How to remove hidden. How to detect and remove a hidden miner in Windows
Mining is one of the most famous concepts in the crypto world. And cryptosystems have been very popular over the past few years.
The Internet is full of information about cryptocurrencies, their mining and the profit they bring. And the more users are interested in something, the more options for fraud.
One of these “black earnings” schemes is hidden mining. It started in 2011, but these were isolated cases, now it is a rather serious problem.
In order to protect your equipment, it is important to know how to find such a program, remove it and prevent attempts to appear.
A hidden miner is a third-party software that starts mining in background, beyond the user's will.
It is downloaded to a computer and uses its power to mine coins, which are then sent to the scammer's wallet.

The prevalence of hidden mining is growing at a tremendous speed, because it is one of the easiest and most massive ways for hackers to make money. The user may not even guess that his PC is used to mine this or that cryptocurrency, if the software does not overload the computer.
Botnets infect office computers, which most often have weak characteristics. That is why it is used for mining.
Most often, infection occurs due to opening malicious messages, downloading unknown files, and viewing spam mailings.
The most curious thing is that those who are engaged in hidden mining receive very little profit for this.
So, if you put the software on 200 computers, you can get about $ 30 per month.
The only thing that attracts is the passivity of income, because apart from infection, you don’t need to do anything else yourself.
There are very few detailed instructions on how to recognize and remove a botnet on the Internet.. However, before looking into the search for a hidden miner, you should understand why it harms your computer at all.
Why a hidden miner harms a computer
Malicious software is somewhat similar to a regular one computer virus. She also pretends to be a system file and can overload the computer very much.
However, they operate in different ways.
If the virus directly harms the “innards” of the computer, then the hidden miner cannot be detected using the antivirus, because it uses only system resources device.
It is precisely because no antivirus program sees such software that it is dangerous.
After all, in order to neutralize it, you need to spend to understand the characteristics and file system your PC, which for the average user can be a big problem.
A hacker does not have to create software for a PC, it is possible to simply develop a script and gain access to resources.
The scammer simply uploads the created code to the site, which will mine cryptocurrencies while visitors are on the page.

Detecting this is quite simple, when you visit the page, the technique will start to work slowly, and the task manager will display an increased load.
In order to protect your technical device from a hidden online miner, you just need to exit such a page.
Using the Task Manager
When it comes to hidden mining through software, such a simple solution will not help. To remove the miner permanently without installation special programs you need to follow 5 simple steps:
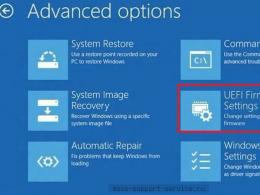
Step 1. We go to "Control Panel" - "Control" - "Task Manager" - "Details".

Step 2 We look through all the tasks, the botnet is different from the rest (often it is an incoherent set of characters).
Step 3 In the tab "Actions" the launch of the file with the name from Step 2 will be displayed.
Step 4 Very often, a hidden miner is hidden under the guise of a system update. To do this, you can enter the name of the file into the search engine and see what it launches.

Step 5. Using a search in the registry, we remove all exact matches.

Step 6 We overload the system.
Using AnVir Task Manager
Step 1. Download and install the program on your computer.
Step 2 Open the program and check all running tasks.

Step 3 If some task seems suspicious, you can call up additional information by hovering over the operation (it is important to remember that many botnets hide under the software, but they cannot fake the file data).

Step 4; Right click on the file - "Detailed information" - "Performance" choose 1 day and look at the activity of the computer during this period.


In windows 7, windows 8, windows 10 and Vista, for security and safety, you can hide important files and folders so that other users do not randomly delete / change important data, or simply from prying eyes. If necessary, these same files are quite easy to display, which we will discuss later in this article.
Also, recently, a case has been very often observed when all files and folders become hidden for users, as if everything that was deleted, and shortcuts with the same names are created instead of them, which is a consequence of a virus infection of a computer / removable media.
It can also happen after installing or checking the computer with an antivirus. If you have just such a case associated with a virus, the instructions below also help you display hidden files and folders. But to completely remove the virus, read the article How to remove a virus with shortcuts.
The first and easiest method I always use is with programs Total commander. Open the program, select desired disk and just click the "Hidden items" button and you will see everything that has been hidden (marked in red exclamation mark).
If you do not have the program installed, also use the fairly simple methods described below.
Show hidden files and folders in windows 8.x or 10
Use the View tab and click the Options button.

On the View tab, check the "Show hidden files, folders and drives" option at the very bottom. If you want to get to hidden windows system files, uncheck the "Hide protected system files" option

Hidden files will appear semi-transparent. If you want to completely remove the "hidden" attribute from a file or folder, click on it right click mouse and select properties. On the General tab, clear the Hidden option.
mixer windows volume 10

In most cases, this helps, but sometimes it happens that the checkbox cannot be removed from the option, because. the hidden attribute is inactive. If so, scroll down a bit and follow the instructions.
windows 7 or Vista
Open any folder and select "Folder and Search Options" from the Organize menu.

As in the previous example, check or uncheck the required options and click OK.

What to do if the hidden attribute of a folder is inactive
In case you are unable to remove the attribute hidden from a folder with the above method, the code below can help you in this situation. Just copy it, paste it into notepad and save it as folder with extension .vbs instead of txt to make it folder.vbs. Then copy and paste the file to the drive you want ( USB flash drive, SD card or HDD) where you want to display hidden files and launch it with a standard double-click.
Don't forget to change "d:" to your drive letter.
‘ Reset file attributes for all folders within a specific drive ‘ Change d: to the drive letter where the script will be applied cDrive = "d:" Set FSO = CreateObject("Scripting.FileSystemObject") ShowSubfolders FSO.GetFolder(cDrive)
WScript.Echo "Done with fix."
composs.ru
How to show hidden folders in windows 7
I had such a situation that when changing the operating system, I did not know how to display hidden folders in windows 7. Previously, there was XP, and there were no special problems with this.
Seven has undergone tremendous changes that distinguished it from previous operating systems. I had to dig around to figure out the basic settings. Now I will show you several ways to open hidden folders, since in windows 7 they are not visible by default. Before starting the procedure, you can hide the folder in order to verify the results after following the recommendations. In the article, let's go over the standard, software methods and use the command line.
Standard recommendations for showing hidden folders and files in windows 7
First you need to find the window where it turns on this option, you need to do one of the following:
1. Launch Explorer (my computer), in the window that opens, click "arrange". Then select "folder and search options".

2. Click "start" and in the search type the word "settings". When the list is built, select the element shown in the screenshot below.

3. Click "start" -> "control panel". Next, make sure " large icons” or “small icons”, after which you can look for the “folder options” setting.

4. In the explorer window, press the ALT key, you will see an additional menu between the path bar and the main menu. Select Tools -> Folder Options.
After using one of the methods, a window with 3 tabs will open in front of you, go to the second one, which is called "view". Scroll down the scrollbar and check the box "show hidden files, folders and drives." Be sure to click on the APPLY button, then OK.
Note: If you need all items to be visible, make sure that the "hide protected operating system files" checkbox is unchecked.
 As you can see, displaying hidden folders in windows 7 is not difficult at all. For reliable results, go to system disk and try to find the hidden folders that have appeared and have a pale tint. There is another interesting method using the command line. To do this, launch cmd and enter the command:
As you can see, displaying hidden folders in windows 7 is not difficult at all. For reliable results, go to system disk and try to find the hidden folders that have appeared and have a pale tint. There is another interesting method using the command line. To do this, launch cmd and enter the command:
All hidden folders and files will be displayed in the current directory. If you want to change your current local disk, use the command:
cd/d local drive letter:
The example shows moving from drive C to D. To change to a directory, enter the following expression:
cd/folder name
Once you have selected the desired directory, enter the first command.

Using total commander
As is known, total commander is a tool for working with files and folders. In my opinion, much more progressive than the standard conductor. On its example, we will analyze the inclusion of hidden elements.
- Run total commander.
- From the top menu select "configuration" -> "setup".
- In the window that opens, click on "panel content".
- Check the boxes for "show hidden files" and "show system files".
Click APPLY and OK.

After the done algorithm of actions, hidden elements will be marked with a red exclamation point.
All recommendations work and will help you display hidden folders and files in windows 7. It's up to you to use one or the other. I would like to highlight standard ways and the use of total commander, as for cmd, this is rather informative information.
www.nastrojcomp.ru
Show hidden files and folders in windows 7,8.x,10

In windows 7, 8.x, 10 and Vista, important files are hidden, and to view them you need to change the folder options. Some users hide folders from other users, and in order to see them, you need to check the desired dialog box, the principle is similar in all versions, but entering the settings is slightly different.
In today's article, we'll look at how to display hidden files in windows 7, 8.x, 10, Vista.
Hidden windows files 8.x, 10
The first way: open "Explorer" => go to the "View" tab => check the box "Hidden items".

Second way: open explorer => click on "View" tab => on the right side select "Options"

Go to the "View" tab, scroll down to the bottom and check the "Show hidden files, folders and drives" box. If you want to find files in windows folder, then in this dialog box you also need to uncheck the "Hide protected operating system files" checkbox. After making changes, click "Apply".

After these steps, you will see hidden files and folders, if you want to hide them again - do this procedure again and check the box "Do not show hidden files, folders and drives."
Hidden files in windows 7
Open File Explorer => On the top left side select "Organize" => "Folder and search options"

As in others windows versions you will see a dialog box in which you need to select "View", go down to the very bottom and check the box "Show hidden files, folders and drives". If you want to find files in the windows folder, then in this dialog box you also need to uncheck "Hide protected operating system files". After making changes, click "Apply".

After these steps, you will see hidden files, and as you might have guessed, in order to no longer show hidden files, you need to check the "do not show hidden files, folders and drives" checkbox.
If something is not clear or there are additions - write comments! Good luck to you 🙂
Read also:
How to restore windows to its original state;
How to install two (or more) versions of windows;
How to add any application to the right click menu
vynesimozg.com
How to enable the display of hidden files and folders?

If you have never changed the settings of "Explorer" in windows, then you do not even know how many files on your computer that you do not see. Hidden from the eyes of an inexperienced user can be not only files, but also folders with all their contents. Basically, these are system files and folders, the removal of which will mean that windows is not working.
How to enable the display of hidden files and folders? | Video lesson
But viruses can also be masked, for the removal of which it is necessary to make hidden files and folders visible. How to show hidden folders we will consider on windows example 7. In other versions of windows, to display hidden files and folders, you must do the same steps.
And so, in order to show hidden folders in windows 7, you need to go to the "Folder Options" settings. To get to this setting, you need to go to "Start / Control Panel / Appearance and Personalization / Folder Options / Show hidden files and folders".




The "Show hidden files and folders" function is located in the "View" tab of the "Folder Options" settings. To enable the "Show hidden files, folders and drives" option, you need to scroll the list in the window to the very bottom and find the "Hidden files and folders" column. You also need to uncheck the "Hide protected operating system files" checkbox to see all available files.

By unchecking the box "Hide protected operating system files" we get a warning window.
You can get to these settings in another way. The developers of windows 7 in the "Start" menu made the "Search" column, which can make life much easier for users if you know how to use it. In the search column, you must enter the name of the function that we are looking for. Enter Folder Options. Then just click on the search result with the left mouse button to enter these settings.

And one more simple way, how to get directly from the Explorer itself to the "Folder Options" settings. In the explorer menu there is an item “Organize”, in the drop-down menu of which there is an item of interest to us “Folder and search options”.

Now let's look at an example. During windows installation 7, a whole disk of 100 MB in size is allocated for the needs of the system. At first glance, it may seem that there are absolutely no files on this disk.

After the manipulations we have performed, it is clear that this disk contains not only hidden files, but also hidden folders.

Hidden files and folders, as well as protected system files, appear in File Explorer with translucent logos. You can also set the status “hidden” for files and folders yourself if you need to hide them from the eyes of inexperienced users. To make a file hidden and, accordingly, invisible, you need to right-click on it and go to "Properties".

In the window that appears, check the box next to the "Hidden" column.

You can make a folder hidden in the same way.

If you have little experience in using a computer, and you do not know the purpose of hidden files, then it is better not to touch them and hide them away from your eyes. Deleting one such file, not any of course, can lead to the complete inoperability of windows.
Also articles on the site chajnikam.ru: How to cut mkv? How to edit avi video? Run command in windows 7 Convert to pdf format
chainnikam.ru
How to enable hidden files and folders in windows 7
Computer-Setup.Ru > windows 7
In this article, I would like to show you how to see hidden files and folders in windows 7. In windows given feature is disabled by default. The fact is that users can inadvertently change the contents of the file or even delete what is hidden, and allows the OS to work, as a result of which windows can be disrupted.
For system security purposes, this is useful, but this function is used by attackers, in writing malware that harm your computer and prevent them from being detected. But we will talk about this a little later. From this we can draw a small conclusion that the visibility of hidden files and folders has its advantages. And even more so if your computer has your hidden folder, you need to learn how to turn on the hidden folder.
There are several ways to get to the folder settings, where you can enable hidden files and folders in windows 7, let's look at them.
Enable hidden packs through my computer
Open My Computer, click on the drop-down menu Organize > Folder and search options

IN open window My Computer, press the Alt key and select Tools from the context menu and then Folder Options

In the Folder Options window that opens, select View, from the Advanced options list, go down the list, look for Hidden files and folders, check the box Show hidden files, folders and drives and click OK.

Folder settings via control panel


The Folder Options window will open, in this window you also need to go down the list, find Hidden files and folders, and check the box next to Show hidden files, folders and drives and click OK.

After doing these manipulations, hidden files and folders will be displayed on your computer.

show system files in windows 7
In order to show system files, you need to uncheck the box next to Hide protected system files (recommended) in the folder options window.
WARNING: For the stable performance of the windows 7 operating system, it makes sense to uncheck this box only for advanced users. Otherwise, you risk disrupting performance by inadvertently deleting system files or system folders.

After you try to uncheck show system files, you will immediately see a windows warning. If you still decide to see hidden system files, click YES in the warning window, otherwise NO to cancel. Then click OK.
If you have this checkbox unchecked and you see all hidden OS files, then it is recommended to check it so that windows 7 hides system files.
In contact with
classmates
www.computer-setup.com
The option that will be discussed in this article compensates for the lack of the ability to password-protect the messenger. Creating a PIN-protected dialogue is not difficult at all. How to remove hidden chat in viber? By and large, there is nothing “abstruse” here, but sometimes users get confused. We have prepared a guide to help you sort this out.
Before deleting, you need to create
To make it clearer, let's explain the principle of this function. It turns on like this:
- Android - open a conversation, swipe the screen to the left and click "Hide". iPhone is the same. Or in the chat screen, you touch the name of the contact, drag it to the left, click "Hide".
- You come up with a PIN code and enter it in a special field. If your device (iPhones, some of the Samsungs and Xiaomi) supports the Touch ID function, you can use it instead of a pin code.

- You will use the same pin code to hide the dialogs later. Before leaving the hidden chat in Viber, you do not need to do anything. It will automatically disappear every time.
2 way directly from the chat menu:


After these manipulations, the selected conversations will no longer be visible in the general list. Those who do not know about them will not be able to find anything. That is, you can add new contact and immediately classify the dialogue with him. No one will even know that some changes have taken place in your Viber.
And now we delete the chat in Viber
There are two ways to delete previously hidden conversations. The first is for cases when you need to selectively remove hidden chats in Viber. First you have to transfer these dialogs to the general list:
- We go into the hidden correspondence: enter the pin code in the search bar, after which all password-protected conversations will open in a separate list.
- Select the desired one and swipe the screen to the left.
- you press "Make visible" and enter your PIN. Then you can leave everything as it is, or delete the correspondence with this person.



The second way, which allows “demolish” the entire list of hidden dialogs at once: in the messenger settings, go to "Privacy" and select the " Hidden chats". Then click on "Reset PIN" and confirm the action.



You can also remove it in the usual way:
Option 1: Swipe left in the main chat menu, click delete;
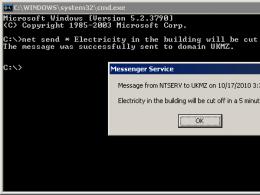
If your computer began to "slow down", and payments for electricity suddenly increased several times, you may have become a victim of hackers engaged in hidden (black) mining.
Hidden mining: how to detect and fix the problem?
To engage in the production of crypto-currencies (mining), ordinary user several things are required: computer hardware high power, the availability of special mining software, a reliable server for distributing subscriptions among members of the miner community and, of course, self-confidence. But not everything is so simple. Every day the process of mining Bitcoin is becoming more complicated, the competition between miners is growing.
Electricity costs are a topic for a separate discussion. Already today, one transaction “eats up” one and a half times more electricity than the average American family consumes per day. And according to expert forecasts, in three years the cost of producing the most popular digital currency will be comparable to the annual electricity consumption of a country like Denmark.
The tightened conditions have completely taken bitcoin miners with home computers out of the game, but they still have the opportunity to earn on alternative coins - the so-called. altcoins. For this reason, some "enterprising" programmers are looking for ways to earn digital cash using other people's computer power.
Crypto mining on someone else's hump: how hackers do it
In any kind of human activity, there are those who work honestly and those who try to profit at the expense of others. And the mining world is no exception. Someone does not pay for electricity, pulling the cable to the transformer, someone uses contraband Chinese video cards. But another way of “playing without rules” is more common - using other people's computers for mining without the knowledge of their owners.
So, in the fall of 2017, specialists from the Kaspersky Center uncovered two large-scale mining networks - for 4 thousand and 5 thousand pieces of equipment. As it turned out, the owners of infected computers had no idea about their participation in the extraction of virtual coins, but the creators of the malicious program replenished their wallets with thousands of dollars every month.
Most often, black miners take “to work” Lightcoins, Feathercoin and Monero - types of cryptocurrencies that do not require heavy-duty equipment. Therefore, the victims are mainly users of ordinary home and gaming computers.
Types of black mining
Let's consider two types of illegal cryptocurrency mining that are used by attackers.
- Hidden browser mining
Surely you know that visiting unknown Internet resources can harm your computer. This rule also applies in our case. It is enough to go to the page, in the script of which a fraudulent code is entered, and your laptop or computer will instantly become an integral part of someone's system for generating virtual coins.
Today, not only unknown sites can become a hotbed of infection, but, as it turned out not so long ago, quite respected resources. In September of this year, there was a scandal related to the official website of a large Ukrainian media holding, whose visitors became unwitting Monero miners. A similar accusation was made a little later on the well-known TV channel ShowTime (USA).
- Virus miners
The first information about virus miners dates back to 2011. Since that time, they continue to attack the equipment of ordinary users in different countries peace. You can get infected by clicking on the link from the e-mile. At risk are high-power computers, mainly gaming ones.
In general, viruses are more dangerous than browser mining, as they use power more actively. computer technology. At the same time, hundreds of thousands of users around the world become their victims.
How to check hidden mining?
The first and most obvious sign of computer infection is slowdown. If the technique works fine most of the time and starts to slow down only on one site, black miners may have entered your computer through the browser. The most dangerous in this regard are sites that require a long time spent by the user - torrent trackers, resources for computer games and watching movies. Very often, gamers with powerful processors and video cards are attacked by the virus. Another symptom of infection is a sharp increase in electricity consumption.
The main difficulty in checking for hidden mining is that antivirus programs identify it not as a virus, but as potentially dangerous software. After all, in fact, miners only steal the resources of someone else's computer, but cannot cause technical failures or breakdowns. This is also important to understand.
Virus mining programs
Let's list the main malware that users need to know about to improve the security of their equipment.
- Miner Bitcoin (trojan). As a rule, people load their computers at about 18-20% capacity, while the Bitcoin miner increases this figure to 80, and sometimes up to 100%. In addition to illegal use of resources, spyware steals personal information and can even give attackers access to your wallets. Distributed by this species Trojan mainly via Skype; it can also be picked up by downloading photos or Word documents.
- epic scale. This program discovered by uTorrent visitors. Responding to well-founded accusations, the owners of the company stated that they send the funds received in this way ... to charity. At the same time, users did not receive an explanation as to why they were “forgotten” to be informed in time about their participation in this “charity event”. It is noteworthy that it is impossible to get rid of EpicScale completely; after removal, the executable files of virus software remain on the computer. Later, a similar scandal erupted around the Pirate Bay torrent tracker.
- JS / Coin Miner. A malicious program that allows you to mine cryptocurrency through the browsers of other computers by introducing special scripts. Users of portals for online video viewing and gaming sites are at particular risk. Such sites load the processor, so in most cases JS/CoinMiner goes unnoticed. To detect a fraudulent script, you need to check if it is in the list of miner scripts.
How to block hidden browser mining
To date, there are several effective ways to protect against attacks by black miners on the browser:
- Edit the hosts file.
- Install the NoCoin browser extension and the Anti-Web Miner utility.
- Disable in your JavaScript browser using No Script.
- Add uBlock and AdBlock anti-mining.
But if everything is clear enough with JavaScript and utilities, then the hosts edition needs more detailed consideration. Below we provide instructions on how to do this:

After these simple steps, your browser will receive reliable protection against infection.
Protection against hidden virus mining: precautions
Basic protection rules: do not follow dubious links, do not download products that do not have a license; do not activate keys from obscure sources.
And now a few more important rules for safe work with a computer:
- It is not enough just to install an antivirus, you need to systematically update it.
- Create yourself account in Windows and log in through it daily. Since you need administrator rights to install any programs, the risk of accidentally downloading and running a malicious program will be eliminated.
- For equipment from the company Apple the best the solution would be to install a feature that allows downloading software only from the AppStore.
- At the first sign of a slowdown, launch the "task manager" and check if there is a program on your computer that uses it to the limit of its power (80-100%). Even if you do not find it, do not rush to calm down, because there are viruses that use less power.
- Install special utilities, which provide virus protection and report updates to the registry. The best option is to install Request Policy Continued and uMatrix at the same time, and for those who use Google Chrome, in addition to them, the Antiminer blocker.
If you are unable to find the dangerous program yourself, you can reinstall Windows, run another antivirus, or seek help from a professional programmer.
- News collections once a day to you by Email:
- Collections of crypto news 1 time per day in Telegram: BitExpert
- Insides, discussion forecasts important topics in our Telegram chat: BitExpert Chat
- The entire cryptocurrency news feed of the BitExpert magazine is in your Telegram: BitExpert LIVE
Found a mistake in the text? Select it and press CTRL+ENTER
31.05.2018
Over time, you may notice that your computer / laptop has become slower, one of the reasons for this may be the installation a large number programs. The fact is that programs can take up a lot of space on the C drive, due to lack of space, the computer / laptop starts to slow down, of course, you can expand C drive but why keep something you don't use. Plus, programs can use RAM (if they are registered in startup). The most optimal in this case, I see the regular removal of unused programs. As you probably guessed, this article will be for beginners and it will be devoted to uninstalling programs in Windows 7, Windows XP, Windows 8.
Unfortunately, to use these software keyloggers it doesn't matter much. Just set them up at the first start, and then, if you want, you can also create a gadget that will allow you to control over the Internet all the tasks that will be performed on the computer where the keylogger was installed. In addition to being installed on purpose, the keylogger software can be located on a specific computer, also exploiting rogue browser vulnerabilities, simply browsing special sites specially designed, as well as opening regular e-mail messages containing suitably modified attachments that can be even equipped with a double extension.
I will consider uninstalling programs in various versions Windows:
Uninstalling programs in Windows XP.
In order to uninstall the program in Windows XP, you must click the "Start" button - "Control Panel"
Select "Add or Remove Programs".

One of the silent threats to our computers are rootkits. There is a special ghost software that, through the use of programming techniques, makes it invisible to the user, device, operating system, as well as major anti-virus, anti-spyware and antivirus programs. Rootkits should not be underestimated. They are the most harmful to the PC as they facilitate hacker attacks by granting remote administrator rights.
The purpose of this malware software is to hide intruders from computer hackers to damage computers connected to the network. The goal is to hide any backdoor or other pirated software from the system administrator.
A window with a list of programs will open. In fact, you can get here in an easier way, just press the key combination "Win" + "R" and enter the command appwiz.cpl, press Enter.

Select the program you want to remove, click on it and select "Uninstall".
If you want to check for rootkits running on your computer, generic antivirus software is not enough. Search the web if you find more than one, both paid and free. This program performs the task of scanning, detecting and removing hidden rootkits on your computer using advanced technologies detection.
It is recommended to view hidden folders and files and protected system files. Most likely, rootkits will be found in these folders and strange names will be known. When you restart your computer, you will immediately notice the difference as it will display faster.

Thus, you can easily uninstall the program in Windows XP.
Uninstalling programs in Windows 7.
In order to uninstall the program in Windows 7, you must click "Start" - "Control Panel".

Select "Programs and Features".
If you have problems installing it, it may mean that your computer is not in good shape and is probably infected with a rootkit. The interface of the program is not immediate, but it works well. At this point, the user must intervene: if you are not sure what you are going to do, you must leave the pending operation and ask for help. However, before embarking on any initiative, it is necessary to document the document. An interpretation error can damage legitimate applications or the operating system.

Another way to press the key combination "Win" + "R" and enter the command appwiz.cpl

No matter which method you used, a window is open in front of you, in which a list of all installed applications. In order to remove any program, click on it and select the "Delete" button from above, or right-click on it and in context menu click "Delete".
A very unpleasant inconvenience that also risks limiting work. In fact, with only a few gigabytes, this is a problem for all devices. Especially those that mount a small HDD. This is a disk that serves to store data, including system files that allow the computer to start and recognize many connected peripherals. Documents, images and videos are stored on disks. They also host apps and more. Some of these files are useless for PC operation and can be safely deleted.

Start the process of uninstalling the program, you just have to agree with it, after which the program will be deleted.
Uninstalling programs in Windows 8/ 8.1
Uninstalling programs in Windows 8/8.1 has not changed much compared to previous versions. The only button "Start" disappeared or lost its former functionality. But you can do without it, to do this, press the key combination "Win" + "R" and enter the command appwiz.cpl then press the key Enter.
How to remove old drivers
In particular, there are two categories of data that, once deleted, will allow you to recover a lot of space: older versions of updated drivers and devices that are no longer used on your computer. On the way to you, you probably heard about the return back. This is very useful feature, which allows you to return in case of problems with the new version of the operating system. Likewise, when the system updates drivers for various devices, it retains the memory of the previous ones. The problem is that these files take up a lot of space.

For those for whom this caused some problems, you can use the more traditional method.
For Windows 8
Hover your mouse over the lower left corner until the Start window appears, right-click on it and select "Programs and Features".

If you have not found any failures on your computer, there is no need to have them in memory. Removing old drivers is very easy. The computer will analyze the files, which you can delete. If you have different partitions, before continuing, select the one where you want to recover space. When the process is complete, click "Cleanup system file". Your computer will start looking over which files you can delete again. At this point, to uninstall previous versions of drivers, simply select "Device Driver Packages" and click "OK".
For Windows 8.1
Right-click on "Start" and select "Programs and Features".

As a result, you will have a list of all installed programs, in order to remove the program, right-click on it and select "Delete" in the context menu or by clicking on the program at the top of the window, click the "Delete" button.
How to Erase Old Device Drivers
It often happens that you install a device and not drivers on your computer as soon as you no longer use it. And when there are different devices, it's hard to find the files and delete them. Even in this case, the procedure is very simple. Without clicking the "Submit" button, right-click " Command line" and then "Run as administrator". Now all old hidden drivers will be visible. All you have to do is enter "Device Manager" and remove all inactive devices. You recognize them because, compared to others, they are "transparent".

As a result, the process of uninstalling the program will start.
Uninstall the program with Revo Uninstaller.
Revo Uninstaller is considered to be one of the best tool for uninstalling programs in Windows, especially useful if you need to remove what is standard Windows tools not removed or not removed completely. This program is suitable for any operating Windows systems(Windows 7, Windows XP, Windows 8).
Locate the device, right-click and select Uninstall. However, be careful not to uninstall active device drivers. This article applies to everyone who moves to the Internet. Everyone who uses the Internet is aware or not aware of some sort of unwanted interest.
Most of these actions are hidden, so when you connect to the Internet, this information from your computer is sent without your knowledge. From what can be stolen, it is obvious that the consequences can be much more serious. To collect this information they use a spy of various methods.
First of all, it is necessary download Revo Uninstaller . The program is available in two paid versions ( trial period 30 days) and free. IN this example used the free version of the program.
Installing the program comes down to a few clicks of the "Continue" button. As a result, you will see a window with the applications you have installed. Select the one you want to delete and click the "Delete" button.
![]()
Confirm your choice.

After that, you will be asked to select the uninstall mode, since we started using a third-party solution for uninstalling programs, we need to squeeze the maximum out of it, so we select "Advanced".
Bring it to life and find a place for it that will keep you more solid with your privacy. We are used to being able to accept various types of threats in the form of viruses, Trojans, spyware. For unknown reasons, we are forgetting about another very serious danger of rootkits. What are they and how can we fight them?
The concept of a rootkit is something completely foreign to the vast majority of computer users. It is this lack of awareness that poses a serious threat to users and operating systems. Generally speaking, this is a kind of technique that allows you to very clever and effective camouflage of all kinds of malware, files and processes. Worse, detecting such a component is indeed very difficult - even for the best and most up-to-date antivirus programs. There are several types of rootkits that are characterized by a slightly different way of functioning or the destination in which they nest. Some of these malicious applications can only survive until we decide to reboot the system. Others even go as far as the core, changing the way different applications work. How to remove rootkits? Removing such things from the system is not easy. IN otherwise we can use special tools. For many people, it may be important that it offers the ability to detect rootkits using GUI. Before using this application, disable all running applications. After downloading and running the program, click the "Scan" button, and then leave the computer until the process is completed. Scanning may take a long time. In addition, you should expect a very large load on the available hardware resources. Therefore, we can forget that when using this tool, we will be able to browse the Internet. When completed, a list of suspicious items will be displayed. Each of them will contain detailed information about location, size and description. However, it is important to remember that, like any similar application, it returns suspicious results and does not explicitly indicate that it is a malicious application. The distribution is based on a "free" license, so it won't blow your budget. This program handles all hidden items such as processes, files, and registry entries. It also checks the modules corresponding, for example, to controlling the operation of various devices. The name of the program is randomly generated - this prevents possible blocking of malicious programs that may be present on our system. The program allows you to scan the drive for files, folders and processes that are hidden from you.
- What is a rootkit?
- The strength of rootkits lies in the fact that they work almost silently.
- The average user cannot even notice that something is wrong with their system.

After that, the standard uninstallation of the program will start, click "Next" ... At the next step, the registry cleaning window will appear in Revo Uninstaller, select all "Select all" and click "Next".

Confirm your choice.
We are constantly working on creating best tools security to protect people using our services. However, we often hear about people who lose access to their personal accounts as a result of fraud. Once they have access to a person's account, scammers can use their account to contact their friends or family members and trick them into asking for a quick loan, for example. We use automatic and manual systems, which we constantly update to detect and block suspicious activity.

At the end, click "Finish".

So you will remove everything unnecessary programs, freeing up disk space and making your computer/laptop work faster.
For Windows 7, there are thousands of programs with a variety of functions. Choosing the right app the first time around is not easy, so many users usually install several programs with similar features at once in order to try each of them and decide on the best option. But what about the rest of the applications that are no longer needed? We will tell you how to uninstall a program from Windows 7 in this article.
Removal by means of the program itself
Some programs, during installation, create a separate folder in the Start menu, which contains not only a shortcut for launching, but also a link to uninstall the program. To use this link, open the Start menu, go to All Programs, find the folder for the application you want to uninstall, and see if there is an "Uninstall [app name]" or "Uninstall [app name]" link. If there is - click this link and follow the instructions of the removal wizard.
Removal by means of the operating system
Not all applications have separate uninstall links, so the easiest way to uninstall a program in Windows 7 is to use the mechanisms built into the program itself. operating system. To do this, open the Start menu and select Control Panel. In the Control Panel, find the "Programs" section and click the "Uninstall a program" link.
The Programs and Features window opens. Highlight the application you want to remove and click the Remove button that appears. In some cases, this will be the Uninstall / Change button, and then in the wizard window that opens, you will need to specify what you want to do - reinstall the program or delete it. Choose the option you want and follow the wizard's prompts.
Removing with CCleaner
There is also a useful CCleaner program that allows you to keep the operating system clean and tidy, remove unnecessary temporary files and clean the registry. It also has a function to remove programs, and sometimes with using CCleaner you can even get rid of applications that are not deleted through standard remedy"Programs and Features".
Download free version CCleaner from the official site. Launch the application and go to the "Service" section, and in it - to the "Uninstall programs" item. Select the program you want to uninstall and click the "Uninstall" button, and then follow the wizard. There is also a "Delete" button - it removes information about the program from Windows Registry and can be useful if removal by conventional means fails.