default site by typing localhost in your browser's address bar.
Test the default site by typing localhost in your browser's address bar. The default page will load.
Add sites to be served by this web server.
 V context menu Select Sites on the Connections tab, select Add Web Site
V context menu Select Sites on the Connections tab, select Add Web Site 
The newly added site will appear in the list of IIS sites.
Installing IIS on Windows Server 2012 R2
 Login to the server with administrator rights. Launch Server Manager from the Start menu.
Login to the server with administrator rights. Launch Server Manager from the Start menu.  On the Dashboard, select Add roles and features.
On the Dashboard, select Add roles and features. The same can be done through the panel " local server" (Local Server) - "Management" (Manage).
 The IIS Setup Wizard will start, review the first page and click Next.
The IIS Setup Wizard will start, review the first page and click Next.  Select the installation type as Role-based or feature-based installation and click Next.
Select the installation type as Role-based or feature-based installation and click Next.  Select a server from the server pool (Select a server from the server pool) and note the name of your server. Click Next.
Select a server from the server pool (Select a server from the server pool) and note the name of your server. Click Next.  On the Select Server Roles page, check "Web Server IIS".
On the Select Server Roles page, check "Web Server IIS".  Leave everything as it is in the window that appears and click Add Features.
Leave everything as it is in the window that appears and click Add Features.  If you do not install anything other than IIS, then click "Next" (Next).
If you do not install anything other than IIS, then click "Next" (Next).  Review the list of IIS components, select the ones you need or leave the default, click "Next" (Next).
Review the list of IIS components, select the ones you need or leave the default, click "Next" (Next).  Review the information in the next window and click Next.
Review the information in the next window and click Next.  View the list of roles IIS web server to be installed. Check the required ones or leave them as they are and click Next.
View the list of roles IIS web server to be installed. Check the required ones or leave them as they are and click Next. Note that the FTP service is not installed by default. If you need new roles later on, you can add them without reinstalling IIS.
 Click the "Install" button.
Click the "Install" button. If necessary, check "Restart the destination server automatically if required", if the item is not selected, then restart the server yourself after installation is complete.
 Launch Server Manager from the Start menu.
Launch Server Manager from the Start menu. The installed IIS service appears in the content list.
 In the upper right corner, click on the “Tools” menu item and launch the “IIS Manager” (Internet Information Services Manager).
In the upper right corner, click on the “Tools” menu item and launch the “IIS Manager” (Internet Information Services Manager).  In the Connections panel, click on the server name, in the window that appears, check Do not show this message again and click the No button.
In the Connections panel, click on the server name, in the window that appears, check Do not show this message again and click the No button.  Features View Panel
Features View Panel The features available to you in IIS are listed in the Features View panel. From here, manage IIS features, configure and restart. For example, set up SSL certificates.
 Immediately after installing IIS, an empty Default Web Site is created by default.
Immediately after installing IIS, an empty Default Web Site is created by default.  Test it out by typing localhost in your browser's address bar. The default page will load.
Test it out by typing localhost in your browser's address bar. The default page will load.  The files for this page are located by default at C:\inetpub\wwwroot
The files for this page are located by default at C:\inetpub\wwwroot  Add sites to be served by this web server. To do this, in the context menu of the “Sites” item (Sites) on the “Connections” tab, select “Add Website”.
Add sites to be served by this web server. To do this, in the context menu of the “Sites” item (Sites) on the “Connections” tab, select “Add Website”.  Fill in the form fields with site data and click OK.
Fill in the form fields with site data and click OK.  The newly added site will appear in the list of IIS sites.
The newly added site will appear in the list of IIS sites. This description applies to the following editions of Windows 7: Professional and Ultimate.
Installing the IIS Web Server
Control Panel → Programs → Turn Windows features on or off. We find the section in the list - IIS Services. Open it and select the necessary components:
Basic set:
- Safety. We select all components except "Authentication with certificate mapping ...".
- Application development components. We select only the CGI component, this is necessary for the subsequent installation of PHP.
- General Functions HTTP. We mark all points.
- Functional check and diagnostics. Select "HTTP Logging" and "Request Monitor".
- Performance enhancement features. We mark all points.
- Website management tools. We mark only the "IIS Management Console".
When all items are selected, click OK. After the installation is complete, be sure to reboot!
Now let's move on to creating a website. Open Control Panel → System and Security → Administrative Tools → Computer Management (you can do this faster: right-click on Computer → select Manage from the menu). In the window that opens, on the left, by clicking on the small triangle, expand the "Services and Applications" group and open the "IIS Manager". In the next "Connections" window, select the "Sites" folder (if there is a Default Web Site, you can delete it), then in the right "Actions" window, click on the "Add website ..." link (you can also do this: right click → Select "Add Website..." from the menu.

Next, in the window that opens, you must specify the name of the website and the location of its files (by default, this is c:\inetpub\wwwroot, if this path is not specified by default, enter it manually). The rest of the options are left unchanged.

Click OK. This completes the basic setup. Now you need to check the performance of the newly created site. Open a browser and enter http://localhost in the address bar. If everything works correctly, you will see a similar page:

Install PHP (FastCGI)
Before starting the installation, you need to download the PHP release from http://windows.php.net/download/ . There are several options to choose from. We need a release VC9 x86 Non Thread Safe. For working with IIS in FastCGI mode, this is the fastest and most stable option. Download the release with an installer, not a zip archive (this is for those who like manual installation). Note that with the installer, it doesn't have to be the latest version of PHP released, it's okay if you download an earlier version.

Choose IIS FastCGI - this is currently the only stable way to install PHP on IIS.
After the installer completes, go to the IIS settings. In principle, only one action needs to be done here - raise the priority of php files so that they are processed in the first place. Open the IIS Manager again - right-click on Computer → select "Manage" in the menu, open "Services and Applications" → "IIS Manager" in the left window. In the window to the right of “Connections”, click on the name of our site and in the middle window open (click 2 times) the “Default Document” section.

In the list that appears, you need to move index.php to the beginning (i.e. to the very top - for this, select index.php and click "Up" on the right):

If you are using Windows 7 64-bit, you need to take one additional step. Open the Application Pools section (in the Connections window). Highlight DefaultAppPool and open "Advanced Options" (via right click or in the far right "Actions" column). In the (General) section, you need to find the option “Enable 32-bit Applications” and set it to True. If additional pools have already been created for existing sites, then for each of them you need to do the same operation.
Now we need to test PHP. In the root folder of the website (c:\inetpub\wwwroot), you need to place the index.php file with the following content:
Open the site in a browser (http://localhost). If everything works correctly, you will see a page with information about installing PHP:

Open the distribution download page: http://www.mysql.com/downloads/mysql/
For Win 32 download: Windows (x86, 32-bit), MSI Installer
For Win 64 download: Windows (x86, 64-bit), MSI Installer
After clicking on the Download button, you will see a registration form, you can skip it by clicking on the link below ("No thanks, just start my download!").
We launch the installer, after several not very informative windows we are offered to choose the type of installation, select Custom:

Component selection window (if you are a beginner, leave everything by default, click Next and install):

At the end of the installation, a new window will appear with a question about the subscription, click the cross in the upper right corner.

The final stage of the installation. Check the "Launch the MySQL Instance Configuration Wizard" option and click Finish:

Once the installation is complete, the MySQL Server Instance Configuration Wizard is launched (you can run it manually from Computer → Program Files → MySQL → MySQL Server 5.5 → bin → MySQLInstanceConfig.exe). Click Next:


Select the installation scenario: Developer Machine - for installation on home computer(our choice), Server Machine - for installation on a server, Dedicated MySQL Server Machine - for installation on a server completely dedicated to MySQL. These options primarily affect the amount of memory consumed by MySQL:

MySQL supports two main database types (InnoDB - with transaction support and MyISAM - without transactions). Multifunctional Database - support for both types of databases will be installed (our choice). Transactional Database Only - Only InnoDB support will be installed. Non-Transactional Database Only - Only MyISAM support will be installed.

If InnoDB support was selected in the previous step, the location of the InnoDB data files can be configured here:

Support for simultaneous connections. Decision Support - up to 20 simultaneous connections (our choice). Online Transaction Processing - up to 500 connections. Manual Setting - manual setting of the number of connections.

We mark the options "Enable TCP / IP Networking" and "Enable Strict Mode". We leave the Port Number unchanged - 3306. If direct connections from other computers are planned to the server, check the option "Add firewall exception for this port" (open the port in the windows firewall).

Select the default encoding. Right now the most reasonable choice is UTF-8. Select the Best Support For Multilingualism option:

Be sure to check the option "Install As Windows Service" (run as Windows Service). Check "Launch the MySQL Server automatically" if you want the service to start automatically.

The final stage. Setting the administrator (root) password. This password is better not to lose! The options "Enable root access from remote machines" and "Create An Anonymous Account" are not recommended, because they reduce security.

Note: if you installed MySQL before, and then uninstalled or reinstalled it, then at the last step an error 1045 (Connection Error) will occur. To avoid this, you will have to uninstall MySQL, then delete the hidden MySQL folder located in C:\ProgramData (this folder contains user data information files). Then repeat the installation and configuration procedure.
Now it remains to check if the installation was successful. Open Start → All Programs → MySQL → MySql Server 5.5 → MySQL 5.5 Command Line Client (a utility for working with MySQL on the command line).
Next, enter the administrator password (root). If the password is correct, you will be taken to the command prompt (mysql>). Enter the command: show databases; (semicolon at the end is required). As a result, you should see a list of databases (at least two - information_schema and mysql). This means that the server is working correctly. Close the command line by executing the exit command.
Installation and basic configuration of phpMyAdmin
Open the download page http://www.phpmyadmin.net/home_page/downloads.php and choose to download the archive ending in *all-languages.7z or *all-languages.zip. Create a phpmyadmin folder in C:\inetpub\wwwroot\ and extract the files of the downloaded archive there.
Let's check how it works. Open the browser and go to the address http://localhost/phpmyadmin/. This window should open:

Before connecting to MySQL, you need to create a configuration file.
There are two options. You can manually edit the config.sample.inc.php file and save it as config.inc.php (both files in the root of your phpMyAdmin installation).
Or use the graphical configurator. To do this, open the following address in the browser: http://localhost/phpmyadmin/setup/

If you see the warning "Unable to load or save settings". Create a config folder at the root of your phpMyAdmin installation (meaning inside the phpmyadmin folder). Make sure that in the security settings of the config folder, the IIS_IUSRS user group and the IUSR user have full control rights. For those who do not know how to do this: right click on the config folder → properties → security tab → click the “Change ...” button → select IIS_IUSRS (...) in the list and check the “Full control” checkbox below, click “Apply”. We do the same for IUSR. If there is no such user in the list, click "Add" → Advanced ... → Search → select IUSR and press OK, then set it full access.

We return to the configurator. To configure the MySQL connection settings, click on the "New Server" button:

The most important moment! If you are connecting to MySQL server installed on the same machine (localhost), in the "Server Host" column, localhost must be replaced with 127.0.0.1 (the same applies to manually creating config.inc.php). Add the following line to the C:\Windows\System32\drivers\etc\hosts file: 127.0.0.1 localhost. In the same file, delete or comment out (put a # sign at the beginning of the line) the line::1 localhost (if it is initially commented out, then you do not need to do anything with it).
We save the settings and automatically return to the previous page. Here we select the default language - Russian, the default server is 127.0.0.1, the end of the line is Windows.

That's all. We return to the page http://localhost/phpmyadmin/. Now you can log in to the system as the root user (enter the password that you specified when setting up MySQL for the root user). Testing the connection to MySQL. If everything went well (you were able to log into phpMyAdmin), delete the config folder.
Applications and sites developed in ASP.NET must be hosted on a web server (hereinafter referred to as IIS). This Windows snap-in, which is responsible for hosting web applications, parallelizing http requests, storing user sessions, and much, much more.
Windows 2008 does not have IIS by default, and before you can set up a site, you must install IIS. Therefore, the article is divided into two parts:
How to install IIS 7 on windows 2008
The IIS 7 Application Server is installed from the operating system distribution. It is advisable to install IIS from the same OS distribution that is installed on this computer. From experience, I’ll say that there are precedents for incorrect work in the case of installing IIS from a “non-native” distribution. Insert the Windows 2008 disc into the drive and start installing IIS:
1. Click "Start" and right-click on "Computer", go to "Management":

2. In Server Manager, select "Features" and click "Add Features":

3. In the tree, select "Web Server Tools (IIS)" and click "Next":

This will start installing IIS 7 from the Windows 2008 operating system disk. Wait until it is finished and restart your computer. Everything! IIS installation completed!
How to set up IIS 7 on windows 2008
So, we have a site, let's call it Security. It is a Security directory and a set of files in that directory. The site has a home page that should load by default. Let's call it index.aspx. The first step is to install and register the .Net Framework. You need to install the same .Net Framework under which your site is written. The version can be viewed in the web.config file of your site. We will assume that our site is written in Net.Framework v.4.0.
Installing and configuring Net.Framework is covered in a separate article How to install Asp.Net and register it in IIS. Here I will describe briefly: to register the .Net Framework in IIS, you need to use the command line from the C:\WINDOWS\Microsoft.NET\Framework\ directory version of your Framework\ run the command aspnet_regiis.exe -i;
Place the Security directory in C:\Inetpub\wwwroot\. This is the working directory of the IIS Manager.
Now let's go directly to setting up IIS:
1. Launch the Internet Information Services (IIS) Manager. Click "Start", "Run". In the window that appears, enter inetmgr.exe and click "OK":


2. First of all, let's create an application group for our site. In general, an application group is created in order to separate applications running on different versions of the .Net Framework. In principle, if you have only one site on your machine, then you can skip this step. In IIS Manager, right-click Application Groups, New menu, Application Group... In the window that appears, enter the name of the application group and click OK. Because Since we decided that our site was written in .Net Framework v.4.0, we will call our application group "Net 4.0":


3. After we copied our site to C:\Inetpub\wwwroot, we have a Security directory in the IIS Manager under Web Sites. Right click and select "Convert to Application":

4. In the window that appears, select our application pool and click "OK":

5. On the "Documents" tab, we need to add our main page. Then, when accessing the site, you will not need to access http:// server_name/Security/ndex.aspx, it will be enough to write http:// server_name/Security and we will get to the main page of the site. On the "Documents" tab, delete all the pages that are there by default and add your index.aspx start page:



6. This completes the IIS configuration, it remains to configure access rights to the Security directory. Open Sharing on the Access tab and give full access to the IIS_IUSRS group and the IUSR user (they are created when IIS is installed). On the "Security" tab, also give full access to the specified group and user:

Now you can try to open our site. Open a browser and enter http:// in the address bar server_name/Security, your main page will appear. Everything! If you have any questions, I will be happy to answer in the comments to the article.